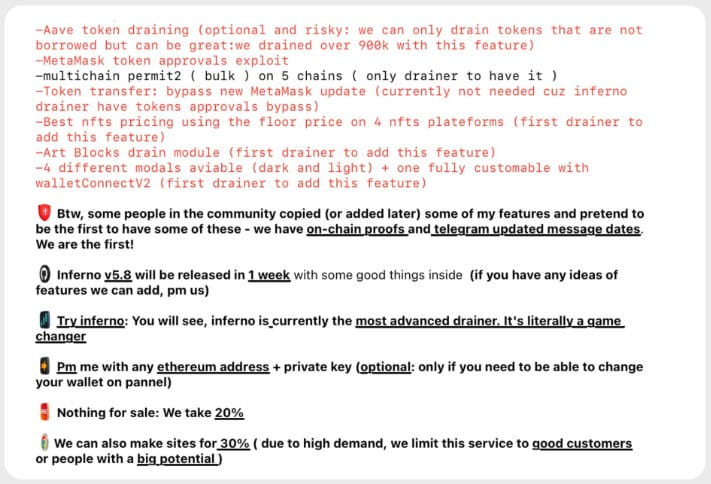
A cryptocurrency phishing and scam service called ‘Inferno Drainer’ has reportedly stolen over $5.9 million worth of crypto from 4,888 victims.
According to a report by the Web3Anti-Scam firm ‘Scam Sniffer,’ the phishing service has created at least 689 fake websites since March 27, 2023.
Most of the phishing sites came online after May 14, 2023, with the analysts reporting a spike in site-building activity around that time.
The malicious websites created with Inferno Drainer target 229 popular brands, including Pepe, Bob, MetaMask, OpenSea, Collab.Land, LayerZero, and others.

Scam Sniffer discovered the service after observing an Inferno Drainer member promoting the service on Telegram by posting a screenshot of a $103,000 theft demonstrating their capabilities.
“By querying the transaction hash obscured in the screenshot, we found this transaction in ScamSniffer’s database and associated it with some known malicious addresses in our malicious address database,” explains Scam Sniffer.
Inferno Drainer promotes multichain fraud, Aave token and Art Blocks draining, MetaMask token approval exploits, and more.
The authors of the “drainer” toolkit provide a modern admin panel with customization options and even offer a trial for interested buyers.
Operators pay Inferno Drainer 20% of their proceeds, while the cut goes up to 30% for services that include the creation of phishing sites.
However, due to high demand, the service will only offer phishing sites to “good customers” or clients who have proven their potential to generate much money.
Scam stats
Scam Sniffer has investigated the operation of Inferno Drainer and found that the service has been active since February 2023 and increased its operational volume starting from mid-April 2023.
Most assets ($4.3M) were stolen from the Mainnet, $790k were snatched from Arbitrum, $410k from Polygon, and $390k from BNB, totaling $5.9 million.
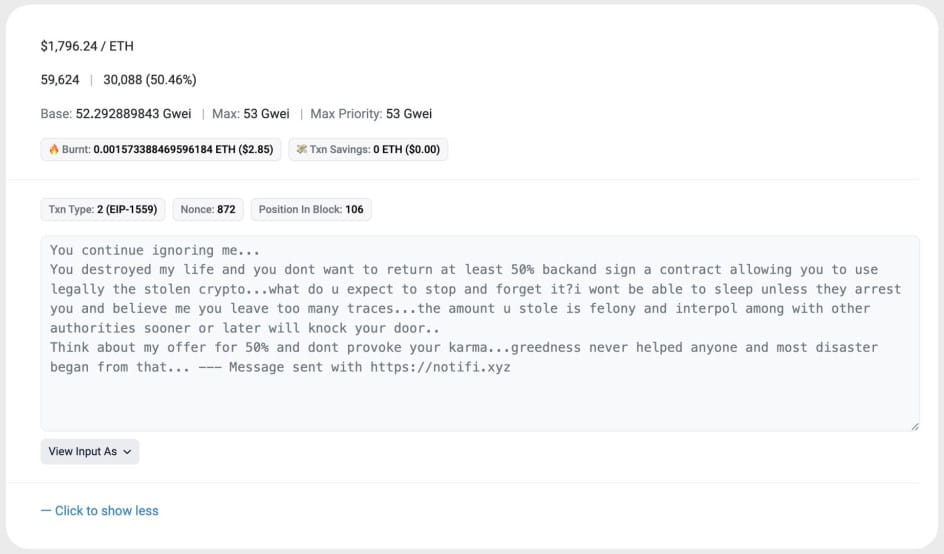
One of the largest victims identified by the analysts lost $400,000 worth of assets. The victim contacted the attackers and offered them 50% of the amount to not legally prosecute them, but the perpetrators ignored those messages.
Scam Sniffer says the threat actors distribute the funds they collect from attack fees among five cryptocurrency addresses currently holding between 250 and 400 ETH.
Cryptocurrency holders should practice vigilance in all transactions, treat incoming messages with skepticism, verify the sender’s identity, use multi-factor authentication to protect their accounts, and keep their software up to date.
Ideally, do not disclose any personal information online, and use hardware “cold” wallets to store most of your digital assets.
