The Cuba ransomware gang has claimed responsibility for this month’s cyberattack on The Philadelphia Inquirer, which temporarily disrupted the newspaper’s distribution and disrupted some business operations.
The Philadelphia Inquirer is Philadelphia’s largest (by circulation) newspaper. It is the third-longest continuously operating daily newspaper in the U.S., founded in 1829, and it has won 20 Pulitzer Prizes for its journalistic excellence.
On May 14th, The Inquirer disclosed that it had suffered a cyberattack that forced its IT team to take computer systems offline to prevent the attack’s spread. Additionally, the newspaper contracted forensics experts from Kroll to investigate the “anomalous activity.”
The attack disrupted the publication of the Sunday print newspaper, so home-delivery subscribers received an early edition composed on Friday and were invited to catch up with the latest news on the newspaper’s website (inquirer.com), which remained unaffected.
“The Inquirer publication disruption is the most significant the company has faced since the blizzard of Jan. 7-8, 1996, and comes just days from the primary for the 100th mayoral election in Philadelphia,” described the relevant article on the newspaper’s online portal.
At the time, a spokesperson for the newspaper did not clarify if the attack was ransomware and kindly requested patience until the ongoing investigation completes.
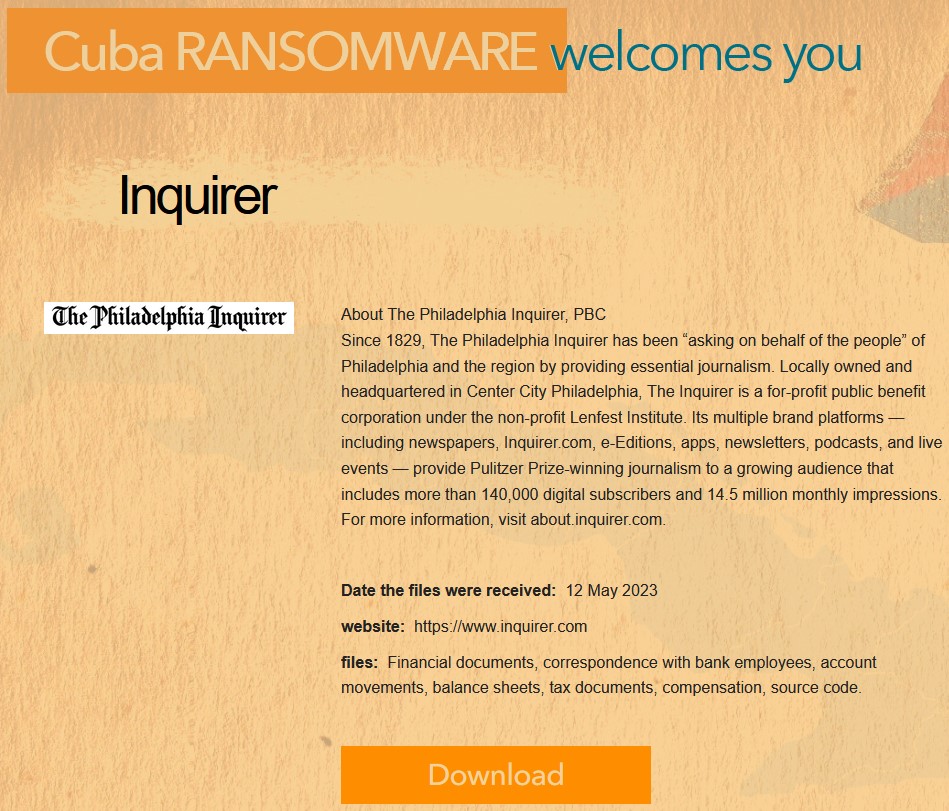
However, today, the cyberattack was claimed by the Cuba ransomware gang in a post on their extortion site, declaring that they stole files from the newspaper’s computers on May 12th, 2023.
The stolen data, now publicly released on Cuba’s extortion portal, includes financial documents, correspondence with bank employees, account movements, balance sheets, tax documents, compensation, and source code.
Source: BleepingComputer
The fact that all stolen files were made available for free indicates that the newspaper has refused to pay a ransom, so the extortion process reached a dead end.
BleepingComputer has contacted The Philadelphia Inquirer to ask about the status of its systems and whether customer data might have been stolen from its networks, but a comment wasn’t available by publication.
The Cuba ransomware gang remains a low-volume but still active group that the FBI reported made $60 million from 100 attacks as of August 2022.
The ransomware gang was also linked to attacks on Ukrainian government agencies after phishing emails delivered the “ROMCOM RAT” malware, a remote access trojan associated with a known Cuba ransomware affiliate.
A January 2023 Microsoft report shared that the Cuba ransomware members also exploited Microsoft Exchange vulnerabilities for initial access to corporate networks.
