The hacking group ALPHV/BlackCat has resurfaced, once again targeting healthcare companies and threatening to report them to the U.S. Department of Health and Human Services (HHS). This government agency, responsible for advancing the well-being of all Americans, now finds itself at the center of a cybersecurity storm.
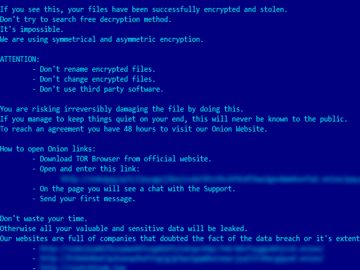
Visitors to the BrightStar Care website were met with a chilling message indicating a security breach: “Sorry, you have been blocked. You are unable to access brightstarcare.com.”
Cyberattack on BrightStar Care
Further investigation revealed that the website was utilizing a security service to protect itself from online attacks, triggered by unspecified actions, possibly a certain word or phrase, a SQL command, or malformed data.
The website also instructed affected users to contact the site owner, providing details of the incident.

In an attempt to delve deeper into the matter and verify the cyberattack, The Cyber Express Team reached out to the officials. However, as of the time of writing this report, no response has been received from the targeted healthcare companies.
Adding fuel to the fire, according to the tweets, BlackCat openly declared their intention to report the targeted healthcare companies to the HHS. This marks a repeat of their aggressive approach seen in December when the BlackCat filed a complaint with the U.S. Securities and Exchange Commission (SEC) against MeridianLink, accusing the California-based company of not adhering to a four-day rule for disclosing a cyberattack.
BlackCat Previous Encounter with the SEC and FBI
In a strategic move viewed by experts as a form of triple extortion, BlackCat’s December complaint with the SEC showcased a new frontier in cybercrime—publicly reporting a cyberattack to a regulatory body. The group accused MeridianLink of withholding information about a cybersecurity incident that compromised customer data and operational details.
In a bizarre turn of events, just hours after the FBI seized control of the ALPHV/BlackCat threat group’s website, the hackers defiantly reestablished control and issued a menacing message directed at the FBI. The dark web post detailed the repercussions of the takedown, revealing specific information about the exposed data to the FBI.
BlackCat asserted its control by stating that the FBI only had access to a limited number of keys, leaving more than 3000 companies without access to their decryption keys. The post outlined new rules, removing all constraints except one—no interference with the Critical Infrastructure Sectors (CIS). The hackers declared that hospitals, nuclear power plants, and other critical systems were fair game for disruption.
This audacious move by BlackCat, deviating from their usual covert operations and ransom demands, raises questions about the motivations and evolving strategies of cybercriminal groups. Is this a sign of desperation, an attempt to exert more pressure for ransom, or an innovative tactic to manipulate regulations for their illicit gains?
As the cybersecurity landscape continues to evolve, these incidents emphasize the need for enhanced vigilance and collaboration between authorities, businesses, and cybersecurity experts to mitigate the ever-growing threat posed by sophisticated hacking groups.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.