There are many avenues of attack that a threat actor can take. One that has been increasing in recent years is user-centric applications. Instead of focusing on a more highly-protected administrator account, attackers target applications or extensions that a user can easily install without IT involvement.
One example is the proliferation of extensions, such as those in Chromium-based browsers. Though not the first of its kind, a recent example is the Rilide malware strain. Trustwave identified this malware, which disguised itself as a Google Drive extension.
After installation, the extension enabled threat actors to monitor browser history, take screenshots, and inject malicious scripts that targeted cryptocurrency exchanges.
Also, cybersecurity giant, Kaspersky, recently identified 34 malicious Chrome extensions with over 87 million downloads. Multiple malicious extensions target user installations, leading to a real danger of data exfiltration and system compromise.
The Danger of Unchecked User Control
A significant shift occurred years ago when users transitioned from primarily running as administrators to running with least privileges. This change reduced the attack surface that malicious applications or attacks could exploit. In the event of an attack, the damage may be limited to that user’s profile and the data they could access.
Although a compromised user account can lead to a compromised administrative account, separating the two provides significantly enhanced security. But, because users felt relatively safe with this separation and may feel annoyed about asking IT to install software, there has been a proliferation of user applications and extensions.
Examples include extensions in Chromium-based browsers or development tools like Visual Studio Code. Users may need to scrutinize the installation process more closely since these extensions are downloaded from traditionally trusted sources, such as Google and Microsoft’s Visual Studio Code extension repository.
Due to this lack of attention, more and more attacks are occurring via extensions or user-profile installations of tools. Other examples include supply-side attacks from PyPi packages or malicious NPM package installations.
Previously legitimate extensions or packages may be sold to an unscrupulous group that allows a user to be silently compromised from a formerly trusted source.
Preventing Damaging User-Profile Extensions and Packages
What can an IT department and a user do to protect themselves? One approach is to vet extensions and packages and use allow-lists to proactively limit what a user can install. This way, both users and administrators can feel safer, and it ensures that only safe packages are used.
IT administrators should monitor extensions and packages that are allowed for changes in ownership and files that may signal danger, especially if done by a third party. Since an extension may attempt to read data that a user profile can see, including files, it is especially important for users who have stored a password in a file to exercise caution.
This underscores the importance of Multi-Factor Authentication (MFA) in preventing further breaches, as a password alone would not be enough to access a sensitive system.
Of course, in the event of an attack, it is crucial to quickly clean and reset a user’s account. The user-profile attack can leverage data contained within, which means that crafted phishing emails or emails sent from a legitimate user’s account could be used to further propagate an attack.
Mitigating Attacks with Specops uReset
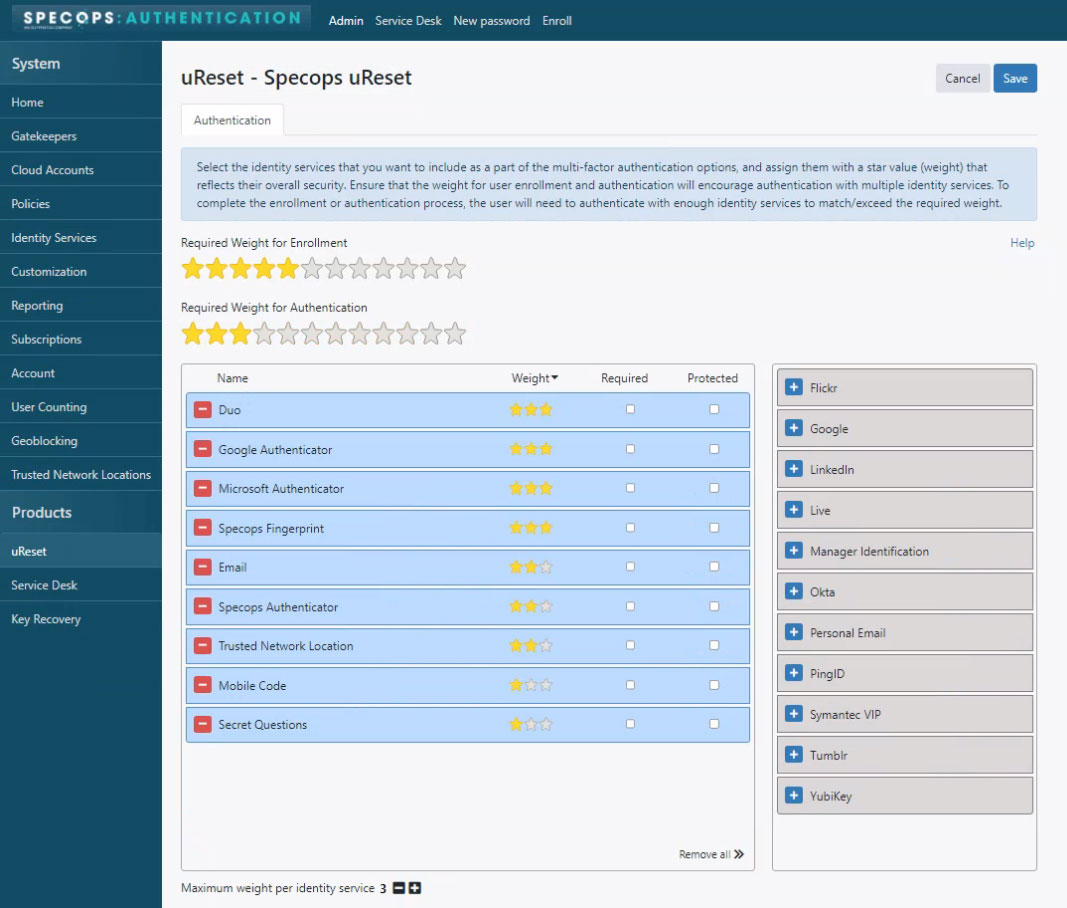
Using tools like Specops uReset, which leverages multiple weighted factors to ensure that only the correct user can reset a password, provides a secure and fast method for a helpdesk to quickly take control of a bad situation.
- Reset passwords from a web browser, the Windows logon screen, or a mobile app.
- Enhance the helpdesk with a specific interface for verifying users, unlocking accounts, and creating a temporary passwords.
- In-depth auditing and reporting on authentication events.
- Multiple identify services such as SMS, Email, Fingerprint Readers, Trusted Network Locations, Manager Verification, Dua, Okta, Symantec VIP, Microsoft & Google Authenticator, Google, Facebook, Twitter, Twitter, and more.
User-Profile Dangers and Mitigations
Although there has been a shift from prolific administrator accounts to limited user accounts, an evolving threat exists from applications that users can install themselves. These applications can range from extensions to packages that can auto-update and appear legitimate.
Therefore, it is crucial for IT organizations to proactively control what can be installed and used by their users.
In the event of an attack, it is crucial for an organization to quickly verify the identity of the user and reset their credentials using tools such as Specops uReset. By doing so, the attack can be stopped in its tracks, and the user’s account and system can be quickly cleaned to prevent any future issues.
Sponsored and written by Specops Software