Cybercriminals are orchestrating sophisticated attacks against trucking and freight companies in elaborate schemes designed to steal cargo shipments worth millions.
These threat actors are exploiting the digital transformation of the logistics industry, compromising transportation companies to fraudulently bid on legitimate cargo loads before stealing and reselling the goods.
At the center of these operations is the deployment of remote monitoring and management (RMM) tools, which have become the weapon of choice for modern cargo thieves looking to infiltrate supply chain networks.
Cargo theft represents a staggering $34 billion annual loss to businesses, according to the National Insurance Crime Bureau.
While cargo theft has plagued the transportation industry for decades—from Old West train robberies to 1960s mobster operations—the criminal enterprise has evolved significantly in the digital age.
Today’s cybercriminals exploit the same technology platforms that companies rely on to move freight efficiently, turning digital tools into vehicles for theft.
The problem extends far beyond North American borders. Munich RE identifies global cargo theft hotspots including Brazil, Mexico, India, the United States, Germany, Chile, and South Africa, with food and beverage products ranking among the most frequently targeted commodities.
The digitization of supply chains has created unprecedented vulnerabilities that organized crime groups exploit using increasingly sophisticated cyber capabilities.
As IMC Logistics testimony to Congress explains, these groups can now steal freight remotely by exploiting gaps in the technology embedded throughout supply chains.
Cyber-enabled theft has become one of the most prevalent forms of cargo crime, relying heavily on social engineering tactics and insider knowledge of trucking industry operations.
The COVID-19 pandemic accelerated this trend, with organized retail theft skyrocketing to levels that prompted Congressional legislation aimed at combating the growing crisis.
How the Attack Chain Works
Cybersecurity researchers at Proofpoint have been tracking a cluster of criminal activity specifically targeting trucking carriers and freight brokers since at least June 2025, though evidence suggests operations may have begun as early as January.
The attack methodology follows a consistent pattern: threat actors first compromise accounts on broker load boards—online marketplaces where companies post and book freight shipments. Using these compromised credentials, criminals post fraudulent freight listings and initiate contact with carriers who respond to the fake loads.
The attackers employ three primary delivery tactics to infect victims with RMM tools. First, they exploit compromised load board accounts to send malicious URLs to carriers inquiring about posted shipments, leveraging the trust and urgency inherent in freight negotiations.
Second, they hijack existing email threads using compromised accounts to inject malicious content into ongoing business conversations.
Third, they launch direct email campaigns against larger logistics entities, including asset-based carriers, freight brokers, and integrated supply chain providers.
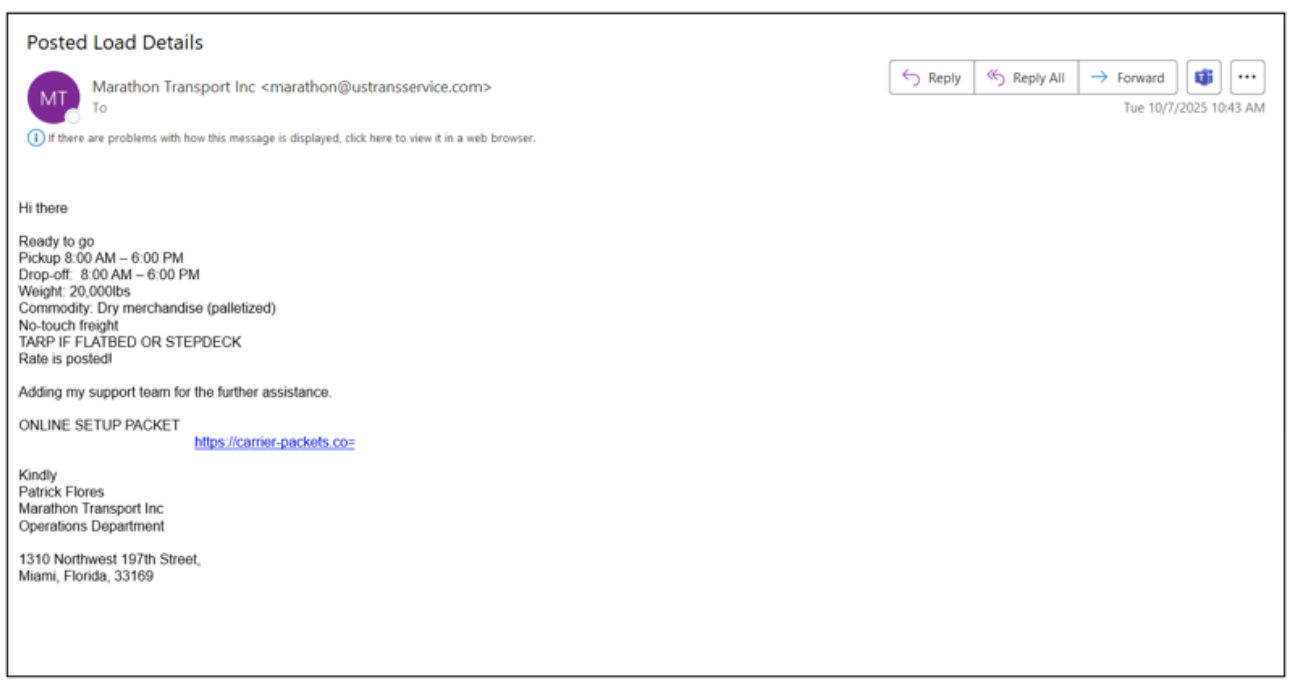
These malicious emails typically contain URLs leading to executable files that, when clicked, install RMM software granting attackers complete control over the victim’s systems.
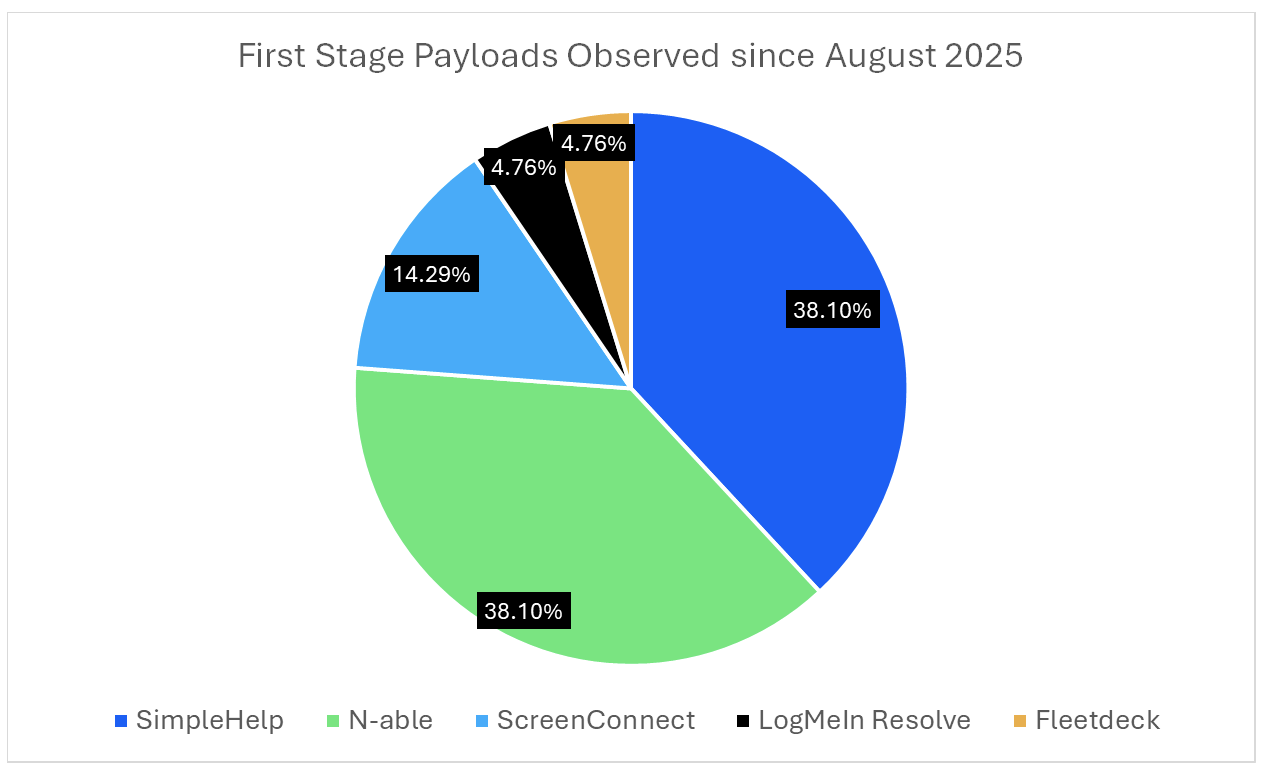
Researchers have identified numerous RMM tools deployed in these campaigns, including ScreenConnect, SimpleHelp, PDQ Connect, Fleetdeck, N-able, and LogMeIn Resolve.
In many cases, multiple RMM tools are deployed simultaneously—for instance, PDQ Connect has been observed downloading and installing both ScreenConnect and SimpleHelp on compromised machines.
Once initial access is established, the attackers conduct thorough reconnaissance of victim networks and deploy credential harvesting tools like WebBrowserPassView to steal login information and expand their access.
This enables them to identify valuable shipments and use their fraudulent access to bid on real cargo loads, which they then steal and sell through online channels or ship overseas.
Scope and Impact of RMM-Based Cargo Theft
Proofpoint has documented nearly two dozen campaigns in just the past two months, with attack volumes ranging from fewer than 10 messages to over 1,000 messages per campaign.

The threat actors appear opportunistic rather than selective, targeting organizations ranging from small family-owned trucking businesses to large integrated transport firms. Any carrier responding to a fraudulent load posting becomes a potential victim.
Public reports corroborate the widespread nature of these attacks. One Reddit post described an attack where criminals compromised a company through RMM delivery, deleted existing bookings, blocked dispatcher notifications, added attacker-controlled devices to phone extensions, booked loads under the victim’s name, and coordinated the actual transport to steal the cargo.
Typically, emails contain URLs that lead to an executable (.exe) or an MSI (.msi) file. When clicked, these files install an RMM tool, granting the threat actor full control of the compromised machine.
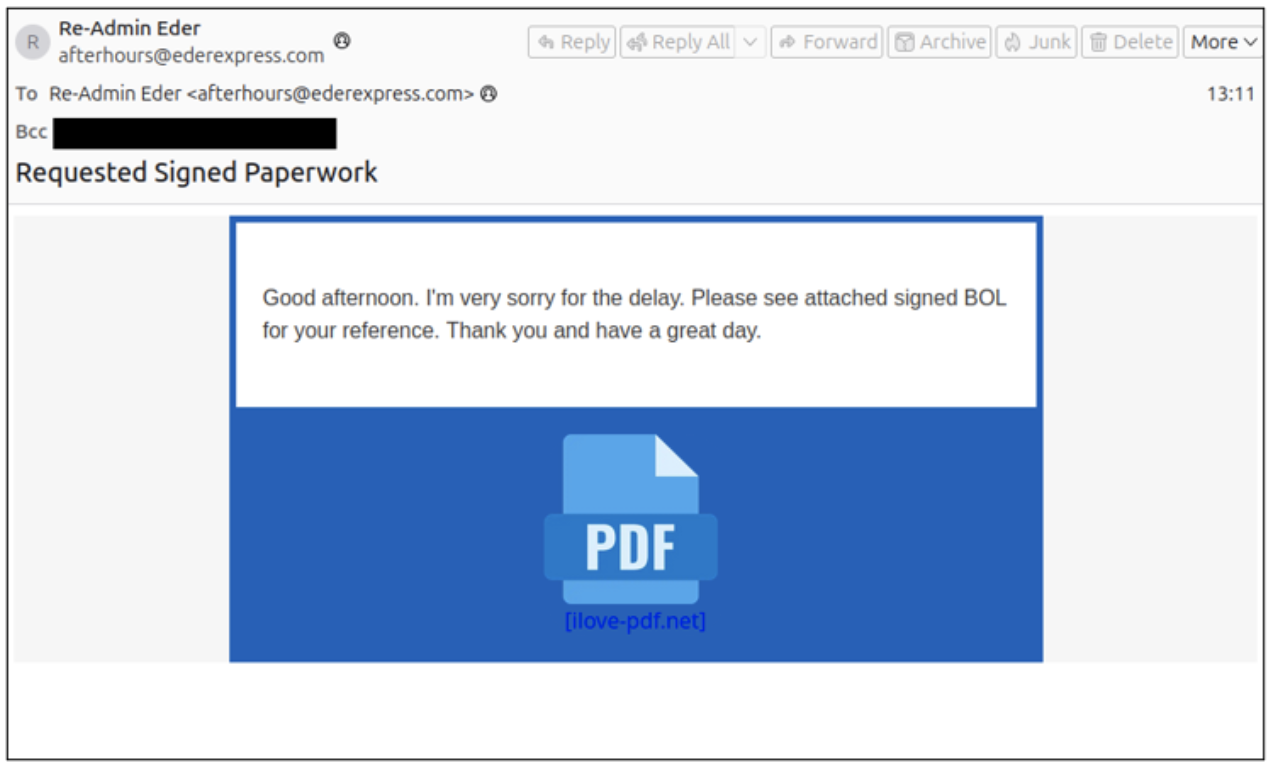

The initial compromise came through a malicious link closely matching URLs researchers observed in active campaigns.
The use of RMM tools provides significant tactical advantages for cargo thieves. Because RMM software serves legitimate business purposes, victims often exhibit less suspicion when installing these tools compared to obvious malware.
Additionally, RMM installers are frequently signed and distributed as legitimate software, allowing them to evade antivirus detection and network security controls more effectively than traditional remote access trojans.
This shift toward RMM-based attacks reflects a broader trend across the cybercrime landscape, where threat actors increasingly adopt these tools as first-stage payloads.
Cyber-Enabled Cargo Theft
The National Insurance Crime Bureau reports that cargo theft losses increased 27 percent in 2024, with projections indicating another 22 percent increase expected in 2025.
As cybercriminals continue targeting surface transportation entities to steal physical goods, organizations must implement robust cybersecurity measures tailored to this specific threat.
The National Motor Freight Traffic Association has published a Cargo Crime Reduction Framework specifically designed for organizations in the surface transportation industry.
Key defensive measures include restricting the download and installation of any unapproved RMM tools, implementing network detection systems with Emerging Threats rulesets to alert on RMM server communications, and deploying endpoint protection solutions.
Organizations should prohibit downloading executable files delivered via email from external senders and train employees to identify and report suspicious activity to security teams.
Given the continued growth of this threat activity between 2024 and 2025, security experts assess that cyber-enabled cargo theft will continue increasing in both scope and sophistication.
Organizations throughout the supply chain must remain vigilant against these evolving tactics to protect their operations and cargo from this profitable criminal enterprise.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



