The collapse of the Silicon Valley Bank (SVB) on March 10, 2023, has sent ripples of turbulence throughout the global financial system, but for hackers, scammers, and phishing campaigns, it’s becoming an excellent opportunity.
As multiple security researchers report, threat actors are already registering suspicious domains, conducting phishing pages, and gearing up for business email compromise (BEC) attacks.
These campaigns aim to steal money, steal account data, or infect targets with malware.
SVB going defunct
SVB was a U.S.-based commercial bank, the 16th largest in the country, and the largest bank by deposits in Silicon Valley, California.
On March 10, 2023, the bank failed after a run on its deposits. This failure was the largest of any bank since the 2007-2008 financial crisis and the second-largest in U.S. history.
This event has impacted many businesses and people in the technology, life science, healthcare, private equity, venture capital, and premium wine industries who were customers of SVB.
The chaotic situation is further worsened by the prevailing elements of urgency, uncertainty, and the significant amounts of money deposited at the bank.
Scammers jump at the opportunity
Security researcher Johannes Ulrich reported yesterday that threat actors are jumping at the opportunity, registering suspicious domains related to SVB that are very likely to be used in attacks.
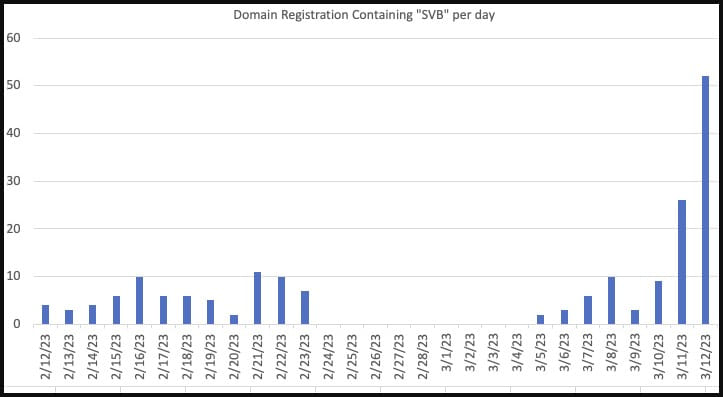
Some of the examples given in a report published on the SANS ISC website include:
- login-svb[.]com
- svbbailout[.]com
- svbcertificates[.]com
- svbclaim[.]com
- svbcollapse[.]com
- svbdeposits[.]com
- svbhelp[.]com
- svblawsuit[.]com
Ulrich warned that the scammers might attempt to contact former clients of SVB to offer them a support package, legal services, loans, or other fake services relating to the bank’s collapse.
An attack already seen in the wild is from BEC threat actors who are impersonating SVB customers and telling customers that they need payments sent to a new bank account after the bank’s collapse.
However, these bank accounts belong to the threat actors, who steal payments meant to go to the legitimate company.
Cyber-intelligence firm Cyble published a similar report today exploring developing SVB-themed threats, warning about these additional domains:
- svbdebt[.]com
- svbclaims[.]net
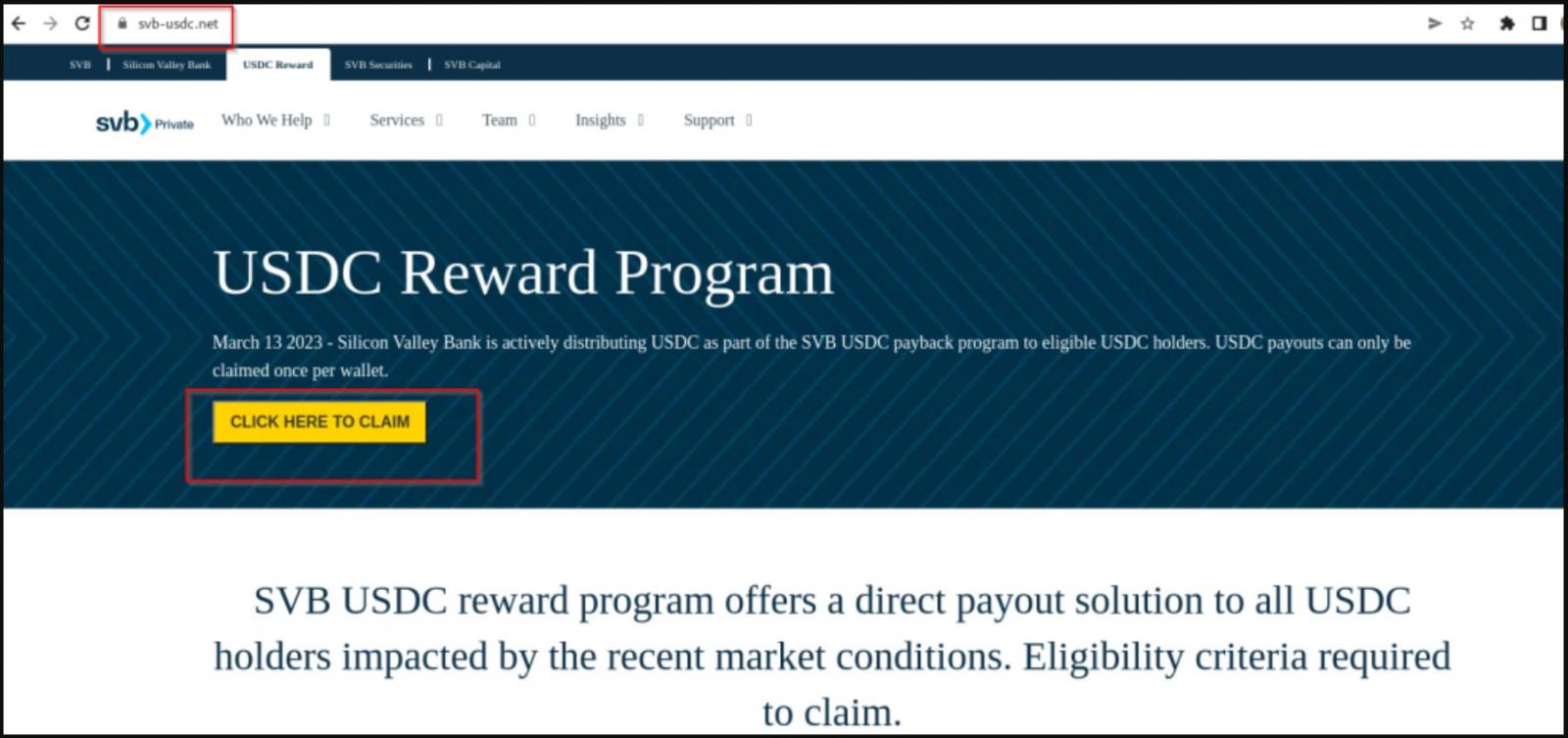
- svb-usdc[.]com
- svb-usdc[.]net
- svbi[.]io
- banksvb[.]com
- svbank[.]com
- svblogin[.]com
Many of these sites were registered on the day of the bank’s collapse, March 10, 2023, and are already hosting cryptocurrency scams.
These scam pages tell SVB customers that the bank is distributing USDC as part of a “payback” program.
“March 13 2023 – Silicon Valley Bank is actively distributing USDC as part of the SVB USDC payback program to eligible USDC holders. USDC payouts can only be claimed once per wallet,” claims the cryptocurrency scam.
However, clicking on the site’s ‘Click here to claim’ button brings up a QR code that attempts to compromise Metamask, Exodus, and the Trust Wallet crypto wallets when scanned.
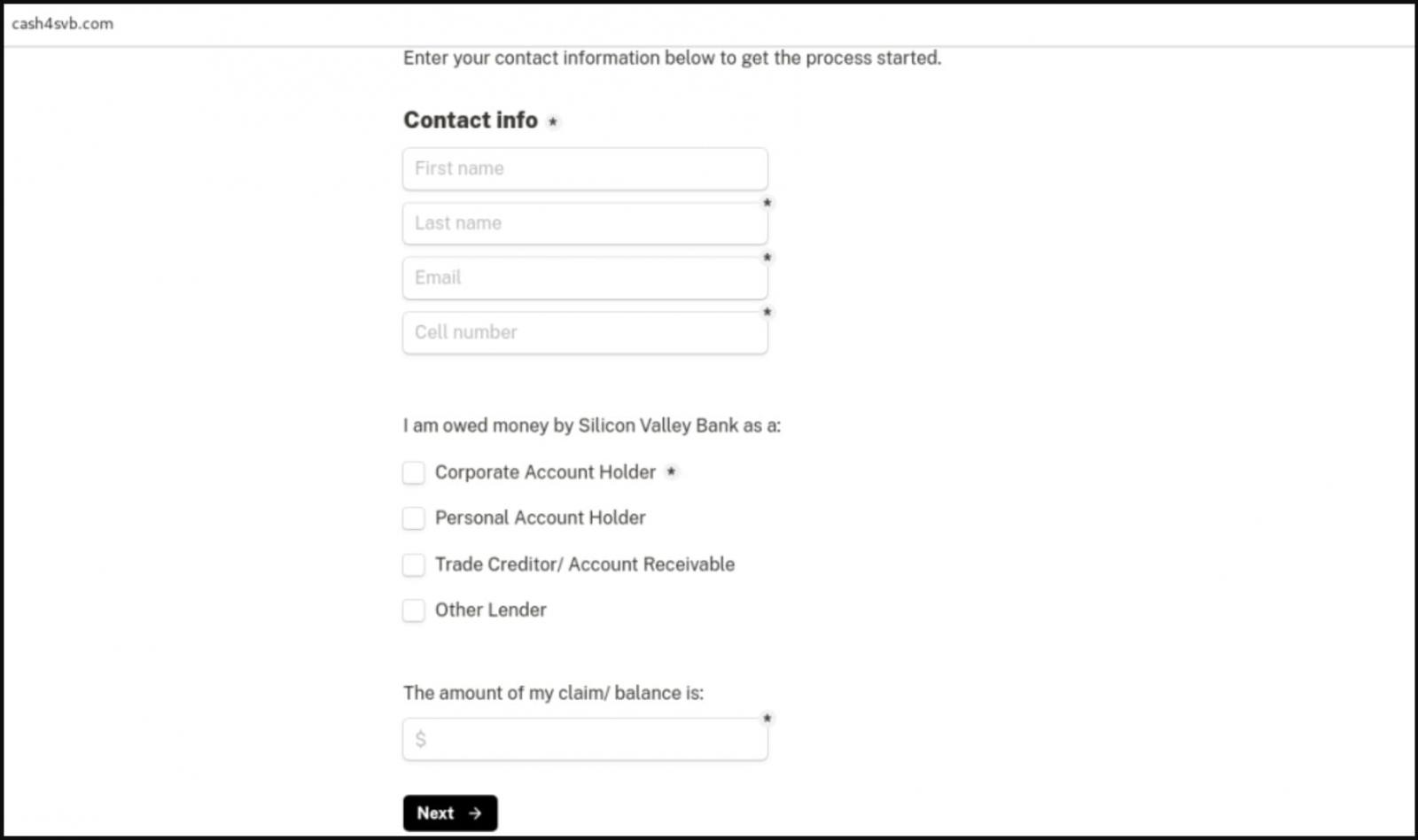
In another case, the threat actors behind “cash4svb.com” attempt to phish former SVB customers’ contact information who are trade creditors or lenders, promising them a return between 65% and 85%.
Circle scams
Peer-to-peer payments firm Circle, which manages the popular stablecoin USDC had a cash reserve of $3.3 billion in the SVB bank. However, the SVB collapse has created uncertainty despite the firm’s assurances of USDC’s liquidity.
This uncertainty has led to the creation of a network of cryptocurrency scam sites using website domains like:
- redeemed-circle[.]com
- circle-reserves[.]com
- circleusdcoin[.]com
- circle-mintusdc[.]com
- svb-circle[.]com
- circle.web3claimer[.]net
- usd-circle[.]com
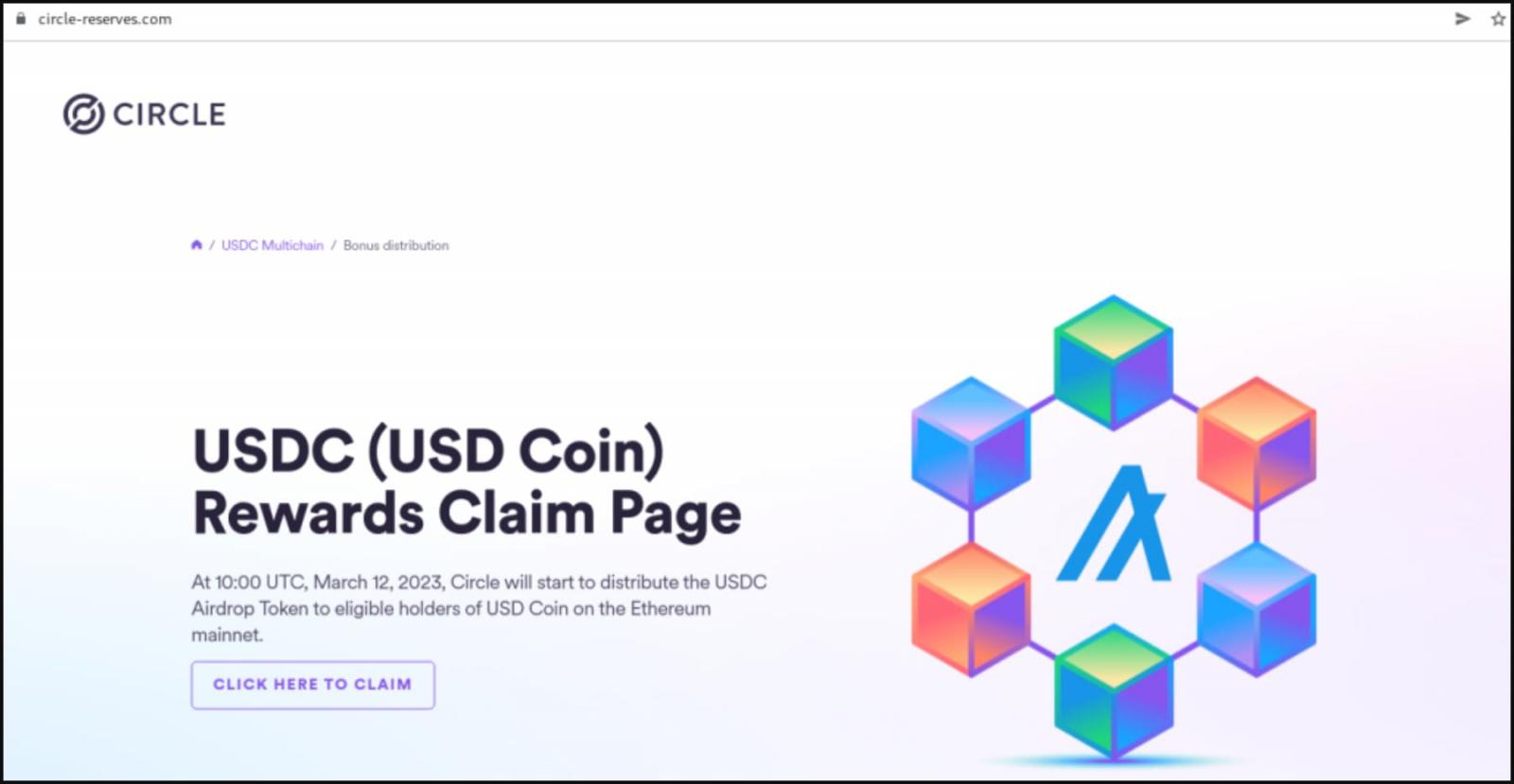
These websites have no real affiliation with Circle, and their sole purpose is to steal their visitors’ wallets, digital assets, or personal details.
Email security firm Proofpoint has also spotted Circle scams stemming from the SVB events, sharing on Twitter a sample of phishing emails sent to targets.
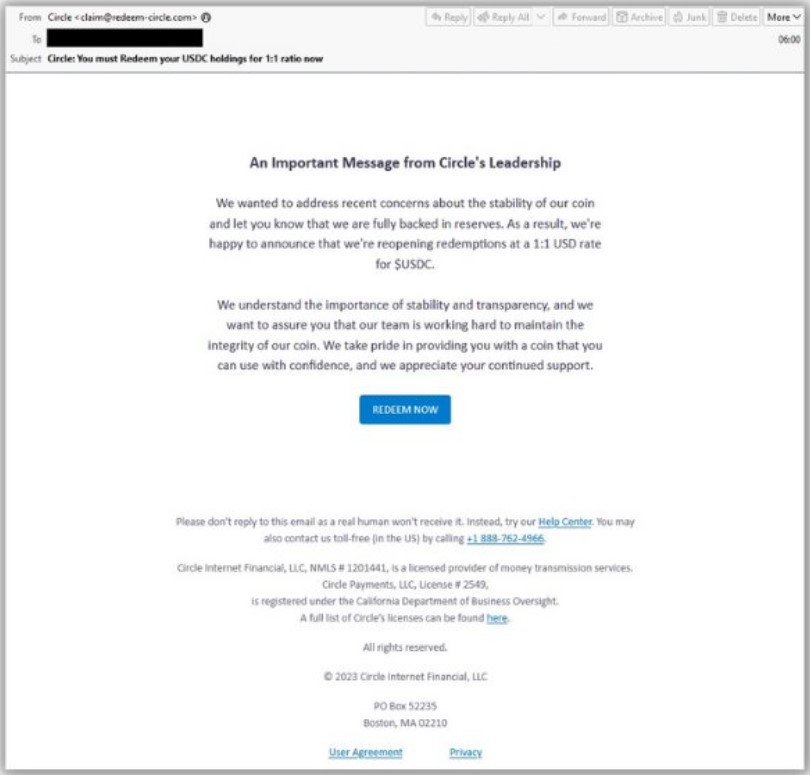
If you are a former SVB customer, the best thing you can do is to stay calm and follow the official communication channels of the U.S. government and the FDIC.
Ignore any emails from unusual domains, and triple-check any requests from alleged SVB banking customers who request that you change bank account details for payments.
The best method to confirm payment changes is to contact your contact via phone, not email, as email accounts can be compromised during these attacks.
