The indie gaming community faces a new and sophisticated threat. Malicious actors are exploiting itch.io and Patreon to distribute the Lumma Stealer malware disguised as legitimate game updates, targeting unsuspecting gamers through a systematic spam campaign across the platform.
Newly created itch.io accounts have been flooding comment sections of legitimate games with templated messages claiming to offer “game updates.”
These comments direct users to Patreon links that download archives named “Updated Version.zip.”
The messaging strategy appears to confuse users unfamiliar with itch.io’s ecosystem, potentially making them believe the updates come from actual game developers rather than malicious actors.
When extracted, most files within these archives appear benign. However, the primary executable, “game.exe,” contains the actual malware payload a sophisticated threat that employs multiple evasion techniques to avoid detection.
A Novel Approach: nexe Compilation
What distinguishes this campaign is its use of nexe, a compiler that converts Node.js applications into standalone PE executables.
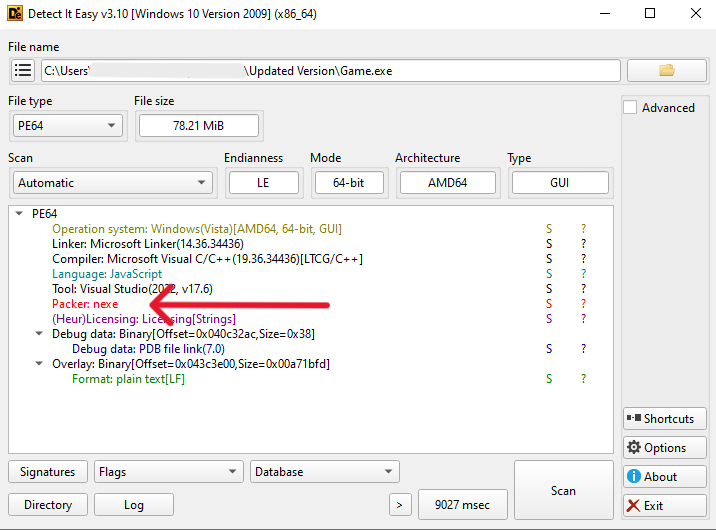
This appears to be the first documented instance of nexe being weaponized for malware distribution in the wild.
Traditionally, Node.js-based malware has required the node.exe runtime; this innovation eliminates that dependency, making the malware more portable and more challenging to detect.
Decompilation reveals an obfuscated JavaScript file named “mains.js” that serves as the malware’s core engine, packed with anti-analysis routines designed to thwart security researchers and automated analysis systems.
The malware implements a comprehensive defensive strategy with six distinct anti-analysis subroutines.
The first checks system resources if RAM is below 4GB or CPU cores are two or fewer, execution halts, indicating virtual environments.
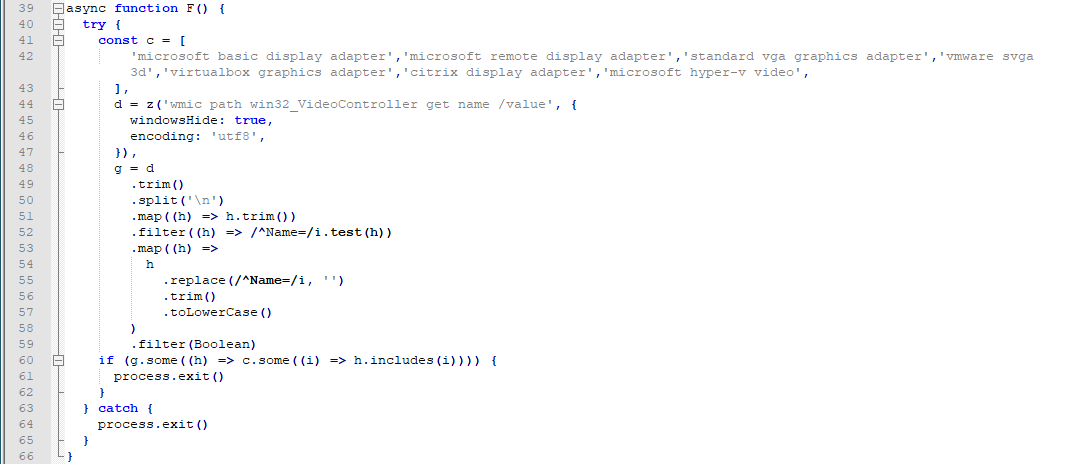
The second searches for sandbox usernames from an extensive predefined list including common analysis system identities like “sandbox,” “vmware,” and “malware.”
The third subroutine compares running processes against a list of over 60 malware analysis tools, including debuggers like IDA Pro, Wireshark, and Burp Suite.
The fourth examines video controller names to identify virtualization indicators such as VMware SVGA 3D and VirtualBox graphics adapters.
The fifth checks system refresh rates, terminating if rates fall below 29Hz typical of virtualized environments. Finally, the sixth inspects disk drive model names for virtual machine identifiers.
LummaStealer Payload Delivery
Upon bypassing these defenses, the malware deploys its final payload through a reflective loading technique.
It decodes and writes a file named “modules.node” a DLL with Node.js API export functions to the system’s temporary directory. This DLL then loads a LummaStealer variant, a notorious information-stealing malware, directly into memory using Node.js APIs.
Evidence suggests a single threat actor managing this campaign across multiple itch.io accounts.
Different samples exhibit varying encoding methods and command-line techniques, with some using PowerShell instead of WMI commands to detect virtualization.
Despite itch.io’s removal of malicious accounts, new ones continue to emerge, maintaining the campaign’s momentum.
Users should exercise extreme caution when downloading game updates from itch.io and verify all updates directly through official game developer channels rather than community comments.
Security teams should monitor for nexe-compiled executables and implement robust endpoint detection for the multi-layered anti-analysis techniques employed in this ongoing campaign.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
