A targeted attack against a U.S.-based certified public accounting firm was discovered in May 2025 by cybersecurity experts, according to a recent study described in eSentire’s Threat Response Unit (TRU) Positives report.
The campaign leveraged a novel crypter named “Ghost Crypt” to deliver PureRAT, a Remote Access Trojan (RAT) that has surged in prevalence throughout 2025.
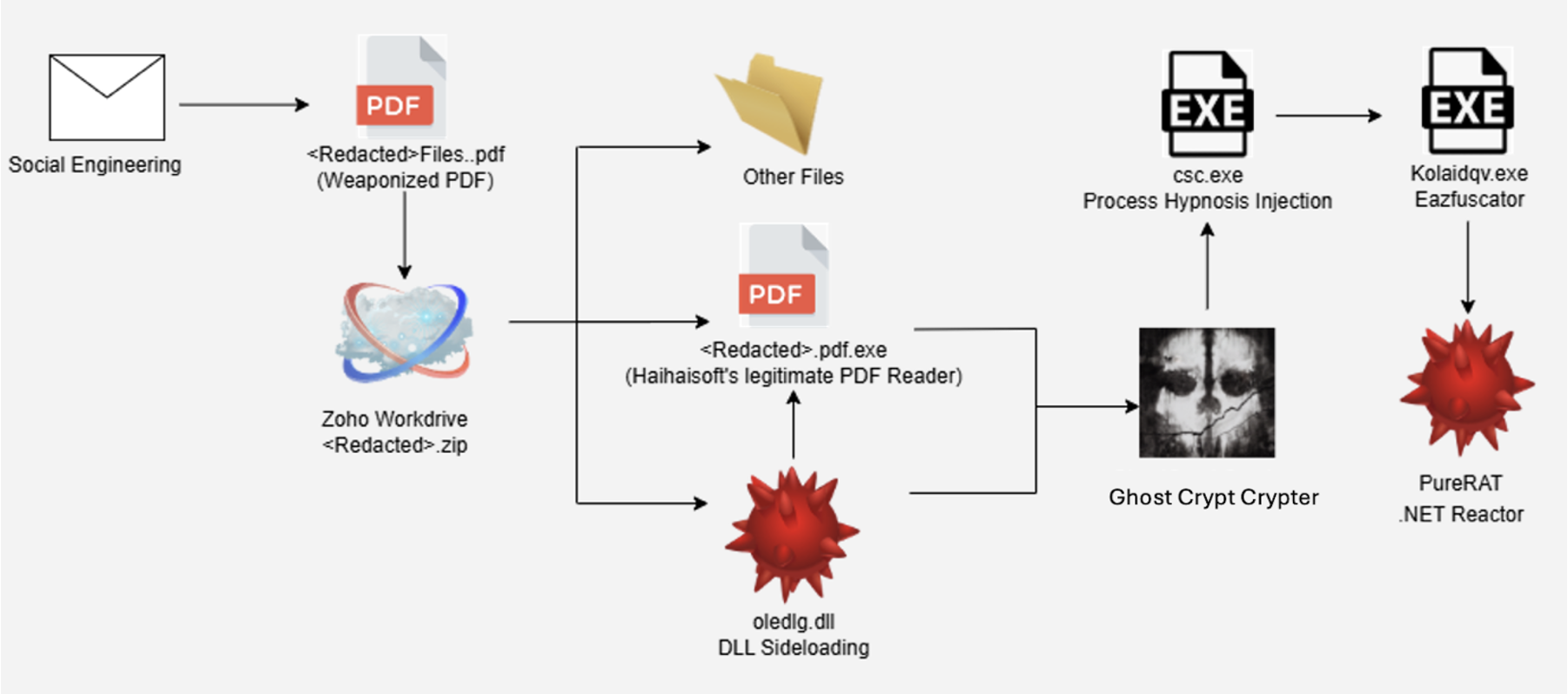
Adversaries employed social engineering tactics, impersonating a new client to distribute malicious payloads via Zoho WorkDrive, a cloud-based file-sharing platform.
This method combined urgency through phone calls with deceptive PDF attachments containing links to zipped archives, enabling initial access and subsequent malware execution.
Sophisticated RAT Campaign
eSentire’s 24/7 Security Operations Centers (SOCs), staffed with Elite Threat Hunters and Cyber Analysts, identified and contained the threat within minutes, underscoring the importance of continuous monitoring in countering such evasive techniques.
Delving into the attack flow, the malicious ZIP archive downloaded from Zoho WorkDrive included seemingly legitimate files like tax documents and a driver’s license scan to build credibility, alongside a double-extension executable disguised as a PDF (e.g., .pdf.exe).
This executable, a legitimate “hpreader.exe” from Haihaisoft Limited, sideloaded a renamed malicious DLL originally called “oledlg.dll” but altered to “CriticalUpdater0549303.dll”.
Multi-Layered Obfuscation
Ghost Crypt, advertised on underground forums like HackForums since April 2025, provided advanced crypting features including support for x86, .NET, and native binaries, DLL sideloading, and claimed bypasses for Windows Defender and various endpoint detection and response (EDR) solutions.
Its key offerings encompass a 99% polymorphic engine, compatibility with Windows 11 24H2+, and integration with tools like Kleenscan for pre-deployment antivirus evasion testing.
The crypter utilized a modified ChaCha20 algorithm with a non-standard magic constant, 12-byte null nonce, and null counter, decrypting the payload before injecting it via “Process Hypnosis” into the legitimate Windows binary csc.exe.
This injection involved creating a debugged child process with CreateProcessW (flags set to DEBUG_ONLY_THIS_PROCESS), allocating RWX memory via VirtualAllocEx, writing the PureRAT payload with WriteProcessMemory, patching ZwManageHotpatch to evade Windows 11 safeguards, and redirecting the entry point using SetThreadContext.
Persistence was established by copying the DLL to the user’s Documents folder and adding a Windows Registry Run key entry.
Further analysis of PureRAT, sold by the vendor PureCoder who shifted focus from PureHVNC to this RAT, revealed heavy obfuscation with Eazfuscator.NET, decryptable using tools like EazFixer.
The malware decrypted payloads via AES-256 in CBC mode, followed by GZIP decompression, skipping initial bytes for extraction.
It loaded an embedded .NET DLL packed with .NET Reactor, unpacked via NetReactorSlayer, which then decompressed a base64-encoded GZIP payload containing an X.509 certificate for secure C2 communication.
The certificate, with a validity extending to 9999 and RSA-4096 public key, facilitated encrypted exfiltration of system data, including hardware fingerprints, user credentials, and targeted cryptocurrency wallet extensions from browsers like Chrome, Edge, and Brave.
Additional scans targeted desktop apps such as Telegram, Ledger Live, Exodus, and Atomic Wallet.
By invoking SetThreadExecutionState with flags preventing system sleep, PureRAT ensured prolonged access, awaiting C2 instructions for plugin deployment.
This infection mirrors tactics in prior PureHVNC campaigns, highlighting the evolving threat landscape where cybercriminals exploit legitimate platforms like Zoho for stealthy RAT distribution.
eSentire recommends multi-factor authentication, employee training on social engineering, and managed detection and response (MDR) services to mitigate such risks, emphasizing that adversaries operate around the clock, necessitating vigilant, AI-augmented defenses.
Get Free Ultimate SOC Requirements Checklist Before you build, buy, or switch your SOC for 2025 - Download Now
