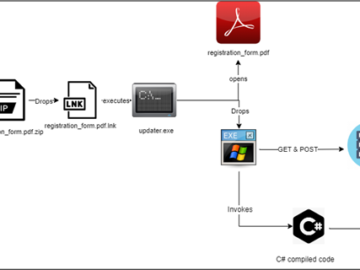
Researchers have published a cybersecurity primer specifically for managers and elected officials in the American local government.
Designed specifically for government officials, this cybersecurity primer aims to simplify essential topics of online security. The primer aims to enhance understanding and clarity, catering to the needs of the nation’s 38,000-plus local government units.
The cybersecurity primer for local government officials
The pdf document incorporates research by Donald F. Norris and Laura K. Mateczun, encompassing over five overarching subjects. These topics encompass inquiries tailored for IT and cybersecurity personnel, providing valuable guidance.
Donald is the professor Emeritus of Public Policy at the University of Maryland and Laura is a research assistant at the Maryland Institute for Policy Analysis and Research.
The key concerns detailed in the primer for cybersecurity were:
- Targeting of local governments
- Success of cyber attacks on local governments
- Vulnerabilities found in the local government systems
- The need for funding for cybersecurity in the local government
- The need for recruiting cybersecurity staff
The cybersecurity primer for government officials brought forth a compelling question, “If they do not understand cybersecurity, how will they be able to know if it is being practiced properly and effectively?”
To answer this, the cybersecurity primer offered suggestions such as advocating for a dedicated cybersecurity budget rather than including it within a general IT budget.
It also emphasized the importance of regular deliberations concerning the risk environment. Furthermore, the primer underscored the value of internal training to bolster cyber awareness.
Cybersecurity training is an integral part of effective application, not just for government officials alone but also for third-party vendors and contractors who are part of the team.
Another essential factor noted in the primer for American government officials was to practice responding to a threat or/ and cyber attack. It would help to think right and act swiftly in times of crisis to curb further damage if response activities are practiced and well-understood by the team.
Response activities are a set of actions involving both automatic controls and communication among the staff. The flow and steps to be followed must be the cornerstone of the response plan in any government office.
Working together to counter security threats from disruptive groups
The cybersecurity of the US government involves a collective approach, with various entities collaborating. This includes legal agencies, the National Institute of Standards and Technology (NIST), federal agencies, and the Multi-State Information Sharing and Analysis Center (MS-ISAC), all working in coordination.
A roadblock noted in the cybersecurity primer for US government officials was the lack of an adequate support system observed between the Chief Information Security Officers (CISO), IT directors in the local governments, and the top local government officials.
This lack of coordination and understanding of the critical nature of cyber security has been a prime reason for a slow response in the face of cyber threats.
The research noted the importance of effective leadership in curbing cyber risks and maintaining an active team to defend critical systems.
The sector is in need of not just one, however, many champions who drive the present workforce to create a wall as strong as possible until more help is found in terms of funding and recruitment.
Addressing the role and involvement of the CISO the research stated, “To the maximum extent possible, centralize all aspects of cybersecurity under a single, qualified Chief Information Security Officer (CISO) or other appropriate senior official.”
The cybersecurity primer concluded on a statement that read, “It is not whether you will be breached but when.” To this, they added – “and how many times?”
If threats can be exploited using any vulnerability in software, hardware, third-party access, and human error, then it becomes a part of the entire team to collaborate and adapt to best practices and believe that together a lot more could be done.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.