The pro-Russia hacktivist group CyberVolk launched a ransomware-as-a-service (RaaS) called VolkLocker that suffered from serious implementation flaws, allowing victims to potentially decrypt files for free.
According to SentinelOne researchers who examined the new ransomware family, the encryptor uses a hardcoded master key in the binary, which is also written in plaintext in a hidden file on affected machines.
This allows targeted companies to use the key to decrypt files for free, undermining VolkLocker’s potential in the cybercrime space.
Hacktivism and cybercrime
CyberVolk is reportedly an India-based pro-Russia hacktivist collective that started operations last year, launching distributed denial of service and ransomware attacks against public and government entities opposing Russia or siding with Ukraine.
While the group was disrupted on Telegram, it returned in August 2025 with a new RaaS program, VolkLocker (CyberVolk 2.x), which targets both Linux/VMware ESXi and Windows systems.
An interesting feature of VolkLocker is the use of a Golang timer function in its code, which, when it expires or when an incorrect key is entered in the HTML ransomware note, triggers the wiping of user folders (Documents, Downloads, Pictures, and Desktop).
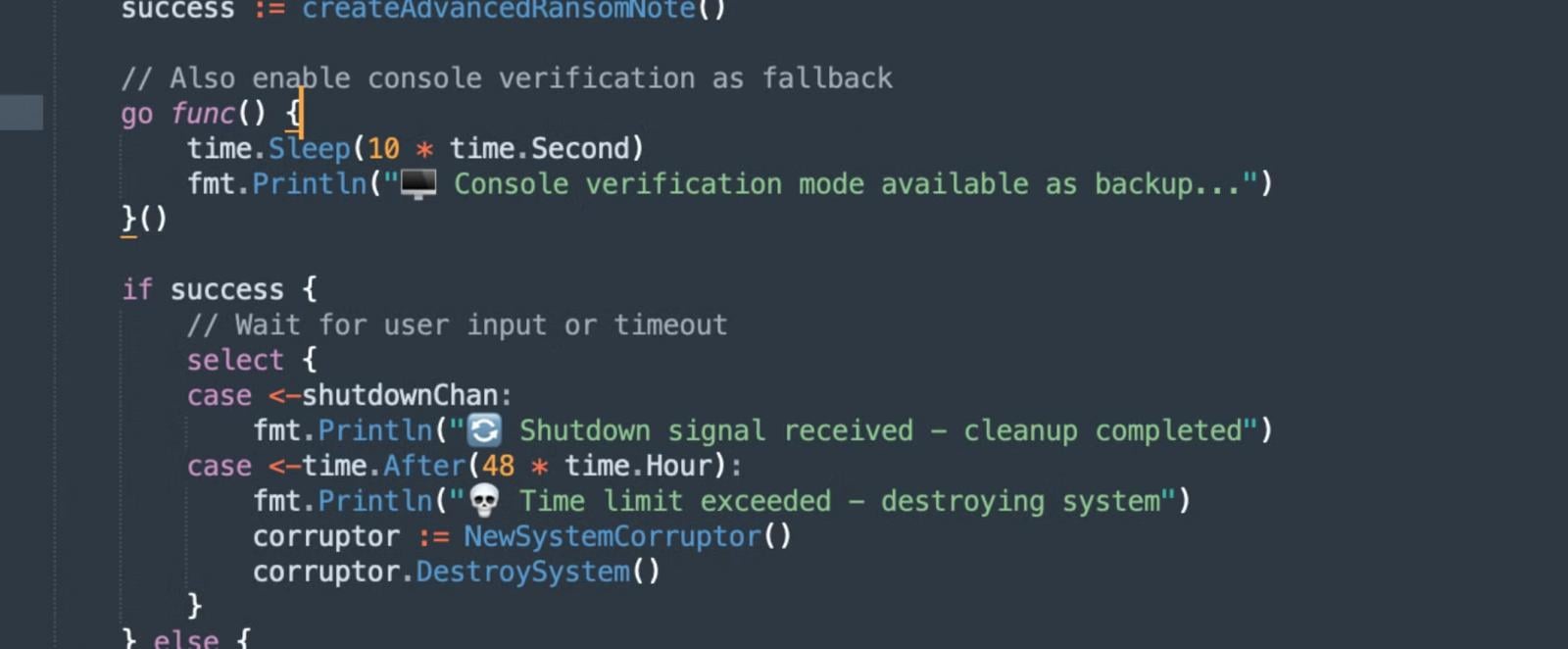
Source: SentinelOne
Access to the RaaS costs between $800 and $1,100 for a single OS architecture, or $1,600 to $2,200 for both.
Purchasers can access a builder bot on Telegram to customize the encryptor and receive the generated payload.
In November 2025, the same threat group began advertising a remote access trojan and a keylogger, both priced at $500 each.
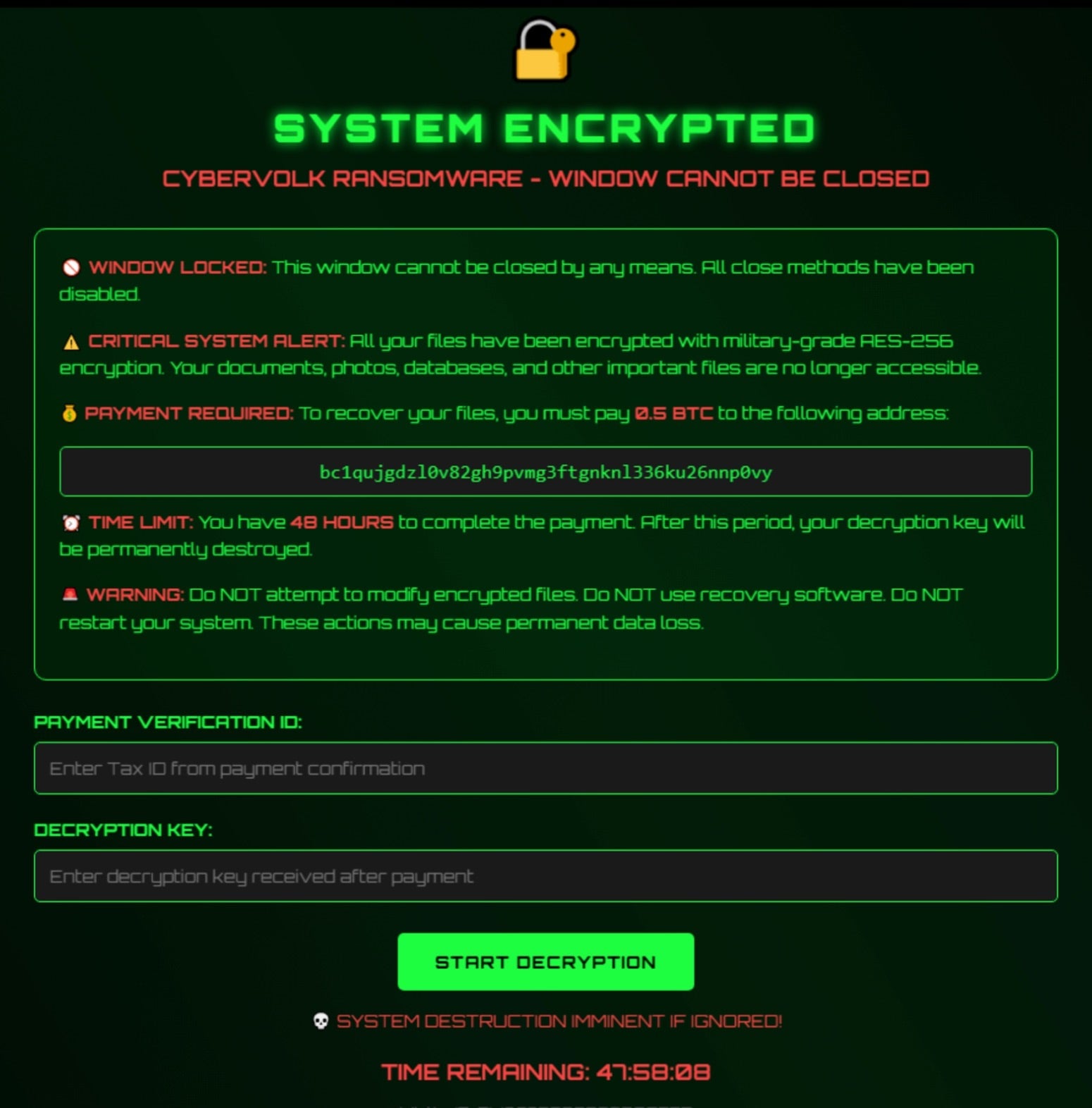
Source: SentinelOne
Critical crypto weakness
VolkLocker uses AES-256 in GCM (Galois/Counter Mode) encryption, with a 32-bit master key derived from a 64-character hex string embedded in the binary.
A random 12-byte nonce is used as the initialization vector (IV) for each file, deleting the original file and appending the .locked or .cvolk file extension to the encrypted copy.
The problem is that VolkLocker uses the same master key to encrypt all files on a victim system, and that same key is also written to a plaintext file (system_backup.key) in the %TEMP% folder.
“Since the ransomware never deletes this backup key file, victims could attempt file recovery by extracting the necessary values from the file,” explains SentinelOne.
“The plaintext key backup likely represents a test artifact inadvertently shipped in production builds.”
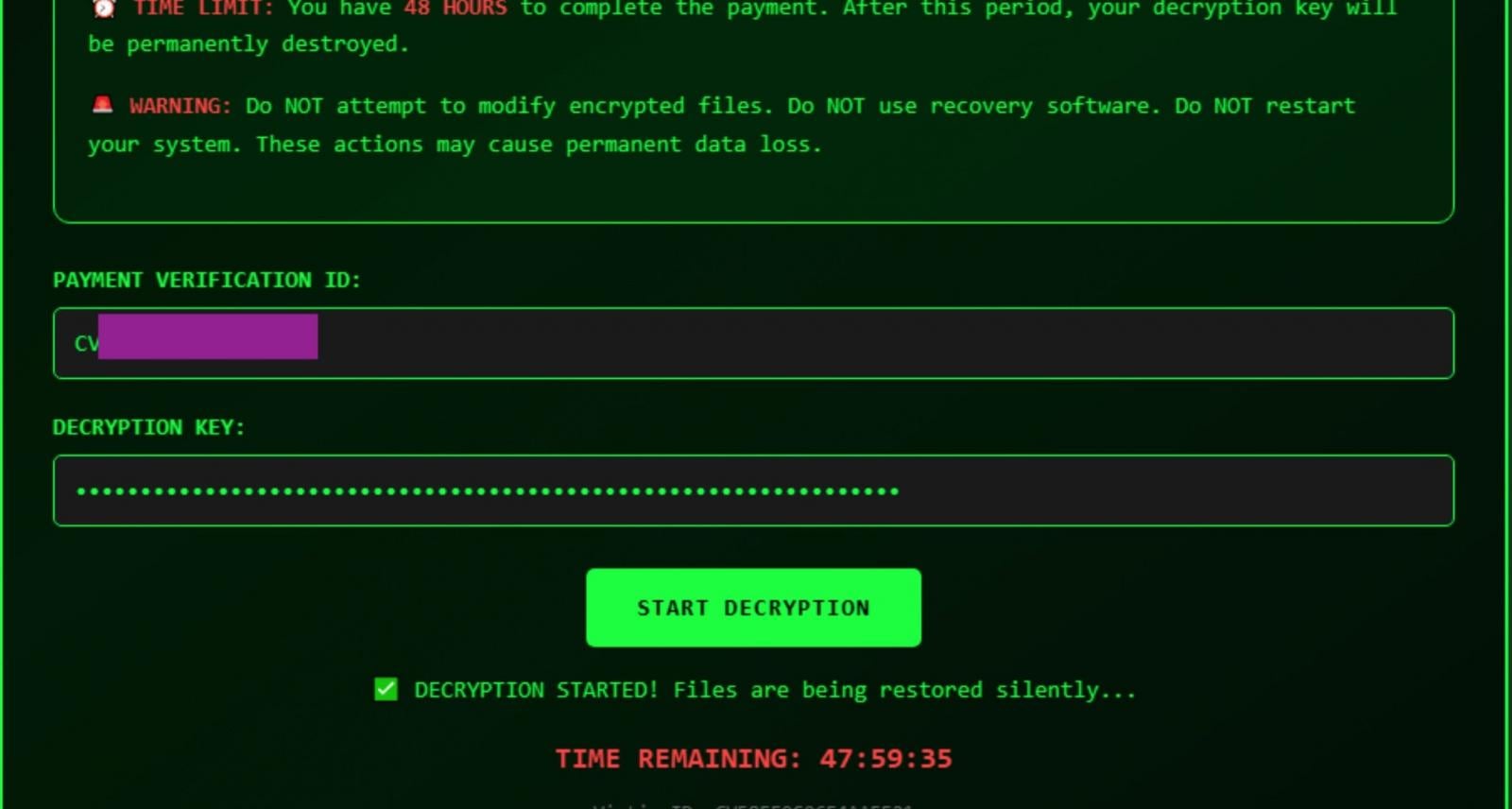
Source: SentinelOne
While this flaw may help any existing victims, the disclosure of VolkLocker’s cryptographic flaw will likely prompt threat actors to fix the bug and prevent it from being abused in the future.
It is considered a better practice not to disclose ransomware flaws while a threat actor is actively running the operation, and instead to share them privately with law enforcement and ransomware negotiation firms that can privately assist victims.
BleepingComputer has contacted SentinelOne to ask about its decision to publicly disclose VolkLocker’s weakness, and a spokesperson sent the below explanation:
“The reason we didn’t hesitate is that this isn’t a core encryption flaw but rather a testing artifact that’s inadvertently getting shipped to some production builds by incompetent operators and isn’t a reliable decryption mechanism beyond those cases. It’s more representative of the ecosystem that CyberVolk is trying to enable through this RaaS offering.” – SentinelOne spokesperson

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
