By Michael Angelo Zummo, Threat Intel Expert – Cybersixgill
Phishing tools and services are common and accessible on the underground. We took a close look at one of them and discovered how easy it can be to launch a phishing scheme.
Phishing is a type of cyberattack in which attackers attempt to deceive individuals into divulging sensitive information, such as usernames, passwords, credit card details, and other personal or financial information. This is typically done by posing as a trustworthy entity, such as a reputable company, financial institution, government agency, or even a friend or colleague.
The cyber underground hosts more than just leaked data, credentials, and narcotics. It is also a marketplace for a variety of tools and services to assist threat actors in carrying out their attacks. This includes phishing.
In the past month alone, underground forums and markets hosted over 2,427 conversations about phishing attacks, templates, kits, and services, with another 17,000 on Telegram, including chatter about services and kits for sale (Figure 1).
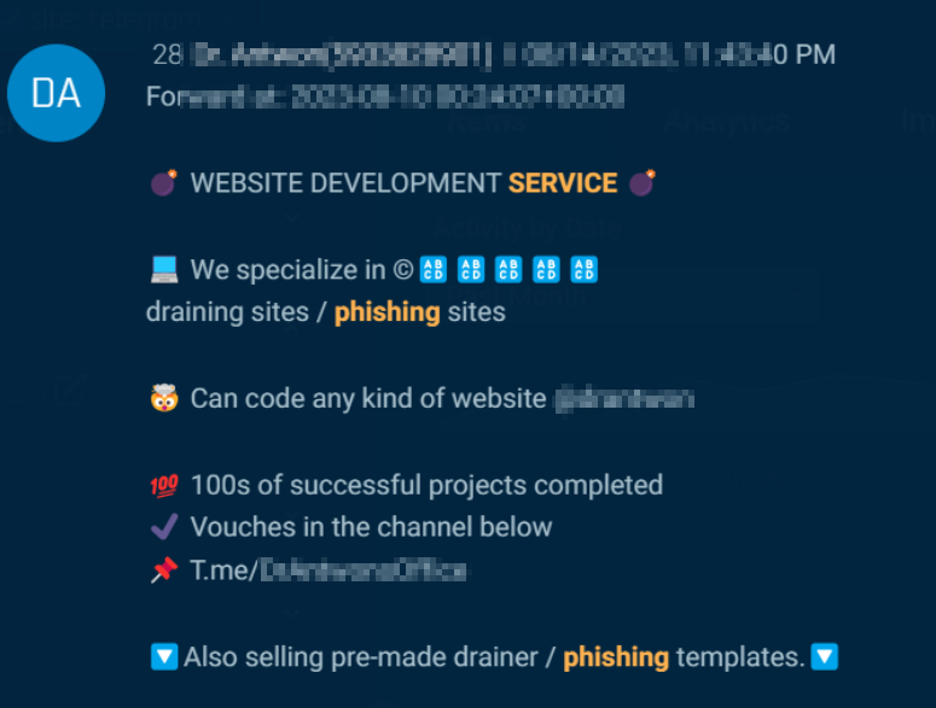
Figure 1. A phishing service is advertised in the underground.
Phishing templates
Much of the focus on phishing consisted of threat actors seeking or offering templates. For example, on July 26, a threat actor on a dark web forum requested that anyone with a Santander Bank email template private message them for further discussion (Figure 2).
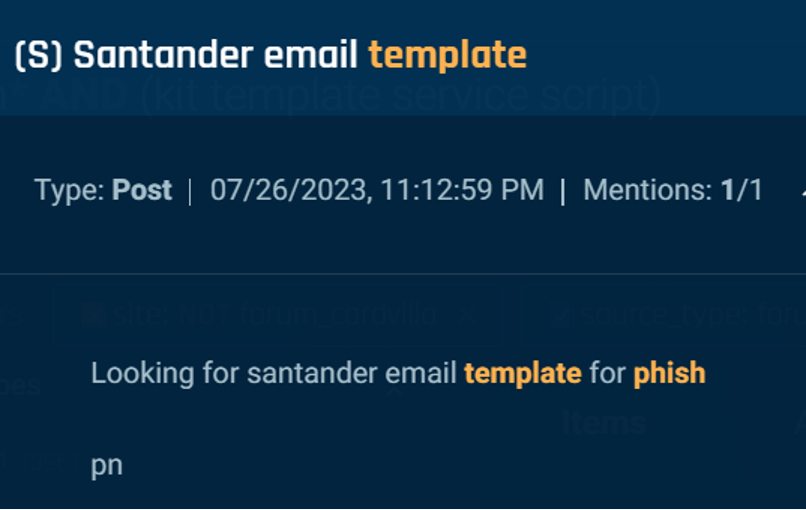
Figure 2. A threat actor requesting an email template to phish Santander Bank.
Furthermore, other threat actors advertised their phishing and scam pages, such as this post on a popular hacking forum (Figure 3).
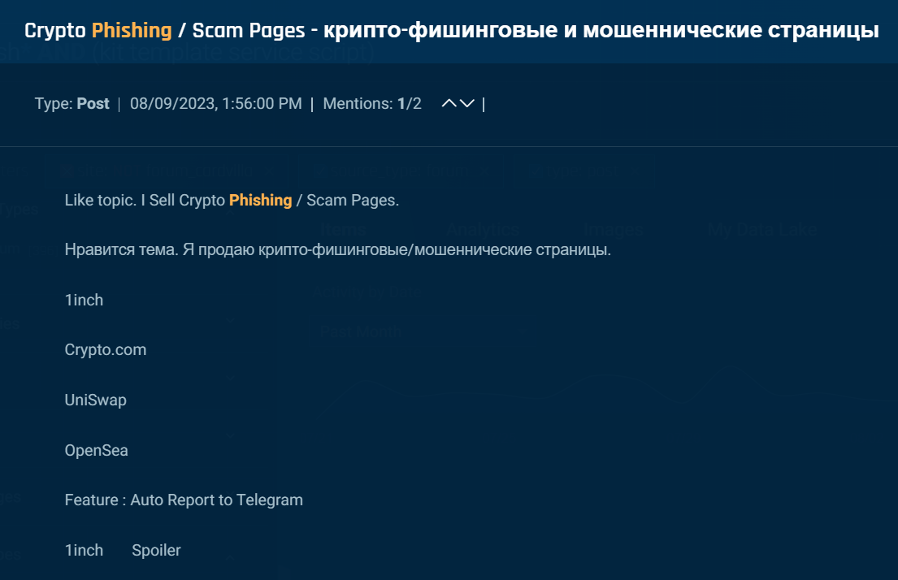
Figure 3. Threat actors offering their phish and scamp pages for sale on an underground forum.
Phishing Tools and Services
There are a variety of phishing tools and services available for threat actors in the underground. The most notable in the past month was the phishing-as-a-service program, Evilproxy, which provides the ability to run phishing attacks with reverse proxy capabilities that steal credentials and assist in bypassing 2FA (Figure 4).
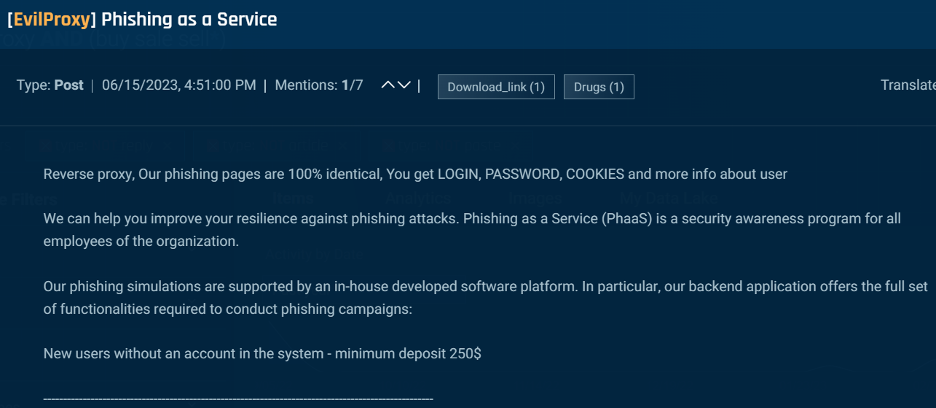
Figure 4. A threat actor advertising their phishing as a service with EvilProxy.
EvilPhish
For those looking for less expensive options, there are free tools available that can be used for experimentation or in real attacks. For example, EvilPhish is an open-source tool available on Github that simply creates an evil twin of a web page and redirects traffic to a local web server hosting the phishing page. To demonstrate how accessible these tools are for threat actors, we installed EvilPhish in our attack box and tried it for ourselves.
EvilPhish is a simple script that copies a web page of your choosing to use as a template for your own phishing page. For the demonstration, we used Cybersixgill’s portal login page and downloaded the HTML to save in our EvilPhish folder. From there, we ran a command on that file, “./NewPage” and moved all the files to our WebPages folder (Figure 5).
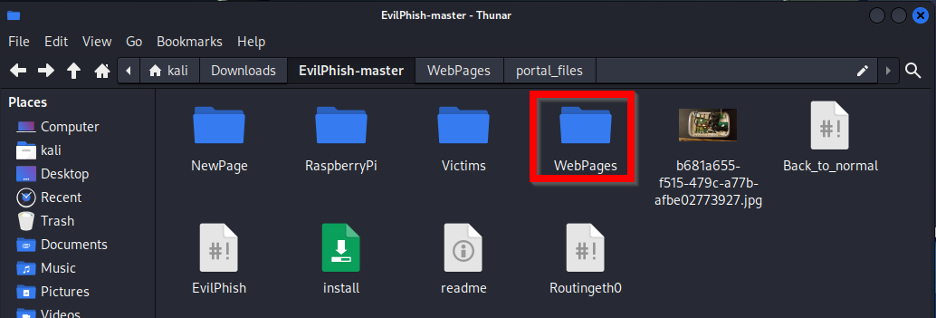
Figure 5. Copying HTML file to WebPages folder.
Next, we ran the EvilPhish script on our WebPages folder to create the new phishing page (Figure 6).
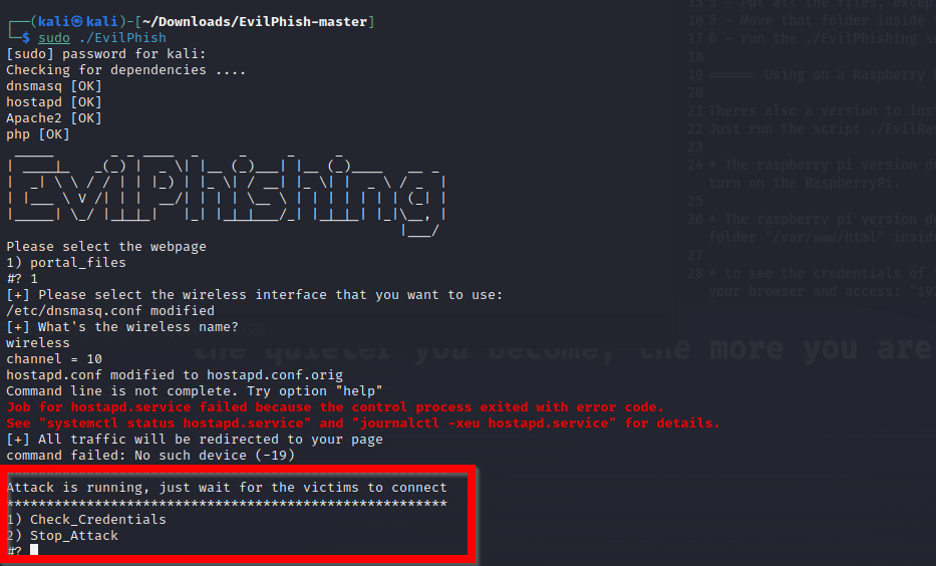
Figure 6. Running the ./EvilPhish script on the HTML files.
As you can see in the below screenshot, our phishing page ran locally while waiting for users to input their credentials (Figure 7).
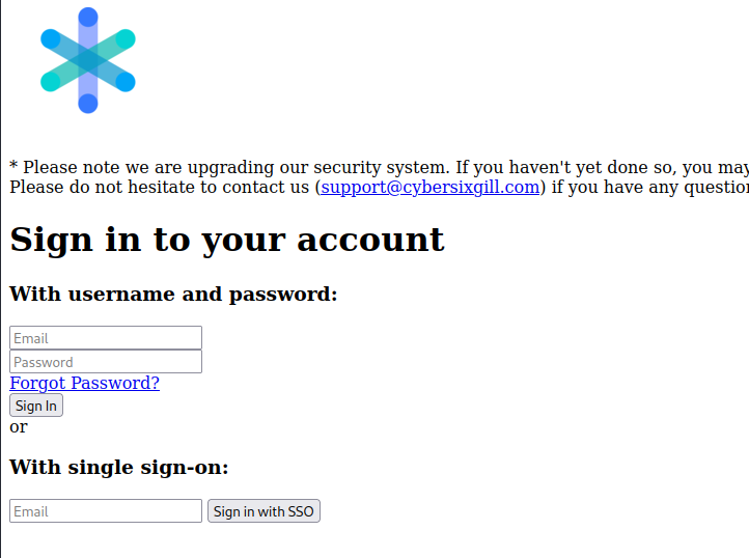
Figure 7. A phishing page impersonating Cybersixgill that we created with EvilPhish.
As a test, we inserted “test” for the username and password to see what EvilPhish captured (Figure 8).
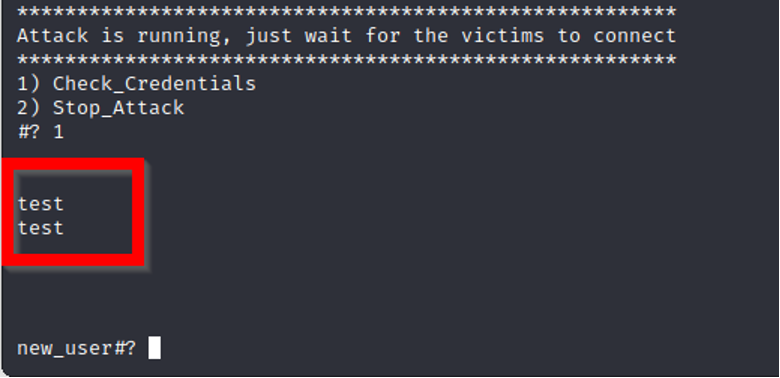
Figure 8. Example of captured user credentials entered on our phishing page.
Once we confirm the tool works, all that a threat actor would need to do is host this on a public domain and redirect traffic to the scam page through various techniques such as embedded links, phishing emails, SMS, and more. Additionally, one can make the page look more convincing through some HTML and CSS modifications.
Conclusion
The cyber underground continues to provide a variety of avenues and opportunities for threat actors to engage in malicious activities. Free, easy-to-use tools are widely available, and actors can deploy them in successful attacks. A curious threat actor with an appetite for cybercrime can inflict a lot of damage.
Fortunately, organizations can take measures to defend themselves. Here are a few tips to proactively defend against phishing attacks.
– Conduct education and awareness training for employees
– Verify senders of emails and use filters when possible
– Enable two-factor authentication for an extra layer of protection
– Implement typosquatting and domain monitoring into your security stack– Monitor underground channels to detect phishing templates, tools, and services targeting your organization with real-time, comprehensive threat intelligence.
Ad
