A new variant of the DarkCloud information-stealer malware has been observed targeting Microsoft Windows systems, primarily affecting Windows users by collecting sensitive data such as login credentials, financial information, and personal contacts.
Discovered in early July 2025 by Fortinet’s FortiGuard Labs, this high-severity campaign leverages sophisticated phishing tactics to initiate infections, demonstrating advanced evasion methods including fileless execution and process hollowing.
DarkCloud, first identified in 2022, is a stealthy Windows-based malware engineered to exfiltrate a wide array of sensitive information from compromised machines, posing substantial risks to individual privacy and organizational security.
Exploits Fileless Techniques
The campaign’s infection chain begins with a phishing email containing a RAR archive disguised as an urgent quote, lacking any message body to heighten curiosity and prompt immediate interaction.
Upon extraction, the archive reveals a standalone JavaScript file, which, when executed via WScript.exe, deobfuscates and launches Base64-encoded PowerShell code.
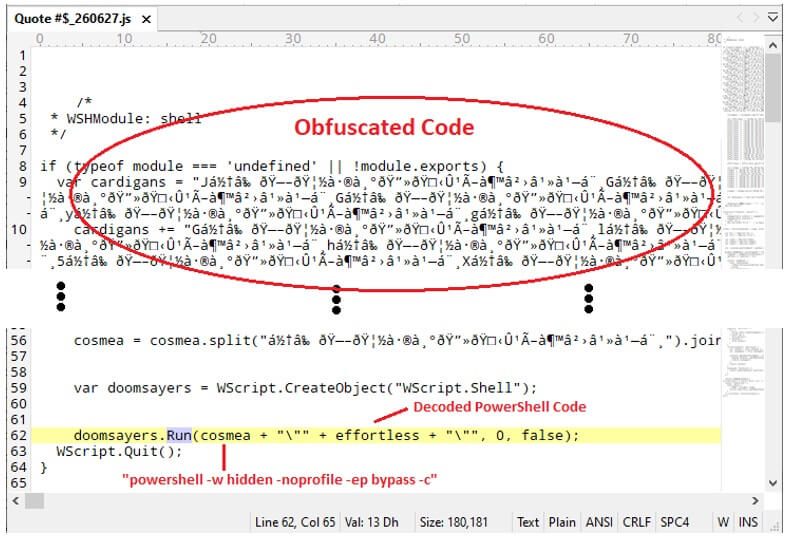
This PowerShell script downloads a seemingly innocuous JPEG image embedded with an encrypted .NET DLL, masquerading as a legitimate Microsoft.Win32.TaskScheduler assembly.
The DLL is loaded reflectively using [Reflection.Assembly]::Load() and invokes the VAI() method, passing parameters that facilitate persistence and payload deployment.
The .NET module establishes system persistence by copying the initial JavaScript file to a public directory (e.g., C:UsersPublicDownloadsedriophthalma.js) and adding an auto-run registry entry under HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun, ensuring automatic execution on startup.
It then decodes a reversed Base64 string to retrieve a URL (hxxp://paste[.]ee/d/0WhDakVP/0), from which it downloads a reversed PE file.
This file is reversed, converted from hex to binary, and injected into a suspended MSBuild.exe process via process hollowing, utilizing Windows APIs such as CreateProcess(), NtUnmapViewOfSection(), WriteProcessMemory(), SetThreadContext(), and ResumeThread() to hollow out the legitimate process and execute the malware covertly.
The DarkCloud payload, implemented in Microsoft Visual Basic 6, incorporates anti-analysis features like over 600 encrypted constant strings decrypted at runtime and an anti-sandbox mechanism that monitors keyboard and mouse activity through GetAsyncKeyState() calls, remaining dormant until user interaction is detected to evade automated analysis environments.
Exfiltration Mechanisms
Once active, the malware systematically gathers basic system information, including computer name and username via rtcEnvironVar(), and the victim’s public IP from http://showip.NET.
It targets credentials and payment details from browsers like Google Chrome, Microsoft Edge, Mozilla Firefox, and Brave, querying SQLite databases in profile paths for login data and credit card information using SQL statements such as “SELECT origin_url, username_value, password_value FROM logins” and decrypting encrypted fields with a dropped auxiliary EXE.
Additional data is harvested from email clients (e.g., Mozilla Thunderbird, Microsoft Outlook), FTP tools (e.g., WinSCP, FileZilla), and applications like Adobe, dnSpy, and Wireshark, storing outputs in local text files.
According to the report, Email contacts are similarly extracted and saved in files like ThunderBirdContacts.txt or OutlookContacts.txt.
Exfiltration occurs primarily via SMTP, with decrypted server details enabling the malware to attach these files to emails, incorporating victim details in the subject line for attacker identification, all transmitted over TLS to maintain stealth.
Fortinet protections mitigate this threat through AntiSPAM, Web Filtering, IPS, and AntiVirus services, detecting the phishing emails, malicious URLs, and payloads with signatures like JS/DarkCloud.ACVJ!tr and W32/DarkCloud.QU!tr.
Users are advised to enable real-time scanning and undergo security awareness training to recognize such phishing attempts.
Indicators of Compromise (IOCs)
| Type | Indicator |
|---|---|
| URL | hxxps://archive[.]org/download/universe-1733359315202-8750/universe-1733359315202-8750.jpg |
| URL | hxxp://paste[.]ee/d/0WhDakVP/0 |
| SHA-256 (JS) | 381AA445E173341F39E464E4F79B89C9ED058631BCBBB2792D9ECBDF9FFE027D |
| SHA-256 (Payload) | 82BA4340BE2E07BB74347ADE0B7B43F12CF8503A8FA535F154D2E228EFBEF69C |
The Ultimate SOC-as-a-Service Pricing Guide for 2025– Download for Free
