US-based telecommunication service T-Mobile has disclosed a data breach that affected 37 million postpaid and prepaid accounts.
In a regulatory filing on 19 January, the company said that it is investigating the matter and that it expects to incur significant costs related to the incident.
T-Mobile claims to have identified the malicious activity on January 5 and contained it within 24 hours. According to the company, no sensitive information such as financial data was compromised.
“We promptly commenced an investigation with external cybersecurity experts and within a day of learning of the malicious activity, we were able to trace the source of the malicious activity and stop it,” the company disclosure said.
“Our investigation is still ongoing, but the malicious activity appears to be fully contained at this time, and there is currently no evidence that the bad actor was able to breach or compromise our systems or our network.”
However, basic customer information, such as names, billing addresses, email addresses, and phone numbers, were obtained.
The company stated that the investigation is ongoing and that the malicious activity appears to be fully contained at this time.
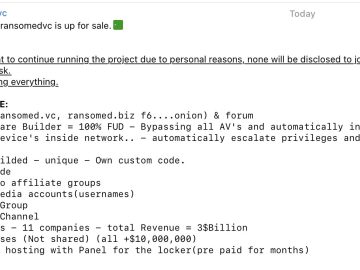
T-Mobile data breach and attack vector
T-Mobile is the third-largest wireless carrier in the United States, with over 110 million subscribers. According to the company disclosure, a bad actor was obtaining data through a single Application Programming Interface (“API”) without authorization.
The data breached included customers’ names, billing addresses, email addresses, phone numbers, dates of birth, T-Mobile account numbers, and details about the number of lines and plan features for each account.
APIs are sets of instructions that enable applications to access data and interact with web databases. However, if not properly secured, these APIs can be exploited by malicious actors to collect large amounts of information stored in those databases.
In October, mobile provider Optus reported that hackers took advantage of a weakly secured API to steal data on 10 million customers in Australia.
The disclosure stressed that the leak was blocked on time and currently there is no evidence that the bad actor was able to breach or compromise their systems or network.
However, the markets did not take these assurances kindly. In after-hours trade, the company’s shares fell 2%.
T-Mobile and earlier data breaches
It’s been hardly a year since T-Mobile was in the cybersecurity news for a major cyber incident.
In April 2022, Krebsonsecurity reported that the Lapsus$ hacking group successfully breached T-Mobile’s systems and stole the company’s source code. Lapsus’s recent targets include Samsung, Uber, and Cisco.
T-Mobile confirmed the attack in a statement to The Verge and stated that the systems accessed did not contain any customer or government information or other sensitive information.
According to private messages obtained by Krebs, the Lapsus$ group had planned to target T-Mobile in the week prior to the arrest of seven of its teenage members.
The group purchased employees’ credentials online and used T-Mobile’s internal tools, such as the Atlas customer management system, to perform SIM swaps.
A SIM swap is a type of attack in which the attacker hijacks a target’s mobile phone number by transferring it to a device owned by the attacker.
This allows the attacker to intercept texts or calls received by that phone number, including any messages sent for multi-factor authentication.
In 2021, T-Mobile agreed to pay $350 million and spend an additional $150 million to upgrade data security to settle litigation over a cyberattack that compromised information belonging to an estimated 76.6 million people.