Cloud security firm Datadog says that one of its RPM GPG signing keys and its passphrase have been exposed during a recent CircleCI security breach.
However, the company added that it has yet to find evidence that this key was leaked or misused.
“As of January 16th, 2023, Datadog has no indication that the key was actually leaked or misused, but we are still taking the following actions out of an abundance of caution,” Datadog said.
In response to CircleCI’s disclosure that the threat actor stole customers’ environment variables, tokens, and keys from its databases, Datadog has released a new version of its Agent 5 RPM for CentOS/RHEL, signed with a new key.
The company has also released a new Linux install script that removes the affected key from the Datadog repo file and the RPM database.
Datadog repos not compromised
Datadog added that even if the attacker managed to steal the signing key and would craft a malicious RPM package, they wouldn’t be able to use it to target the company’s customers because they would also need access to the official package repositories.
“Official Datadog repositories were not compromised. The signing key, if actually leaked, could be used to construct an RPM package that looks like it is from Datadog but it would not be enough to place such a package in our official package repositories,” Datadog said.
“A hypothetical attacker with the affected key would need to be able upload the constructed RPM package to a repository used by the system.”
Customers are advised to ensure that their systems stop trusting the affected key and, if they still do, to delete the key and verify if all installed were built by Datadog using the instructions available here.
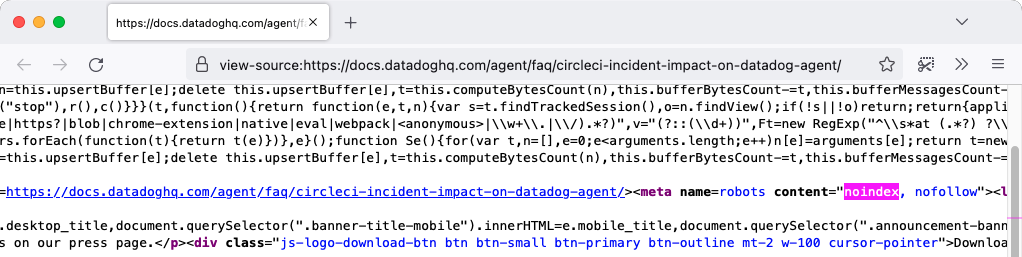
Datadog published this information on its documentation page as a “Frequently Asked Questions,” which isn’t listed on the company’s website next to the other FAQs.
Additionally, BleepingComputer couldn’t find this page on the web because search engines won’t index it since Datadog has added ‘noindex’ and ‘nofollow’ tags to its metadata.
A Datadog spokesperson was not immediately available for comment when contacted by BleepingComputer earlier today for more details.
Datadog’s disclosure comes after CircleCI revealed on Friday that its systems were breached via an engineer’s malware-infected laptop.
CircleCI first disclosed that it suffered a security incident in early January and warned all customers to rotate their secrets and tokens.
Last week, the software company said the attackers also stole customer secrets after gaining access to its internal systems using a 2FA-backed SSO session cookie from the employee’s compromised device.
The company added that multiple customers (“fewer than 5”) already found “unauthorized access to third-party systems” and warned clients to investigate their environments for suspicious activity starting December 16, 2022.
