Dell is warning customers of a data breach after a threat actor claimed to have stolen information for approximately 49 million customers.
The computer maker began emailing data breach notifications to customers yesterday, stating that a Dell portal containing customer information related to purchases was breached.
“We are currently investigating an incident involving a Dell portal, which contains a database with limited types of customer information related to purchases from Dell,” reads a Dell data breach notification shared with BleepingComputer.
“We believe there is not a significant risk to our customers given the type of information involved.”

Dell states that the following information was accessed by the threat actor during the breach:
- Name
- Physical address
- Dell hardware and order information, including service tag, item description, date of order, and related warranty information
The company stresses that the stolen information does not include financial or payment information, email addresses, or telephone numbers and that they are working with law enforcement and a third-party forensics firm to investigate the incident.
BleepingComputer contacted Dell on Wednesday to learn more about the breach and how many people it impacted but was told they “are not disclosing this specific information from our ongoing investigation.”
Data was for sale on a hacking forum
As first reported by Daily Dark Web, a threat actor named Menelik attempted to sell a Dell database on the Breach Forums hacking forum on April 28th.
The threat actor said they stole data from the computer maker for “49 million customer and other information systems purchased from Dell between 2017-2024.”
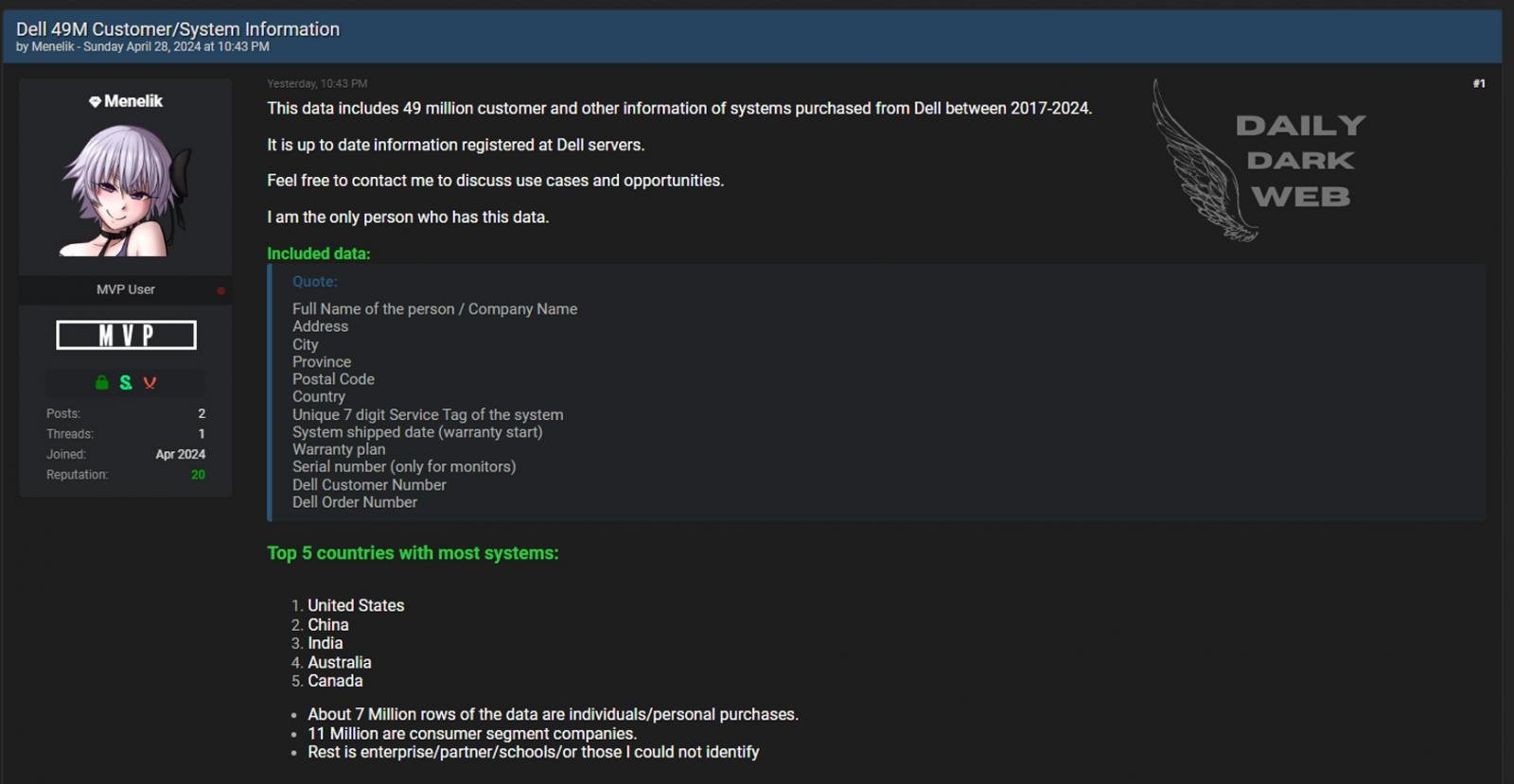
Source: Daily Dark Web
While BleepingComputer has not been able to confirm if this is the same data that Dell disclosed, it matches the information listed in the data breach notification.
The Breach Forum’s post has since been deleted from the site, which could indicate that another threat actor purchased the database.
Dell does not “believe there is significant risk to our customers given the type of information involved,” yet the stolen information could potentially be used in targeted attacks against Dell customers.
As the stolen information does not include email addresses, threat actors could target specific people with physical mailings that contain media (DVDs/thumb drives) to install malware on targets’ devices.
While this may sound far-fetched, threat actors have conducted similar attacks in the past, physically mailing tampered Ledger hardware wallets that stole cryptocurrency or sending gifts with USB drives that installed malware.

Source: TrustWave
As the database is no longer being sold, there is a good chance a threat actor is attempting to monetize it in some way through attacks.
Therefore, be wary of any physical mailings or emails you receive that claim to be from Dell asking you to install software, change passwords, or perform some other potentially risky action.
If you receive an email or physical mailing, you should instead contact Dell directly to confirm it is legitimate.




