Hackers have been targeting developers by using fake job offers to hijack GitHub accounts.
This alarming trend has raised significant concerns among corporate information security teams, especially since developers often have administrative access to critical repositories.
The attack begins with an email that appears to be from GitHub, offering an attractive job position with a $180,000 annual salary and generous benefits.
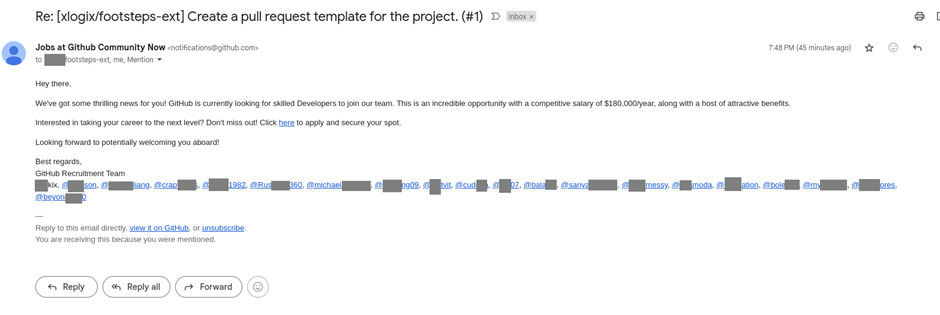
The emails are sent from [email protected], a legitimate GitHub address, which makes them appear authentic, as per a report by Kaspersky.
However, there are subtle red flags, such as the use of a notification address for HR communications and email subjects that do not match the job offer content.
Despite these discrepancies, the promise of a lucrative salary entices some recipients to click the link provided.
"Is Your System Under Attack? Try Cynet XDR: Automated Detection & Response for Endpoints, Networks, & Users!"- Free Demo
Phishing Career Site on GitHub
Clicking the link directs the recipient to a fake GitHub career site, using addresses like githubtalentcommunity[.]online and githubcareers[.]online.
These phishing sites have since been taken down, but not before causing significant damage. On the fake site, developers are prompted to log in to their GitHub account and authorize a new OAuth application.
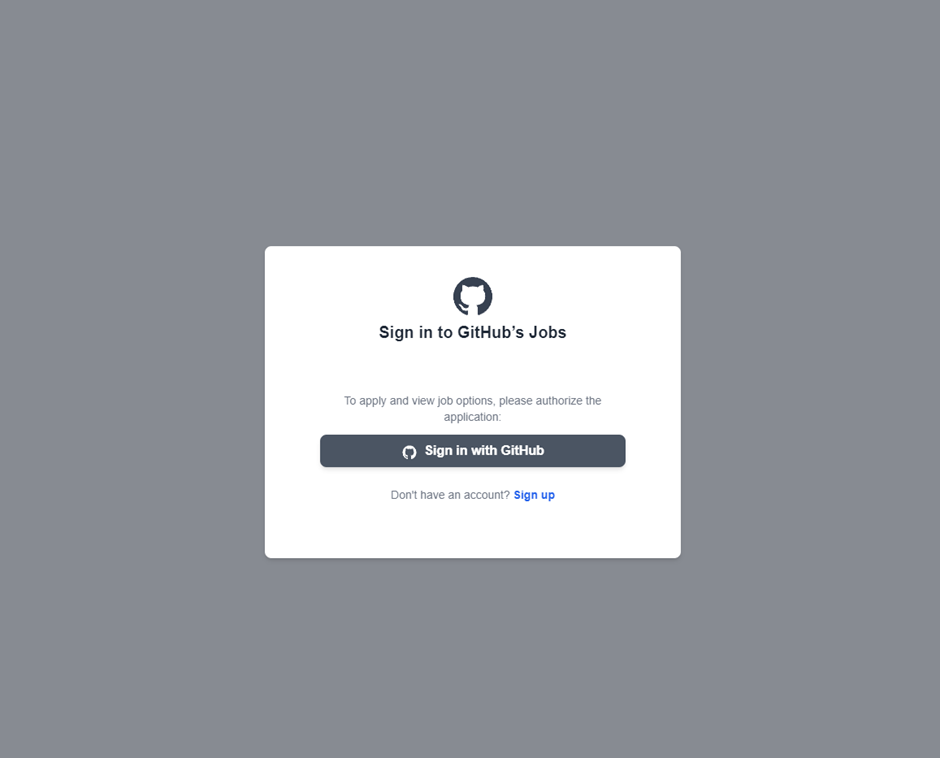
This malicious OAuth application requests extensive permissions, including access to private repositories, personal data, and the ability to delete repositories.
Another variant of the phishing email claims that GitHub has been hacked and requires the user’s authorization to mitigate the consequences. Both tactics aim to trick developers into granting dangerous permissions.
The Next Thing: Repository Wipe and Ransom Demand
If a developer falls for the scam and authorizes the malicious OAuth application, the attackers quickly exploit the granted permissions.
They wipe all the victim’s repositories and rename them, leaving behind only a README.me file.
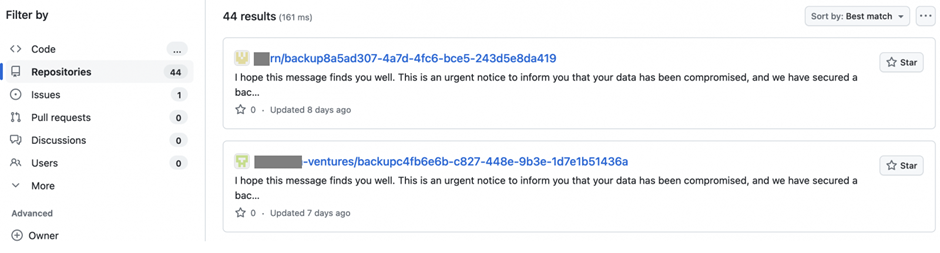
The README.me file contains a ransom note, stating that the data has been compromised but a backup exists.
To restore the data, the victim is instructed to contact a Gitloker user on Telegram.
These phishing emails are sent using the GitHub discussion system, leveraging already compromised accounts to tag multiple users, who then receive emails from the legitimate GitHub address.
How to Protect Against Such Attacks on GitHub Accounts
To safeguard against these sophisticated phishing attacks, developers should follow these recommendations:
- Scrutinize Email Details: Always check the details of an email, including the subject, text, and sender address. Discrepancies are likely signs of phishing.
- Avoid Clicking Suspicious Links: If you receive a suspicious email from GitHub, do not click any links. Report the email to GitHub support.
- Be Cautious with OAuth Applications: Never authorize unknown OAuth applications. Regularly review and remove any suspicious applications from your GitHub account.
By staying vigilant and following these guidelines, developers can protect their accounts and prevent potential data breaches.
Are you from SOC/DFIR Teams? - Sign up for a free ANY.RUN account! to Analyse Advanced Malware Files
