Researchers at Insikt Group have uncovered new infrastructure linked to multiple operational clusters associated with Israeli spyware vendor Candiru, revealing an ongoing campaign deploying the sophisticated DevilsTongue malware against Windows users across several nations.
The discovery highlights the persistent threat posed by commercial surveillance tools despite international regulatory efforts to curb their abuse.
The investigation identified eight distinct infrastructure clusters tied to Candiru’s operations, of which five are highly likely to be currently active.
Among these, clusters linked to Hungary and Saudi Arabia remain operational, while one cluster associated with Indonesia was active until November 2024.
Two additional clusters connected to Azerbaijan remain of uncertain status due to limited visibility into their victim-facing infrastructure.
Insikt Group’s analysis using Recorded Future Network Intelligence revealed significant variations in how these clusters are administered.
Some operators manage their victim-facing systems directly, while others employ intermediary infrastructure layers or route traffic through the Tor network to obscure their activities.
The infrastructure includes both victim-facing components used for deploying and controlling DevilsTongue, as well as higher-tier operator infrastructure.
High-Value Targets at Risk
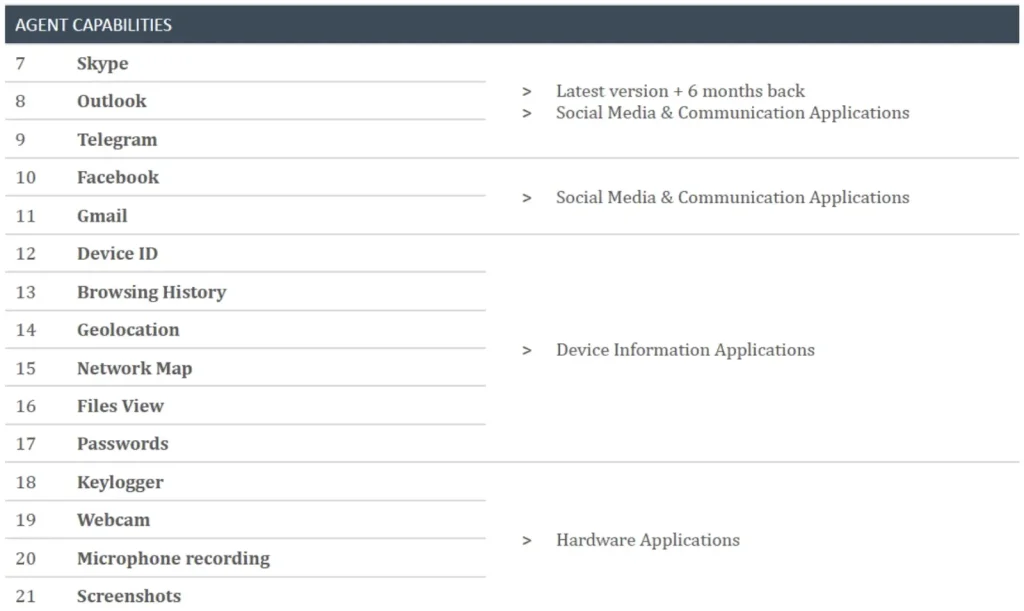
DevilsTongue is a sophisticated, modular Windows malware capable of deep device infiltration, file extraction, browser data collection, and theft of encrypted messages from applications like Signal.
The high cost per deployment estimated in the millions of euros based on leaked sales information means individuals with significant intelligence value are particularly at risk.
Politicians, business leaders, journalists, human rights defenders, and individuals in sensitive roles represent prime targets for operators wielding this technology.
The use of mercenary spyware outside serious crime or counterterrorism contexts poses substantial privacy, legal, and safety risks not only to targets and their organizations but also to the operators themselves.
Despite mounting international pressure, Candiru has demonstrated remarkable resilience. In November 2021, the US Department of Commerce added Candiru to its Entity List, citing its role in supplying spyware to foreign governments engaged in malicious activities.
The European Union has passed resolutions aimed at curbing spyware abuse, and the UK- and France-led Pall Mall initiative seeks to define and regulate legitimate surveillance tool use.
Nevertheless, Candiru continues operations and has actively pushed back against restrictions, including efforts to secure removal from the Entity List.
In April 2022, Citizen Lab reported that members of the Catalan independence movement had been targeted with Candiru spyware as part of a domestic surveillance operation.

The company’s frequent corporate restructuring operating under names including Saito Tech Ltd., Taveta Ltd., and Grindavik Solutions Ltd. has helped maintain operational secrecy.
Defensive Recommendations
Security defenders should implement comprehensive protective measures, including regular software updates, threat hunting for known indicators of compromise, pre-travel security briefings for at-risk personnel, and strict separation of personal and corporate devices.
The leaked Candiru project proposal outlining the spyware’s Windows-specific capabilities.
Employee security awareness training should address infection vectors and malware capabilities while promoting minimal data exposure practices.
Organizations facing elevated risk should invest in thorough risk assessments to develop adaptive security policies.
As the mercenary spyware market expands with new vendors and more countries seeking advanced cyber capabilities, the risk of targeting now extends beyond civil society to anyone of interest to actors with access to such tools.
Innovation continues accelerating, with emerging techniques including alleged ad-based infections, direct attacks on messaging servers, and enhanced persistence mechanisms.
These developments are driving stealthier infection chains, targeting of cloud backups, and broader tool portfolios across an increasingly professionalized spyware ecosystem.
Effective mitigation requires continuous ecosystem monitoring and more decisive regulatory action from policymakers worldwide.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
