Acronis Threat Research Unit has analyzed recent activity linked to the DragonForce ransomware group and identified a new malware variant in the wild.
The latest sample uses vulnerable drivers such as truesight.sys and rentdrv2.sys to disable security software, terminate protected processes and correct encryption flaws previously associated with Akira ransomware.
The updated encryption scheme addresses weaknesses publicly detailed in a Habr article cited on DragonForce’s leak site, demonstrating the group’s commitment to maintaining operational security and technical superiority.
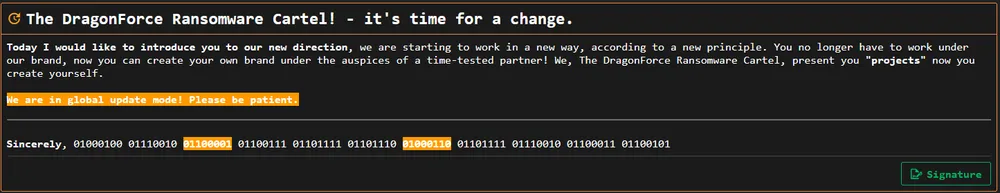
Recently, DragonForce announced a rebrand, stating that the group would now operate as a ransomware cartel.
By offering affiliates 80 percent of profits, customizable encryptors and infrastructure, DragonForce lowers the barrier to entry and encourages more affiliates to join.
Since then, DragonForce has been more active in attacking companies globally, posting significantly more victims compared to a year ago. Their most notable attack targeted retailer Marks & Spencer in collaboration with Scattered Spider.
Rise of DragonForce and Cartel Operations
DragonForce is a ransomware-as-a-service group that first appeared in 2023 and was initially associated with the hacktivist group DragonForce Malaysia, though concrete evidence linking the two remains limited.
The group started using the leaked LockBit 3.0 builder to develop its encryptors, then later adopted a customized Conti v3 code base.
In early 2025, DragonForce began branding itself as a ransomware cartel. This approach allows DragonForce to continue building its brand as one of the most notorious cybercriminal groups currently active.
Through its affiliate program, DragonForce strengthened its position in the ransomware scene, attracting new partners and competing with more established RaaS operators.
Affiliates can deploy their own malware while using DragonForce’s infrastructure and operating under their own brand.
This lowers the technical barrier and allows both established groups and new actors to run operations without building a full ransomware ecosystem.
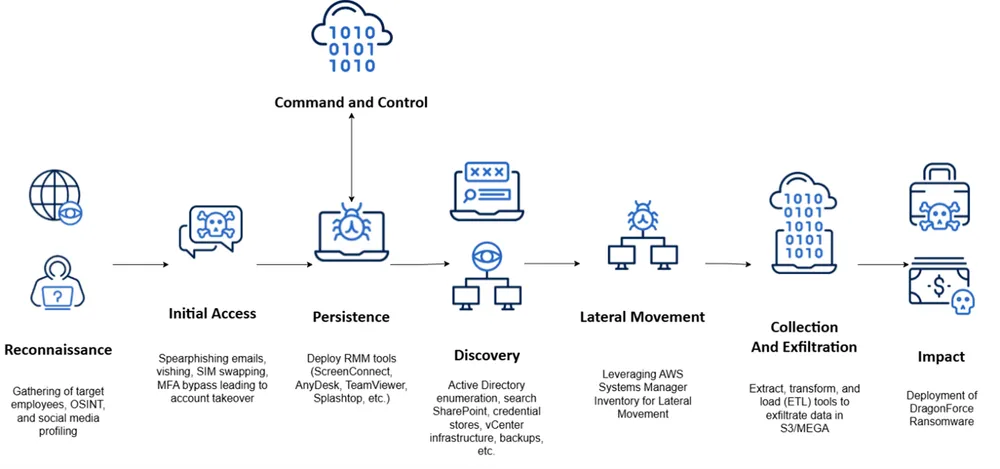

Among DragonForce’s partners is Scattered Spider, an initial access broker known for phishing, SIM swapping and MFA bypass. The group’s campaigns have produced many victims, including well-known organizations such as Marks & Spencer and Harrods.
Technical Evolution and BYOVD Attacks
DragonForce employs bring your own vulnerable driver (BYOVD) attacks by using truesight.sys and rentdrv2.sys drivers to terminate processes and disable security software.
DragonForce supports two driver backends that must be present on the victim host beforehand: Truesight and BadRentdrv2.

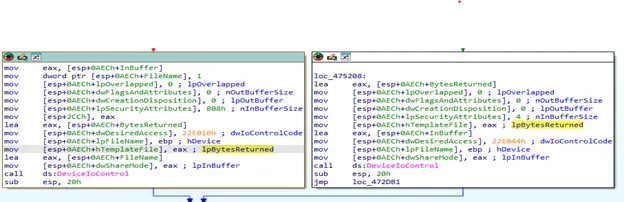
By sending proper control codes to those drivers through DeviceIoControl, operators can cause the drivers to terminate specified processes, effectively neutralizing endpoint detection and response solutions.
After an article appeared in Habr—a media platform focused on technology and internet culture—revealed weaknesses in Akira’s encryption, DragonForce quickly reinforced its own encryptor to avoid similar problems.

The encryption scheme uses a single ChaCha20 encryption key generated for each file, which is then encrypted using a public RSA key and appended at the beginning of the resulting file.
DragonForce and LockBit Green share common lineage through the leaked Conti v3 code, leading to overlaps in routines and artifacts. The analyzed code shows extensive overlap with Conti’s leaked source files, including initialization processes and API manipulation techniques.
Growing Threat Landscape
More than 200 victims have been exposed on DragonForce’s leak site since late 2023, across retail, airlines, insurance, managed service providers and other enterprise sectors.
This collaboration between Scattered Spider and DragonForce evolved into broader overlaps with LAPSUS$ and ShinyHunters, forming what researchers dubbed the Scattered LAPSUS$ Hunters within the Hacker Com ecosystem.
DragonForce has also been linked to affiliates creating variants like Devman and Mamona/Global, while defacing rival groups to reinforce its position in the ecosystem.
By rebranding itself as a cartel, DragonForce aimed to strengthen its influence in the ransomware landscape, proving its dominance by defacing or taking control of rival infrastructure, including attempts against BlackLock and RansomHub.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.





