A cybercriminal group obtained contracts from cybersecurity firm Dragos Inc. as part of an extortion attempt that involved contacting the chief executive officer’s wife and 5-year-old kid.
For industrial control systems, including power grids, water treatment facilities, and pipelines, Dragos excels in offering cybersecurity services.
According to the reports, a newly hired Dragos salesperson’s email account was compromised, giving hackers access to internal documents. The company didn’t compensate the hackers, CEO Robert M. Lee.
No Dragos systems were compromised, including those connected to the Dragos Platform.

Cybercriminal Group Attempted And Failed At An Extortion Scheme
On May 8, a “known criminal group attempted and failed at an extortion scheme against Dragos,” according to the blog. Dragos didn’t mention who the hackers were.
According to Lee, the hackers called Lee’s kid using a phone he used to call his grandma as part of the extortion effort. The boy handed his mother the phone, who then hung up. According to him, the hackers called Lee’s wife separately.
“The criminal group gained access by compromising the personal email address of a new sales employee before their start date, and subsequently used their personal information to impersonate the Dragos employee and accomplish initial steps in the employee onboarding process,” the blog said.
The intranet software and Dragos contract management system were among the resources the hackers accessed that a new sales employee would typically use.
Dragos stopped the hackers from deploying ransomware, which was thought to be their primary objective, and from further infiltrating the company’s network.
The company said that in one instance, a report with IP addresses associated with a customer was accessed, and they contacted the customer.
The firm executives approached by the hackers on WhatsApp declined to respond.
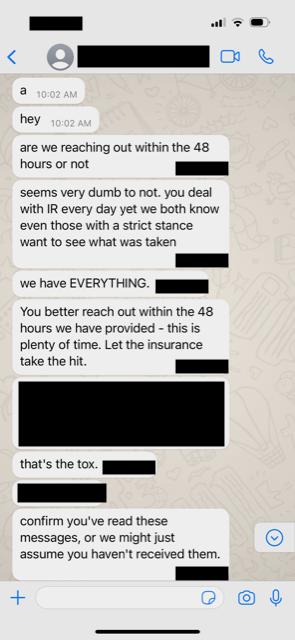
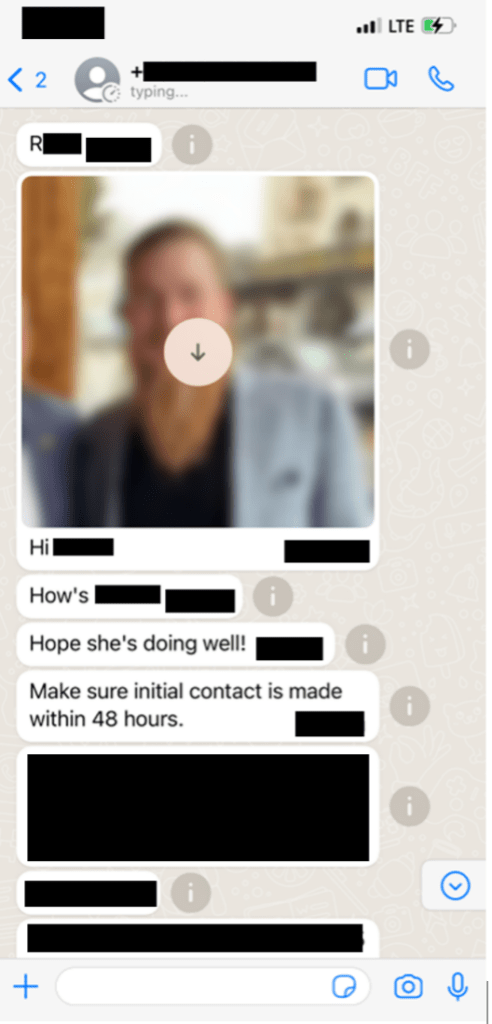
Cybercriminals have begun contacting business executives and occasionally family members to put more pressure on hacking victims to pay an extortion price, according to cybersecurity officials.
Bloomberg News approached a hacker. The hacker confirmed contacting Lee’s wife but denied contacting Lee’s son. 130 gigabytes of files were taken from the business.
“The hacker provided Bloomberg with a copy of a contract between Dragos and the 67th Cyberspace Wing of the US Air Force outlining a research and development agreement”, Bloomberg reports.
The agreement for Dragos to get network information on the Department of Defense’s industrial control system environment is outlined in the six-page document.
Lee attested to the validity of the contract. A 67th Cyberspace Wing representative declined to comment.
Dragos claimed it introduced an additional verification step “to further harden our onboarding process and ensure that this technique cannot be repeated.”
Hence, wherever possible, use multi-factor authentication. Examine receiving emails carefully for common phishing indicators, such as the email address, URL, and spelling, and make sure there is ongoing security monitoring and that there are tested incident response playbooks in place.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus




