Earth Preta, also known as Mustang Panda, Bronze President, RedDelta, and Red Lich, is a sophisticated Chinese APT group that has been active since at least 2012.
They are known for targeting government entities, academic institutions, foundations, and research sectors globally. However, the focus of this group is on the Asia-Pacific region.

Trend Micro researchers recently discovered that Earth Preta hackers added new tools to their arsenal.
Earth Preta Hackers
Earth Preta APT group has evolved its cyberattack strategy, as it’s been observed by researchers that they are now using a variant of the HIUPAN worm to disseminate PUBLOAD malware via removable drives.
Decoding Compliance: What CISOs Need to Know – Join Free Webinar
This denotes a major shift from their previous spear-phishing tactics. PUBLOAD serves as the primary control tool, executing various tasks like data gathering using RAR and exfiltration via cURL to FTP sites.
The group has introduced additional tools like FDMTP, it’s a malware downloader that is based on TouchSocket over DMTP, and this acts as a secondary control tool.
While the PTSOCKET offers an alternative exfiltration method. HIUPAN installs itself and PUBLOAD in the C:ProgramDataIntel_ directory, which helps in creating autorun registry entries for persistence.
.webp)
The PUBLOAD is installed in C:ProgramDataCocCocBrowser, and this performs network surveillance using system commands like ‘ipconfig’, ‘netstat’, and ‘systeminfo’.
Besides this, it also delivers supplementary tools to compromised systems. While the attackers focus on government entities in the region and target the files with the following extensions:-
- .doc
- .docx
- .xls
- .xlsx
- .ppt
- .pptx
This multi-stage attack shows the increased sophistication in malware deployment and data theft techniques, as read in the Trend Micro report.
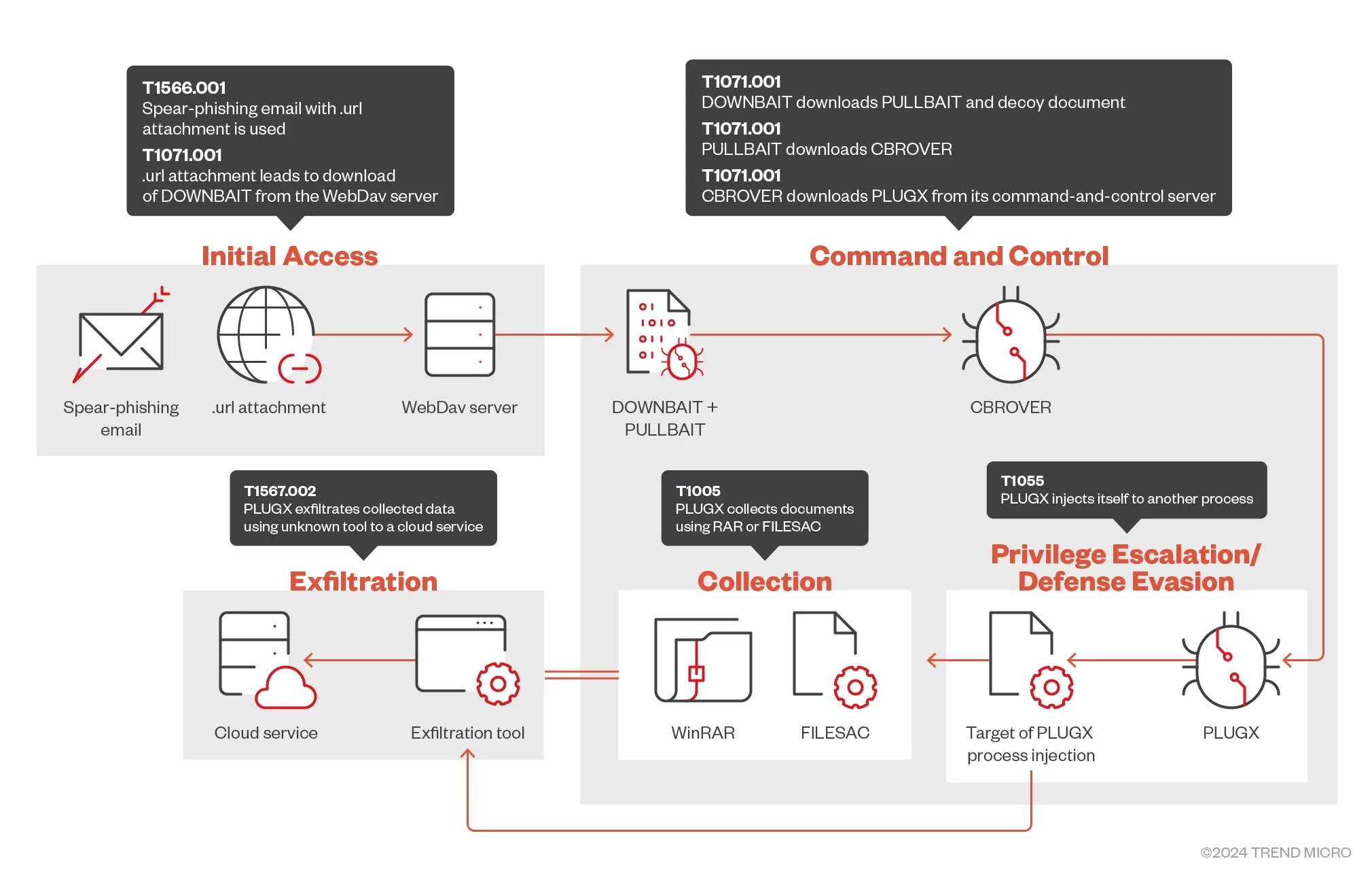
Their campaign begins with a spear-phishing email containing a .url attachment, which triggers a multi-stage malware deployment process.
.webp)
First, a signed downloader tool is executed which is dubbed “DOWNBAIT.” It uses multi-layered XOR encryption and downloads a decoy document and PULLBAIT which is a shellcode component.
PULLBAIT then downloads and executes CBROVER by utilizing DLL side-loading. CBROVER is a first-stage backdoor that deploys PLUGX, a more advanced backdoor.
PLUGX comes in two stages, the second being protected by “RC4 encryption” and “Data Protection API (DPAPI).”
For data gathering, the threat actors use either a RAR command-line tool or FILESAC, which is a modified version of “FileSearchAndCompress.”
All these tools target specific file types and date ranges. The collected data is exfiltrated using Microsoft’s cloud services (OneDrive) and Graph API.
The attack infrastructure includes a WebDAV server at “16.162.188.93,” which hosts the malware and decoy documents.
This campaign illustrates the evolving tactics of Earth Preta in fast-paced operations and sophisticated evasion techniques, which pose a significant threat to various sectors.
Download Free Incident Response Plan Template for Your Security Team – Free Download
