GhostSec ransomware group, in collaboration with the notorious Stormous ransomware collective, has reportedly claimed to have launched the Econocom group ransomware attack.
The alleged Econocom group ransomware attack has exposed a substantial 70GB of sensitive company data, including sensitive information about the company.
A post on the dark web seemed to validate the occurrence of the Econocom Group ransomware attack and the hacker group’s unauthorized entry into the company’s digital infrastructure.
The statement read, “GhostSec & STORMOUS: Proudly announcing our latest achievement—a joint blog representing our collaborative efforts. We have successfully infiltrated the Econocom Group, gaining access to over 70GB of invaluable company data.”
The group further claimed that some of the preliminary samples have already been published on their blog.
Two Threat Actors Behind Econocom Group Ransomware Attack

The perpetrators behind the Econocom group ransomware attack also included a URL, /econocom.html, pointing readers to their online hub where the pilfered data and samples from the alleged ransomware attack are posted.
Notably, the breached data encompasses sensitive information, including passwords, project details, messages, plans, reports, relationships, files, and documents—detailing the profound extent of the potential damage.
The Cyber Express has reached out to the company to confirm the Econocom group ransomware attack. However, at the time of writing, an official response or confirmation was yet to be received, leaving the Econocom group ransomware attack claims unverified.
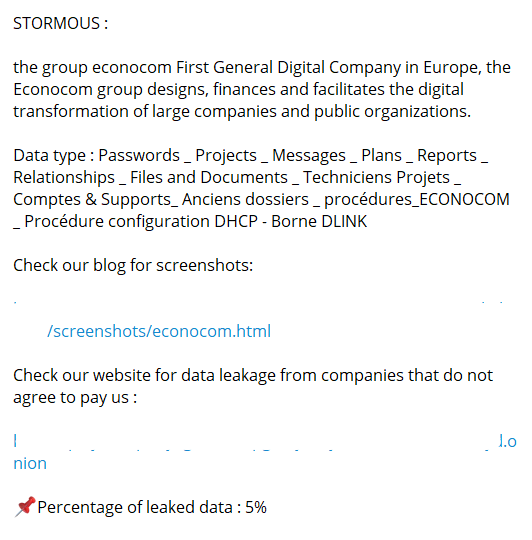
STORMOUS, the hacker collective that has joined forces with GhostSec, elucidates the significance of the Econocom Group in their post.
The Econocom Group is recognized as Europe’s premier digital transformation facilitator, partnering with large corporations and public entities to orchestrate their technological evolution.
The stolen data spans various categories, from project-related details to account information, offering a broad picture and the magnitude of the Econocom group ransomware attack.
The leaked data includes passwords, project specifications, communication records, strategic plans, and even technical details.
To substantiate their claims, the hackers released screenshots of the stolen data on their blog, /screenshots/econocom.html, where users can check out the stolen data.
Econocom group ransomware attack: GhostSec and Stormous partnerships intensifies
The situation is further compounded by the timing of the breach, following an earlier alliance between the GhostSec and Stormous groups.
This collaboration, established in July 2023, aimed to target Cuba, signaling the potential expansion of their attacks to a global scale.
The threat actors announced their joint operation, emphasizing their dedication to Operation Cuba while expressing aspirations for future cyber attacks.
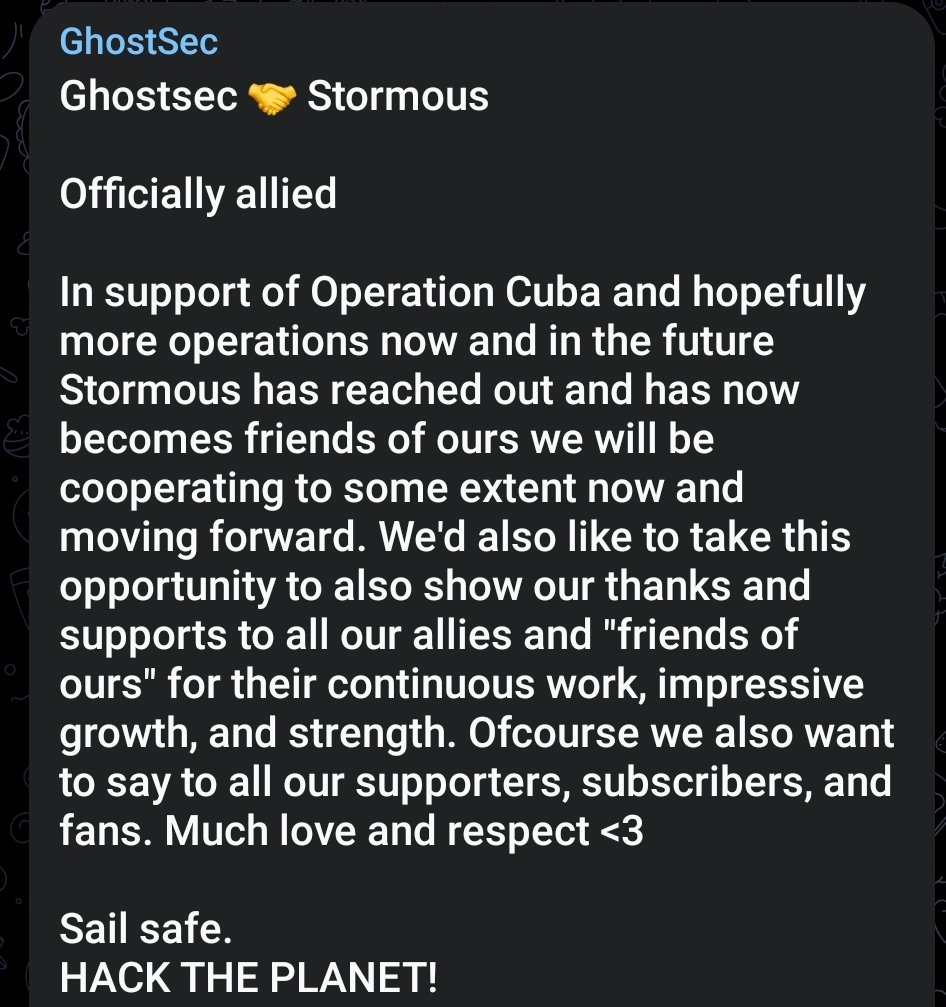
The collaboration was announced on their dark web channel, where the threat actor, Ghostsec, stated, “Officially allied, in support of Operation Cuba and hopefully more operations now and in the future.
The Stormous group also announced their plans to target the Ministry of Culture of the Republic of Cuba.
Stormous shared the victims’ names in this cyber attack, including the Department of Culture, the Ministry of Education, and the National Council for Culture.

As for the Econocom group ransomware attack, we’re yet to see any official confirmation. However, the threat actor has already claimed to have posted over 70GB of the company’s data on their data leak site.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
