Ransomware is shifting from traditional systems to cloud environments, fundamentally redefining its impact on cloud-native data.
As organizations increasingly migrate to cloud platforms, threat actors are adapting their tactics moving away from traditional encryption-based malware to exploit the unique architecture and misconfiguration vulnerabilities inherent in cloud storage services.
Cloud storage services like Amazon Simple Storage Service (S3) remain attractive targets due to potential customer misconfigurations on bucket settings and access controls.
Unlike ransomware targeting on-premises environments, cloud-focused variants often leverage native cloud features to delete or overwrite data, suspend access, or extract sensitive content all while remaining under the radar of traditional security tools.
Security researchers have documented five distinct S3 ransomware variants, combining both observed attack techniques and potential future vectors.
These variants demonstrate the sophistication of cloud-native attack strategies and the critical importance of proper AWS configuration.
Variant 1 leverages default AWS KMS keys with SSE-KMS encryption, where attackers create customer-managed keys accessible to multiple AWS accounts, then encrypt victim data and schedule key deletion within a seven-day window.
While theoretically viable, this variant is unlikely in real-world scenarios due to the possibility of AWS support intervention.
Variant 2, attributed to threat actor Codefinger, utilizes server-side encryption with customer-provided keys (SSE-C).

This variant proved highly effective because attackers control the encryption key directly, leaving both customers and AWS with no recovery options.
AWS logs only the HMAC of the key not the key itself making decryption impossible even with AWS support intervention.
Variant 3 abandons encryption entirely, instead employing data exfiltration combined with deletion. Threat actors steal AWS credentials, copy sensitive data to their own environments, then delete the original S3 bucket contents.
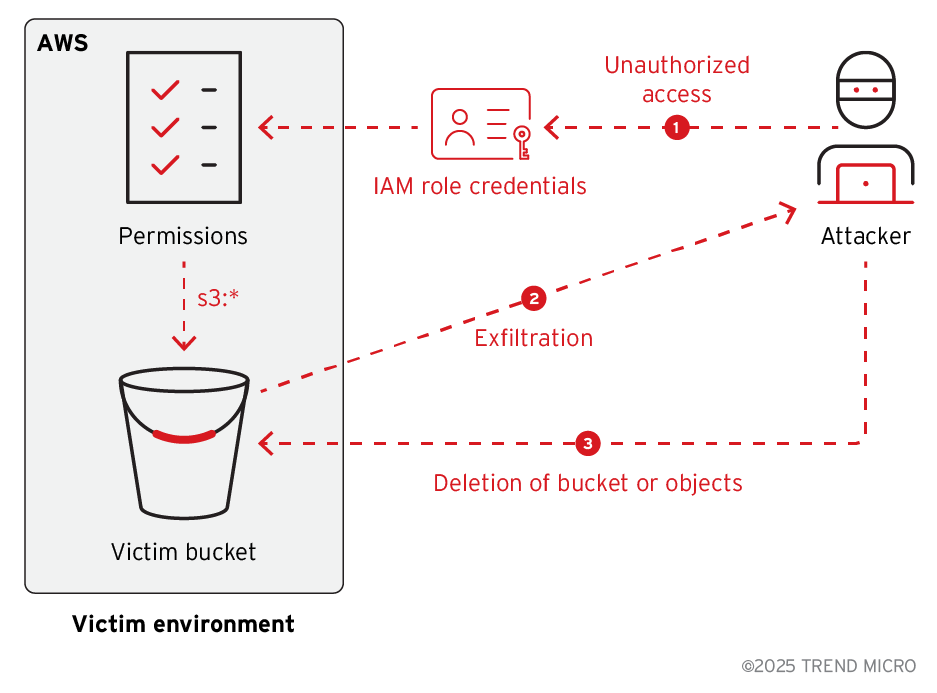
This straightforward approach remains highly likely to occur in real-world campaigns.
Variant 4 exploits AWS KMS External Key Material through the Bring Your Own Key (BYOK) process.
Attackers import their own key material, set short expiration windows, and encrypt S3 buckets with keys that expire rapidly rendering data permanently inaccessible to both customers and AWS.
Variant 5 abuses the KMS External Key Store (XKS) feature, which enables customers to store cryptographic keys entirely outside AWS.
Attackers deploy XKS proxy implementations using tools like ngrok to tunnel local services through public HTTPS endpoints, creating encryption keys that never exist within AWS infrastructure.
Detection and Defense
Trend Vision One provides critical visibility into AWS CloudTrail events to detect and respond to active ransomware activity.
The platform includes variant-specific detections alongside generic pre- and post-attack phase indicators, enabling organizations to identify compromise attempts before encryption occurs.
Attackers tend to keep the expiration window as small as possible to destroy the key and keep it out of reach of AWS.
Key detections include AWS S3 ransomware activity patterns, unusual encryption configurations, bulk download and deletion sequences, and suspicious IAM privilege escalations.
Over 28 dedicated S3 security rules monitor for misconfigurations including disabled MFA Delete, missing Object Lock, and enabled SSE-C usage.
Organizations must adopt layered security controls tailored explicitly to cloud infrastructure.
Critical measures include enforcing least-privilege access through IAM policies, hardening KMS governance to restrict cross-account operations, enabling S3 Object Lock and versioning to prevent overwrites, and maintaining multi-factor authentication requirements for sensitive operations.
Backup isolation through cross-account replication with separate CMKs ensures clean recovery options, while continuous CloudTrail monitoring enables rapid detection of anomalous activity.
Regular recovery testing validates restoration capabilities and identifies configuration drift before incidents occur.
As AWS emphasizes through its shared responsibility model, defenders must assume an active security posture management rather than relying solely on cloud provider protections.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
