14 Feb Empowering SOC Teams with Open and Seamless API Integration
in Blogs
Boosting SOC Efficiency with Open XDR and API Integration
– Peter Luo, Director of Product Management, Stellar Cyber
San Jose, Calif. – Feb. 13, 2025
Today’s complex cyberthreat landscape poses both enterprises and Managed Security Service Providers (MSSPs) multiple challenges. To combat evolved threats across diverse IT & Security environments, cybersecurity professionals develop an array of tools and data sources to monitor their specific threat landscape. However, the tool array presents its own difficulties, as there are gaps in visibility, high demands of small analyst teams, and redundancies in functionality. The following blog will explore ways in which you can enhance your security operations without creating additional burden to your analyst team.
Why Openness Matters for SOC Teams
No single cybersecurity tool is infallible. SOC analysts and MSSPs rely on a diverse set of solutions to monitor, detect, and respond to threats. Rather than contribute an additional redundant tool, Stellar Cyber’s Open XDR platform:
- Integrates seamlessly with your existing security stack.
- Supports multiple data ingestion methods to accommodate diverse environments.
- Enables customization to meet unique operational needs of each SOC team.
At Stellar Cyber, we don’t believe in locking you into a proprietary ecosystem. Instead, we provide the tools and flexibility to adapt to your environment, ensuring you can leverage the best solutions for your needs.
The Role of APIs in Modern SOC Teams
An API (Application Programming Interface) is a set of protocols and tools that enable different software applications to communicate with each other. APIs serve as the glue that binds your security ecosystem together, facilitating data sharing, automation, and orchestration. They are the backbone of modern cybersecurity, enabling systems to communicate, share data, and execute actions programmatically.
APIs are deeply embedded in every aspect of modern SOC operations, often working behind the scenes to ensure seamless collaboration between tools and teams.
“Within Brite’s Security Operations Center (SOC), API logging is essential for continuous security monitoring and incident response, enabling organizations to effectively defend against incidents potentially leading to a breach,” says Jon-Michael Lacek, CTO at Brite. “Over time, API logging has transitioned from a fundamental tool to a critical element of cybersecurity defense. With the ongoing shift toward SaaS and cloud-based solutions, the ability to access and analyze security logs from applications is increasingly imperative. Additionally, the capacity to leverage APIs for real-time response actions—such as mitigating threats—is a key area where Brite’s analysts guide customers to enhance playbook maturity, significantly reducing the potential for lateral movement by malicious actors within the network.”
Challenges of Integration
Despite their critical role, achieving seamless API integration is no easy task. Common challenges include:
- Different Protocols/Syntax: Variability in API standards, such as REST, GraphQL, or SOAP, or completely proprietary
- Different Parameters/Semantics: Lack of uniformity in how data is structured, defined or passed.
- Authentication Mechanisms: Diverse methods like OAuth, API keys, or token-based authentication.
- Inconsistent Practices: Many vendors do not adhere to consistent or transparent API practices, making integrations cumbersome.
Stellar Cyber addresses these challenges by simplifying the integration process and ensuring compatibility across diverse technologies.
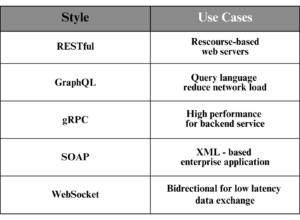
Variety kinds of API Protocols and Specifications
In practice, There are several types of APIs, each designed for specific use cases:
- RESTful API: A lightweight, widely-used protocol for web services.
- GraphQL: A query language that allows clients to request exactly the data they need, reducing network latency.
- gRPC: A high-performance protocol for microservices, using Protocol Buffers for data serialization.
- SOAP: A legacy protocol for structured information exchange, often used in enterprise systems.
- WebSocket: A protocol for real-time, bidirectional communication, ideal for low-latency applications.
While RESTful APIs are the most common in security tool integrations, some tools also use GraphQL or other protocols.

Variety kinds of API Authentication Mechanisms
Different vendors use various authentication methods to ensure secure communication. Common mechanisms include:
- OAuth 2.0: The industry standard for authorization, allowing secure access to resources.
- Basic Authentication: A simple method using a username and password, often encoded in Base64.
- Token Authentication: Uses tokens (e.g., JWTs) to verify identity and permissions.
- API Key Authentication: A straightforward method where a unique key is used to authenticate requests.
- Access Key/Secret Key: A pair of keys used for authentication and authorization.
Variety kinds of API Standards: The Foundation of Interoperability
API standards ensure consistency, interoperability, and ease of use. There are a variety of API standards over the years. The OpenAPI Specification (OAS), formerly known as Swagger, is the most widely adopted standard for defining RESTful APIs. However, there are alternatives, such as:
- RAML: A YAML-based language for describing RESTful APIs.
- API Blueprint: A Markdown-based language for API documentation.
Inconsistent quality of APIs among different vendors
The quality of APIs can vary significantly across vendors, creating challenges for seamless integration and interoperability. A well-designed API is critical for ensuring smooth communication between systems and reducing the burden on SOC teams. Key characteristics of a high-quality API include:
- Proper Versioning: Ensures backward compatibility, allowing systems to evolve without breaking existing integrations.
- Clear Documentation: Provides easy-to-understand guidelines, examples, and use cases, enabling developers to implement integrations quickly and accurately.
- Robust Error Handling: Delivers meaningful error codes and messages to help diagnose and resolve issues efficiently.
- Throttling and Limits: Prevents abuse and ensures system stability by controlling the rate of API requests.
- Clean, Nested Results: Structures data in a logical, easy-to-parse format, reducing the complexity of processing and analysis.
Unfortunately, not all vendors adhere to these best practices, leading to inconsistent API quality. Poorly designed APIs can result in integration headaches, increased development time, and operational inefficiencies.
APIs: The Foundation for Innovation
As we enter the era of AI-driven SOCs, APIs are more critical than ever. Whether it’s for automation, Gen AI, or AI-based SOC operations, APIs are the fundamental components that enable innovation. At Stellar Cyber, we’re embracing this integration-driven future, making it easier for you to automate, orchestrate, and collaborate across your security ecosystem. With APIs at the core of our platform, we’re empowering SOC teams to quickly remediate risks, streamline workflows, and stay ahead of evolving threats.
Conclusion
In a world where cybersecurity threats are constantly evolving, cybersecurity analysts need to adopt the most strategic and efficient solution to combat any kind of threat at any point in their IT & security landscape. An open and flexible XDR platform is no longer a luxury—it’s a necessity. Stellar Cyber’s Open XDR Platform, powered by a robust API foundation, empowers SOC analysts and MSSPs to integrate, innovate, and respond with confidence.
Ready to experience the power of seamless integration? Contact us today to learn more about how Stellar Cyber can transform your security operations.
– Peter Luo is the Director of Product Management at Stellar Cyber.

 About Stellar Cyber
About Stellar Cyber
Stellar Cyber’s Open XDR Platform delivers comprehensive, unified security without complexity, empowering lean security teams of any skill level to secure their environments successfully. With Stellar Cyber, organizations reduce risk with early and precise identification and remediation of threats while slashing costs, retaining investments in existing tools, and improving analyst productivity, delivering an 8X improvement in MTTD and a 20X improvement in MTTR. The company is based in Silicon Valley. For more information, visit https://stellarcyber.ai.
