A threat actor tracked as ‘EncryptHub,’ aka Larva-208, has been targeting organizations worldwide with spear-phishing and social engineering attacks to gain access to corporate networks.
According to a report by Prodaft, which was published internally last week and made public yesterday, since June 2024, when EncryptHub initiated operations, it has compromised at least 618 organizations.
After gaining access, the threat actors install Remote Monitoring and Management (RMM) software, followed by the deployment of information stealers like Stealc and Rhadamanthys. In many observed cases, EncryptHub also deploys ransomware on compromised systems.
Prodaft told BleepingComputer that the threat group is affiliated with RansomHub and BlackSuit, having deployed both ransomware encryptors in the past and possibly acting as an initial access broker for them or a direct affiliate.
However, in many attacks the researchers observed, the threat actors deployed a custom PowerShell data encryptor, so they maintain their own variant too.
Gaining initial access
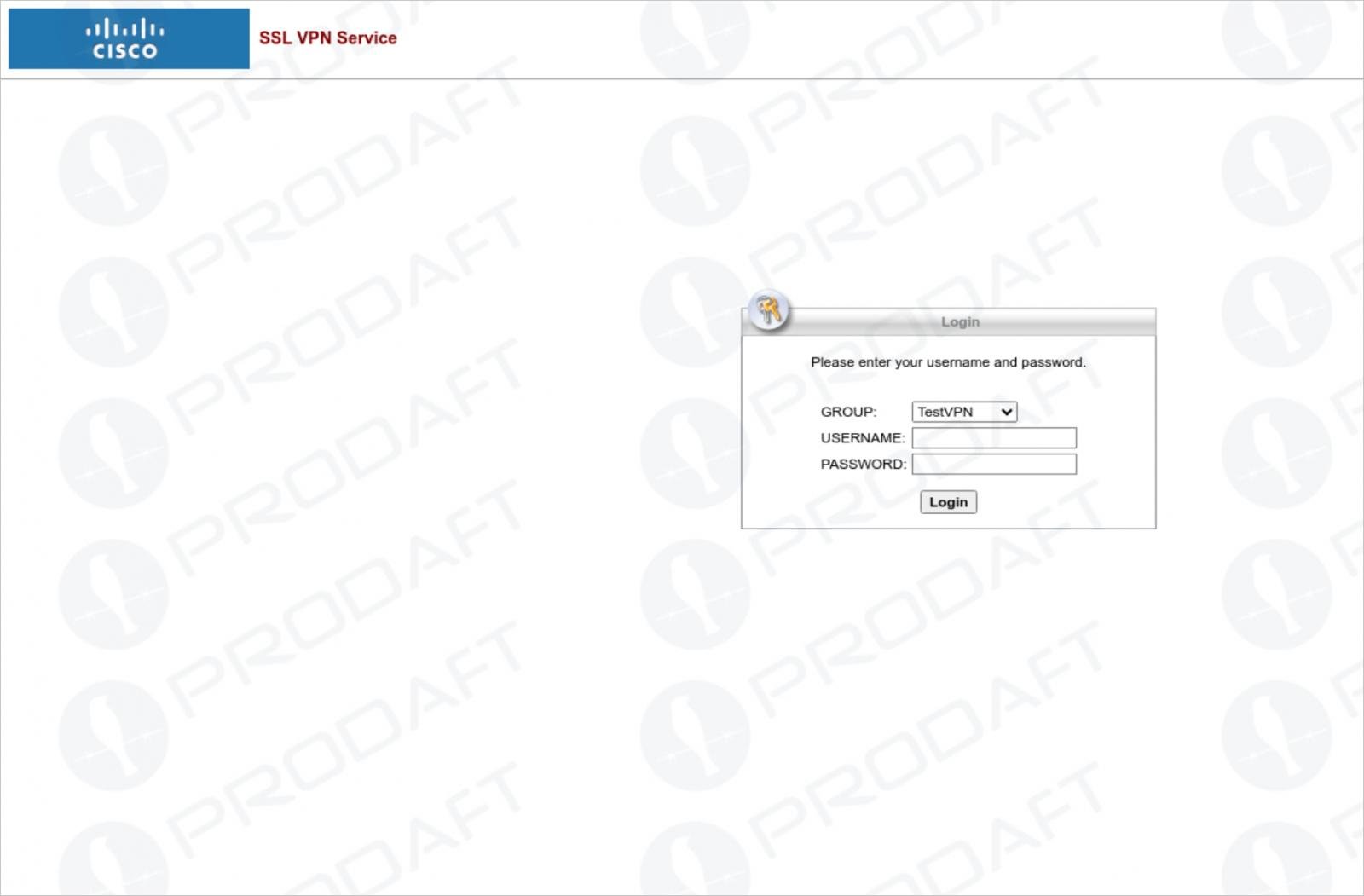
Larva-208’s attacks involve SMS phishing, voice phishing, and fake login pages that mimic corporate VPN products like Cisco AnyConnect, Palo Alto GlobalProtect, Fortinet, and Microsoft 365.
Source: Prodaft
The attackers typically impersonate IT support in their messages to the targets, claiming an issue with VPN access or a security concern with their account, directing them to log in on a phishing site.
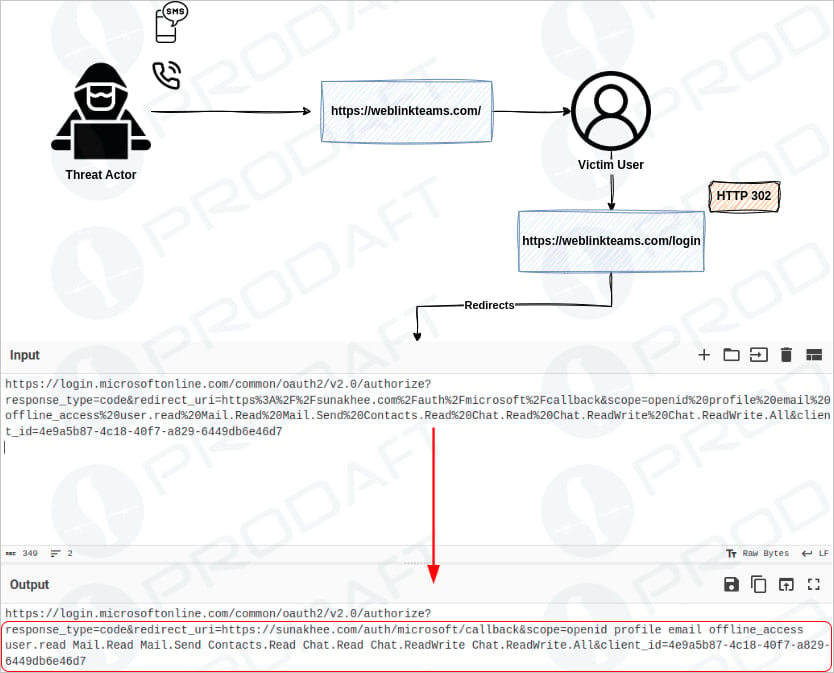
Victims receive links that redirect them to phishing login pages where their credentials and multi-factor authentication (MFA) tokens (session cookies) are captured in real-time.
Once the phishing process is over, the victim is redirected to the service’s real domain to avoid raising suspicion.
Source: Prodaft
EncryptHub has bought over 70 domains that mimic the said products, such as ‘linkwebcisco.com’ and ‘weblinkteams.com,’ to increase the perceived legitimacy of the phishing pages.
The phishing sites are hosted on bulletproof hosting providers like Yalishanda, which ProDaft says does not typically respond to justified takedown requests.
Prodaft has also discovered there’s another subgroup tracked as Larva-148, which helps purchase the domains used in the phishing campaigns, manage hosting, and set up the infrastructure.
It’s possible that Larva-148 sells domains and phishing kits to EncryptHub, though their exact relationship hasn’t been deciphered yet.
Deploying malware
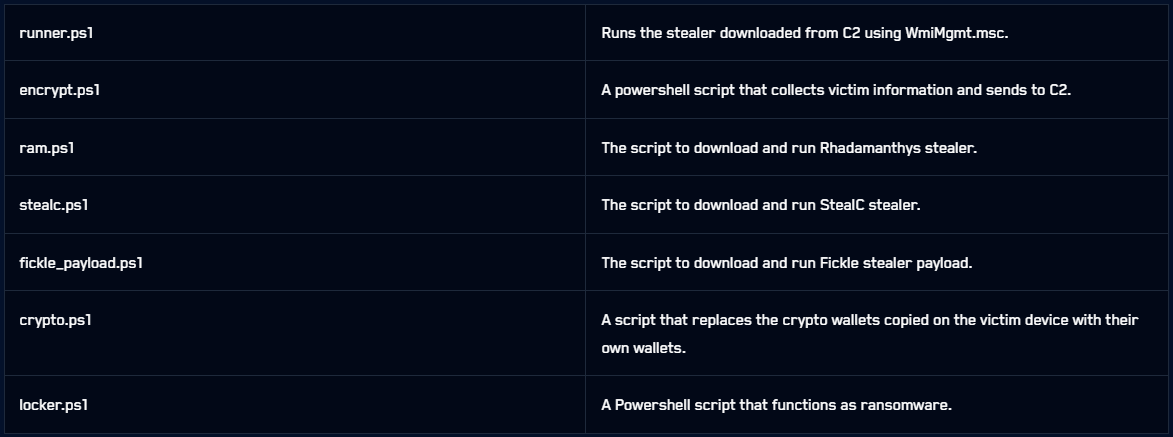
Once EncryptHub breaches a targeted system, it deploys various PowerShell scripts and malware to gain persistence, remote access, steal data, and encrypt files.
First, they trick victims into installing RMM software like AnyDesk, TeamViewer, ScreenConnect, Atera, and Splashtop. This allows them to control the compromised system remotely, maintain long-term access, and make lateral movement possible.
Next, they use different PowerShell scripts to deploy infostealers, such as Stealc, Rhadamanthys, and Fickle Stealer, to steal data stored in web browsers. This data includes saved credentials, session cookies, and cryptocurrency wallet passphrases.
Source: Prodaft
BleepingComputer has also seen Python scripts that perform similar behavior for Linux and Mac devices.
In samples of the scripts seen by BleepingComputer, the threat actor attempts to steal a large amount of data from breached systems, including:
- Data from various cryptocurrency wallets, including MetaMask, Ethereum Wallet, Coinbase Wallet, Trust Wallet, Opera Wallet, Brave Wallet, TronLink, Trezor Wallet, and many others.
- Configuration data for various VPN clients, including Cisco VPN Client, FortiClient, Palto Alto Networks GlobalProtect, OpenVPN, and WireGuard.
- Data from popular password managers, including Authenticator, 1Password, NordPass, DashLane, Bitwarden, RoboForm, Keeper, MultiPassword, KeePassXC, and LastPass.
- Files that match particular extensions or whose names contain certain keywords, including images, RDP connection files, Word documents, Excel spreadsheets, CSV files, and certificates. Some of the keywords in file names that are targeted include “pass”, “account”, “auth”, “2fa”, “wallet”, “seedphrase”, “recovery”, “keepass”, “secret”, and many others.
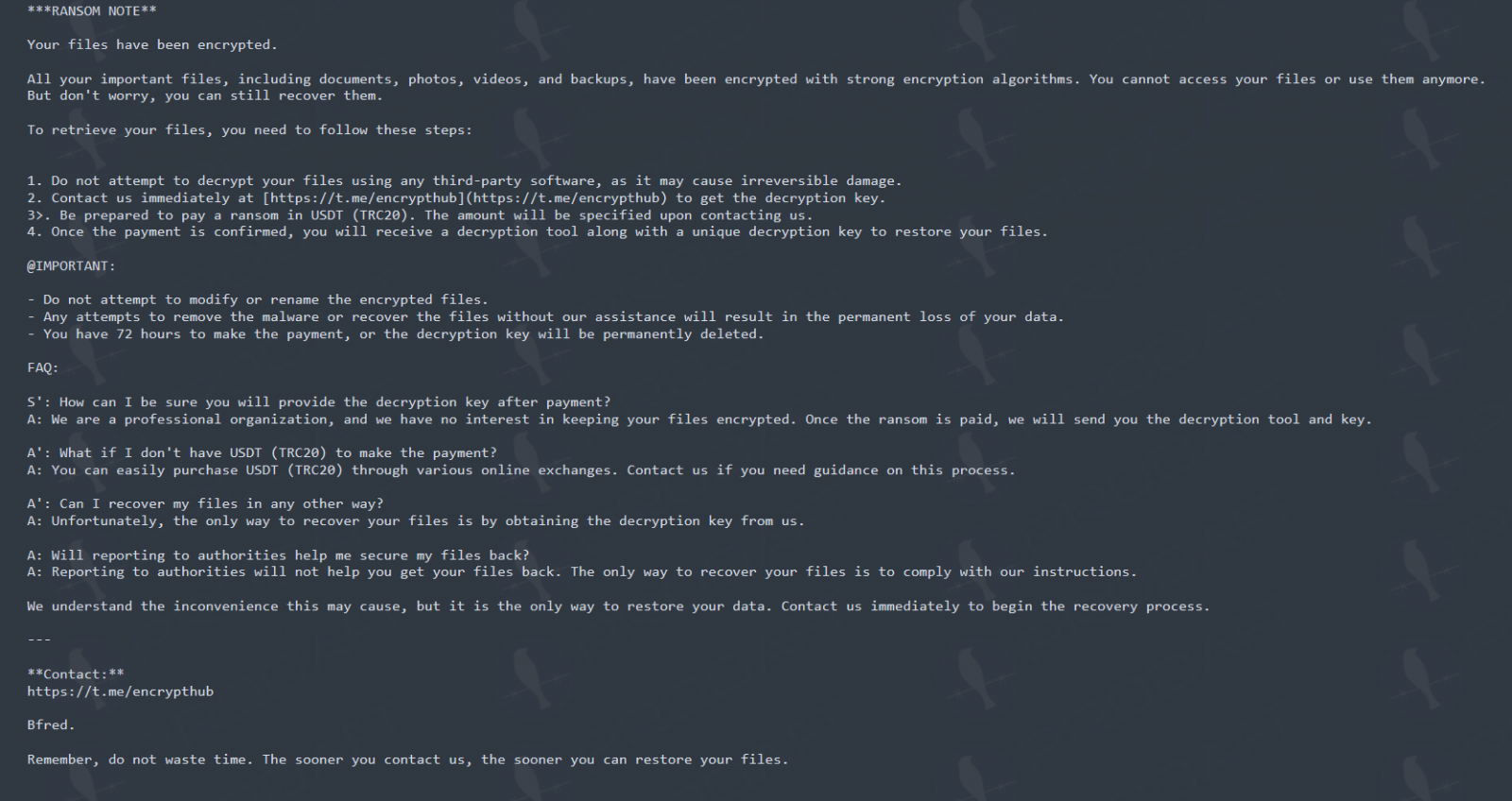
Larva-208’s final threat is ransomware in the form of a custom PowerShell-based encryptor that encrypts files using AES and appends the “.crypted” extension, deleting original files.
A ransom note is generated for the victims, demanding a ransom payment in USDT via Telegram.
Source: Prodaft
Prodaft says EncryptHub is a sophisticated threat actor that tailors its attacks for better effectiveness, achieving high-value breaches on large organizations.
“The LARVA-208 spear-phishing actor examined in this report exemplifies the increasing sophistication of targeted cyber attacks,” warns Prodaft.
“By employing highly customized social engineering tactics, advanced obfuscation methods, and meticulously crafted lures, this threat actor has demonstrated a significant capability to evade detection and compromise high-value targets.”
