I’m not a LastPass user but this tweet from Sean Wright caught my attention.
Just as I thought… LastPass considers a user enumeration issue to be an informational issue (and hence not interested). Just another reason to not use it!
— Sean Wright (@SeanWrightSec) August 9, 2022
Sean afterwards posted this:
So I’m need to own up to making an incorrect assumption 😞 I think it was the bug bounty programme and not LastPass who closed the issue. Apologies to LastPass if this was the case! https://t.co/zQzO5OuuI8
— Sean Wright (@SeanWrightSec) August 9, 2022
Regardless if it was LastPass or the bug bounty program closing the issue, I think this should be fixed.
They consider it an informational issue, but is it really that innocent?
What’s a user account enumeration risk?
Simply put, we speak of a user (account) enumeration risk when a website or application leaks whether a particular user has an account.
That’s about enough for now to understand the problem, but if you want to learn a bit more about user account enumeration, I suggest you to read this short post first.
For testing purposes I created a free LastPass account with the email address [email protected]
I deliberately entered the wrong password here and get the following message:
“Check your master password and try again.”
Let’s try to enter a non-existent email address.
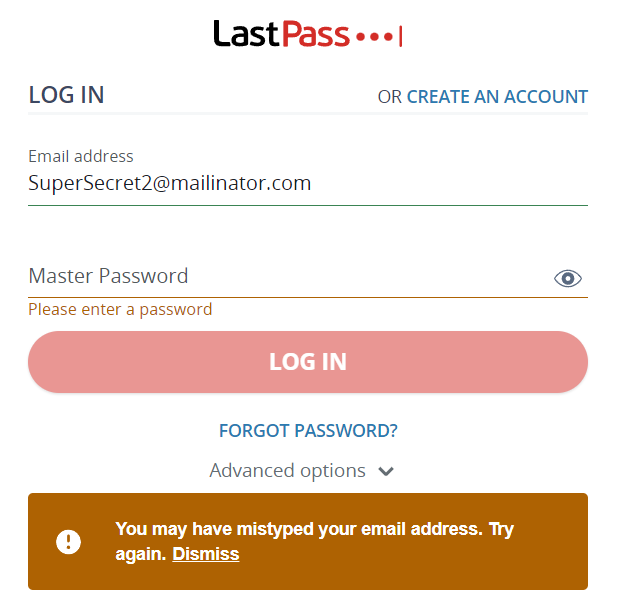
And I get a different message:
“You may have mistyped your email address. Try again.”
This implies that you can easily deduct if a particular email address has an associated account.
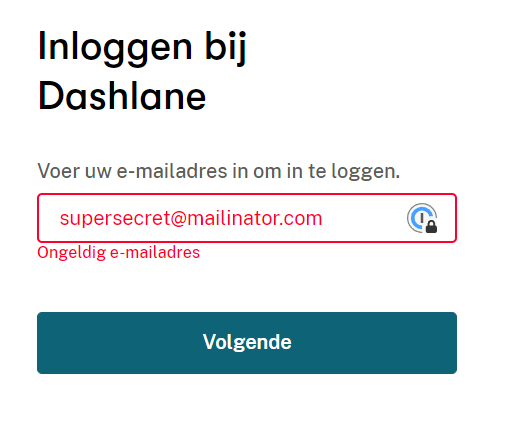
This issue is not limited to LastPass only, Dashlane for instance also shows whether an email address is “invalid” or already in use.
(Why) is this a problem?
Is it such a big deal that someone would know which password manager you use?
It depends…
It’s not a secret that I use 1Password. I have blogged before how I did my own research and came to the decision that it is a good fit for me. I feel quite comfortable to be open about this because even if an adversary knows that I have a 1Password account, it isn’t very helpful to them.
My threat model is also very different from people that have to fear nation state attackers.
I think 1Password does a real good job at security. Let’s have a look how they prevent enumeration at login. If someone would enter the email address I use, they still will not be able to provide the secret key. 1Password will show “Invalid Secret Key”, thus not leaking if an account is associated with this email address or not.
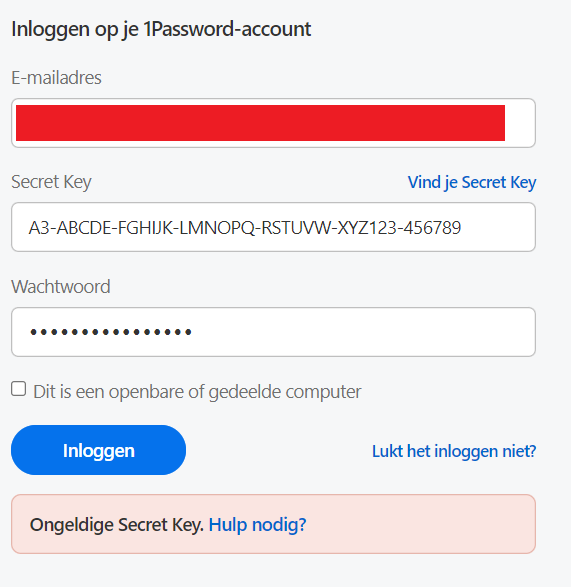
This is an elegant way of preventing enumeration and besides the secret key is an extra encryption key on top of the master password.
By default LastPass relies purely on the email address and master password to protect their users’ accounts. One of these two pieces of information can be retrieved by enumerating their login page. This means that the master password is the only defense that’s standing between someone’s account and an attacker.
Both 1Password and LastPass have the option to enable two-factor authentication but this is not mandatory.
We might hope that people choose a strong password at account creation and enable two factor authentication, but reality is often different. The fact that weak passwords like [email protected] are allowed by LastPass isn’t really promising either.
Enumeration becomes a real risk for people that have bad account security practices. One might say securing their account is the end user’s responsibility, but when the entire premise of your product is securing people’s secrets, LastPass’ implementation is simply not enough.
The secret key 1Password assigns to a user account even protects people that use bad passwords, fends off credential stuffing and other passwords attacks and strengthens the encryption of people’s secrets.
The LastPass enumeration risk is not limited to the login page. At account creation it’s also very easy to check whether an email address is already registered.
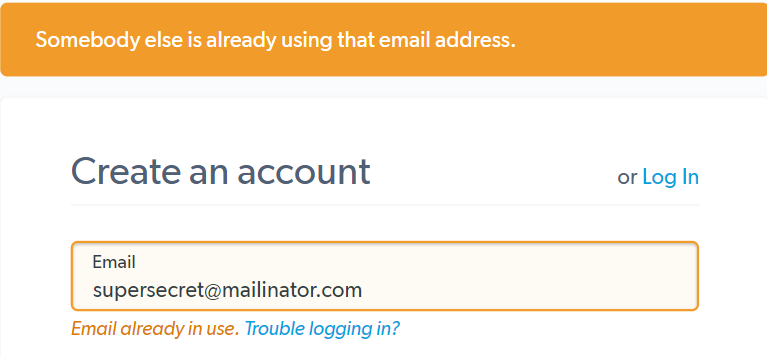
Bitwarden has the same behavior, when an account already exists for a particular email address it shows an error message.
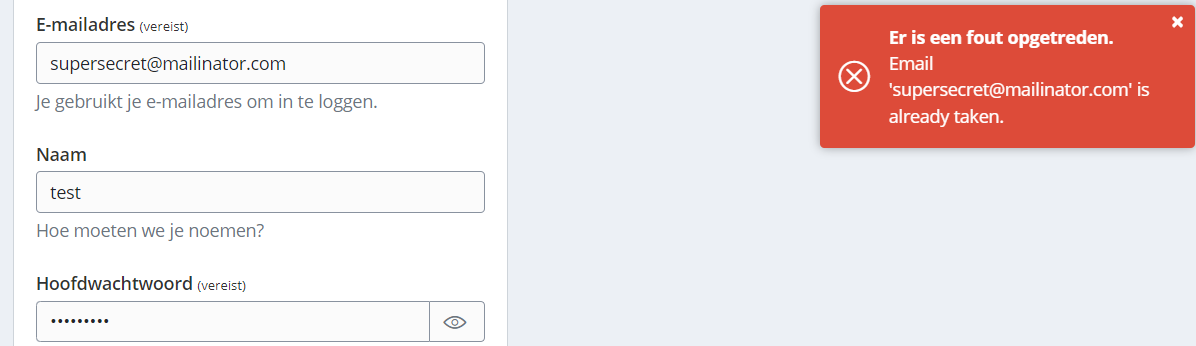
This is also quite simple to fix. 1Password does so by sending a verification code to the provided email address.
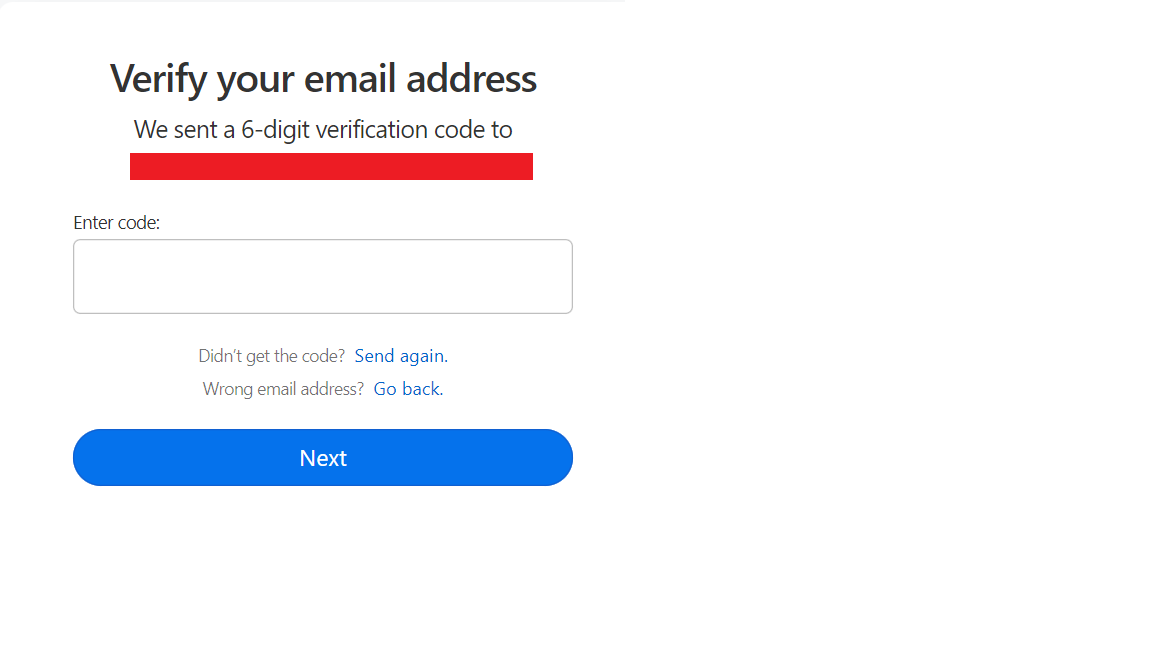
In this way they don’t leak whether the email address is already registered and only if the requester has access to the e-mail account they’ll receive the code and can either continue the registration or sign in to their account if it already exists.
Conclusion
An account enumeration risk on its own might be a low risk but when no other controls – like a secret key associated to a user account – are enforced, the risk increases.
Of course this risk can be limited by using a strong master password and 2FA, but in my opinion a password manager vendor should do better.
It’s simply not a good look for a service whose entire premise is to secure people’s secrets. Given that it’s also very easy to fix it should be a no-brainer.
I’ve currently compared LastPass’ account registration and login with 1Password because that’s the password manager I use and because I know they do a good job at account security. I’ve done some quick checks on some other password managers, like Dashlane, Keeper, Nordpass and Bitwarden, but I plan to look more into detail at different password managers and compare their account management implementations.




