Welcome to HackerOne’s second edition of “Fact or Fiction,” where we review hacking entertainment and discuss how realistic (or not!) they are. For this blog entry, we’re going to focus on season two’s ninth episode, A.K.A. eps2.7init5.fve.
Warning! Spoilers ahead!
If you aren’t caught up on season two, now’s your chance to turn around and pretend this blog never happened (at least, until you’re caught up, of course).
Rubber ducky
My very favorite little pal, rubber ducky! Sesame Street set aside, Rubber Ducky is a tool that Mobley gave Angela originally for the FBI hack. Rubber Ducky is a USB device that basically acts like a keyboard and punches in a bunch of commands that you’ve programmed it with. You can learn more about it here. In this episode, Angela grabs it out of her bag:

Then she uses her mastery of social engineering to trick someone who looks like her new boss’s admin assistant to leave the room so she can get access to his computer while everyone’s out to lunch:

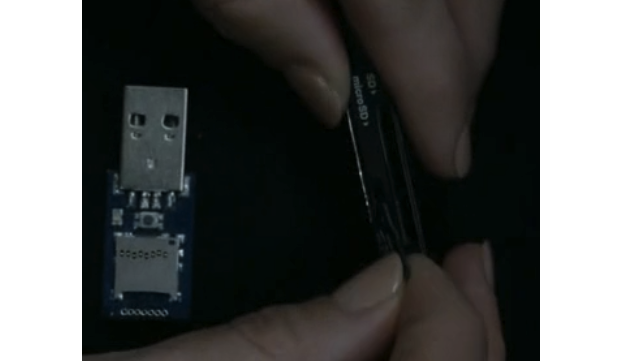
Angela pops the rubber ducky into her boss’s machine

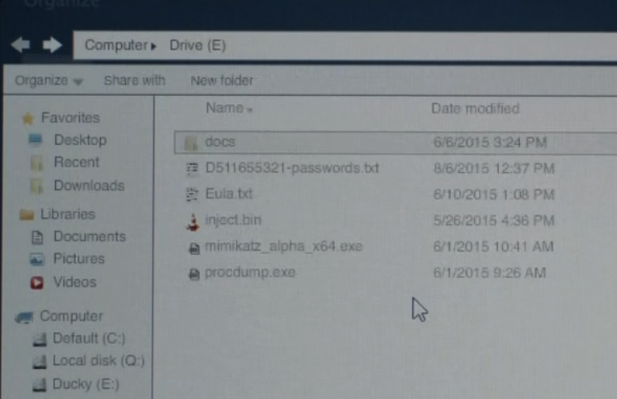
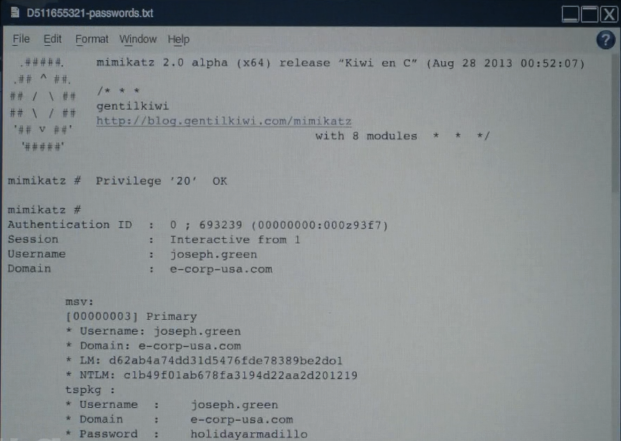
The Rubber Ducky gets to work, leveraging “mimikatz” to steal her boss’s password and copy it to the USB stick. Angela head’s back to her desk, grabs the micro SD card from the rubber ducky, pops it into a micro SD reader, and plugs that into her own machine.

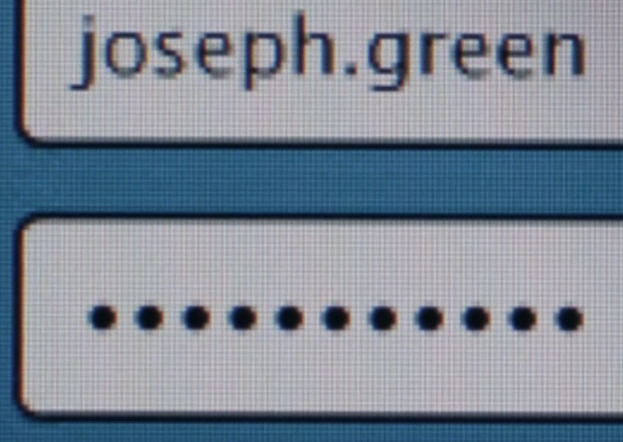
Now we see Angela browsing through the contents of the SD card, and we can see that there’s a text file that contains her boss’s password (holidayarmadillo).
From here, she logs out, then logs in as her boss to access the files.
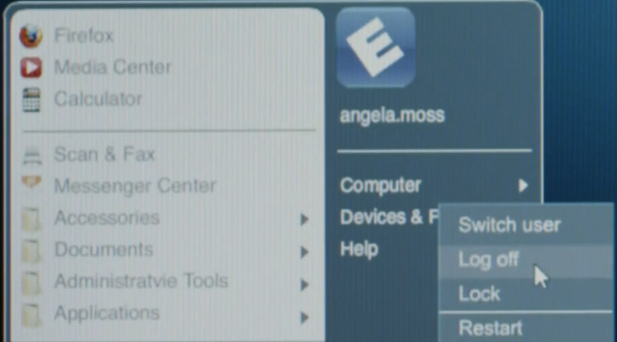
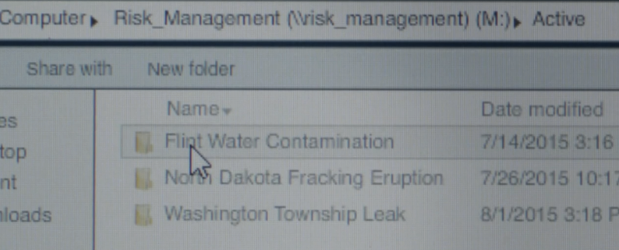
Hopefully this won’t leave much of a trace in terms of suspicious activity, it will just look like her boss was accessing the files from the Washington Township case. That said, she did login as her boss from her own computer (not her boss’s), and depending on logging settings on her boss’s machine, they might be able to see a USB device was plugged in to his box while he was at lunch… so we’ll see what happens!
Pwnie Express Pwn Phone
This is a real device that is used by penetration testers, you can learn more about it here: https://www.pwnieexpress.com/mr-robot-pwn-phone. It comes loaded with a lot of the same tools you’d see on Kali Linux (the operating system we see fsociety use throughout the show on their laptops). Now, the custom script Elliot uses called CrackSim is NOT a real life thing. This is something that appears to have been made up for the show. From what I can tell, Elliot sends a text message to Shun (Cisco’s Dark Army contact). This text message is actually malicious and somehow installs Elliot’s malware onto the SIM card of Shun’s phone. This malware allows Elliot to hijack the microphone on the phone and lets him and Darlene listen in to his conversations, even when he’s not actually on a phone call.

Even though CrackSIM itself is not a real thing, attacks like this are definitely plausible. Apple recently released an emergency update to patch three vulnerabilities due to recently discovered malware called Pegasus. A suspicious text message was sent to Ahmed Mansoor, a human rights activist, who realized something was up and contacted his security friends at Citizen Lab and Lookout. They did a technical analysis and found out NSO Group had created malware that lets you hijack someone’s iPhone just by the victim clicking on a link. The Pegasus malware that gets installed gives the attacker access to everything. You can look through email, Facebook messages, listen in on the microphone, and even peek through the camera! You can learn about it in much more detail here.
Wrapping it up
There are so many easter eggs and hidden messages within Mr. Robot! Have you found any from episode 9 we missed? Let us know!
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.




![[tl;dr sec] #208 – Cybersecurity GPT Agents, Supply Chain Security, Kubernetes Pentest Image [tl;dr sec] #208 - Cybersecurity GPT Agents, Supply Chain Security, Kubernetes Pentest Image](https://image.cybernoz.com/wp-content/uploads/2023/11/tldr-sec-208-Cybersecurity-GPT-Agents-Supply-Chain-Security-360x270.png)