A new longitudinal study of Magecart-style eSkimming attacks overturns the assumption that discovery equals recovery.
Instead of being a one-time incident that ends with script removal, eSkimming is emerging as a long-lived, shape‑shifting threat that lingers on previously compromised sites and often returns in new forms.
Over the course of a year, researchers tracked 550 previously compromised e-commerce sites across 68 countries.
The findings are clear: eSkimming persistence is not the exception; it is the norm. One year after initial discovery, 18% of these sites remained actively infected, meaning nearly one in six organizations never achieved true recovery.
More troubling, 57% of still‑infected sites were not running the original skimmer, but a new or evolved attack path, indicating active adaptation and re‑exploitation rather than simple cleanup failures.
Report challenges that assumption. Based on a year-long longitudinal study of 550 previously compromised e-commerce websites
In parallel, 16% of sites originally identified as victims have since gone offline or become unreachable, an alarming pattern for any business that leaves client-side attacks unresolved.
The root cause is structural. eSkimming operates entirely within the user’s browser, while most defenses – WAFs, CSPs, server-side scanners, and code reviews – focus on networks, servers, or static assets.
How eSkimming Tactics Are Evolving
Typical remediation removes the visible skimmer but leaves the underlying exposure untouched: a lack of real-time visibility and control over what first- and third‑party scripts do at runtime.
As long as the browser remains an unmonitored execution environment, attackers can quietly persist, pivot, and re-enter through new vectors that traditional controls implicitly trust.
The Source Defense study distilled its active sample from an initial dataset of roughly 3,600 known Magecart victims.
Of these, 550 reachable, operational websites were analyzed after at least a year had passed since the original compromise, excluding sites that had already gone offline.
Each site was classified as clean (no active skimmer), infected (active skimming code), or offline. By focusing only on operational businesses with ample remediation time, the report provides a realistic view of whether organizations achieve durable recovery, not just short‑term cleanup.
Geographically, the problem is borderless. The 68‑country dataset spans almost every continent, with the United States accounting for nearly one‑third of active sites and the United Kingdom roughly 9%.
On average, 18% of sites showed persistent eSkimming, but there were notable outliers: Spain recorded the highest persistence rate at 23%, while Germany stood out with only 4% infected, suggesting comparatively stronger remediation discipline or client‑side security controls.
Despite these differences, the pattern is consistent: wherever browser‑side blind spots exist, Magecart operators succeed.
Complexity of eSkimming Attacks
Persistence in this dataset is less about sloppy incident response and more about attacker innovation.
Among the 98 infected sites, 43% still showed the original campaign, while 57% exhibited re‑infection or evolution, such as new code paths, altered delivery, or fresh script locations.
Attackers watch and react to defender behavior; when organizations block one malicious script but leave the core exposure unchanged, they effectively incentivize adversaries to return with more resilient techniques.
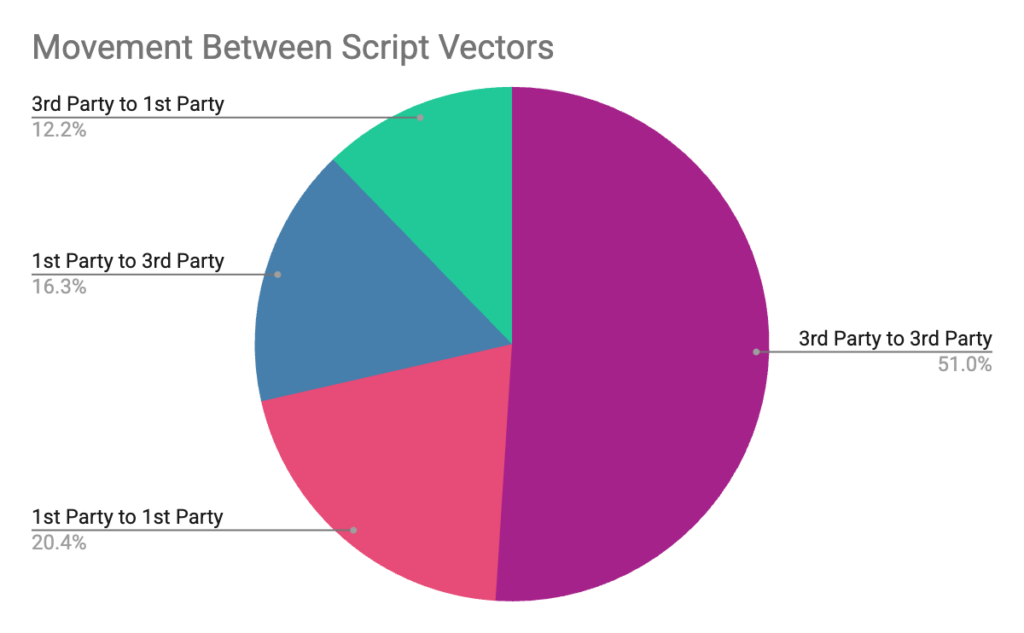
One of the clearest signs of this adaptation is the movement between first‑ and third‑party code. Some campaigns begin in third‑party scripts and later migrate into first‑party JavaScript; others reverse that flow or simply rotate infrastructure while preserving behavior.
In the study, 12% of campaigns shifted from third‑party to first‑party execution over time, embedding deeper into core site logic and the trusted application surface.
Each wave of partial remediation closes one door but nudges attackers toward entry points that are even harder to detect and remove.
The conclusion is unavoidable: point‑in‑time cleanup and server‑centric tools are no longer sufficient for a threat that executes inside the browser.
Effective defense now requires continuous client-side monitoring that can observe all executing scripts (including trusted ones), detect risky behaviors in real time, and enforce controls during execution before payment data or other sensitive information is skimmed or exfiltrated.
In our data, 12% of campaigns shifted from third-party to first-party execution over time, embedding deeper into core site logic.
Source Defense positions its technology as an answer to this gap. By operating directly in the browser, it provides runtime visibility into script behavior, flags unauthorized access to sensitive fields and fake payment forms, and applies behavior‑based controls that can block data exfiltration and make post‑cleanup pivots significantly harder.
This shifts organizations from episodic incident response to continuous control over the client‑side environment.
Ultimately, the study reframes eSkimming from a technical nuisance to a strategic business risk. The fact that a notable share of previously attacked sites later disappear from the web, even if not conclusively attributable to eSkimming, is a stark warning.
In an era where the browser is the primary transaction surface, visibility into client-side behavior is no longer optional – it is the foundation for turning “incident resolved” into recovery that truly lasts.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




