Europol has confirmed that a Telegram channel impersonating the agency and offering a $50,000 reward for information on two Qilin ransomware administrators is fake. The impostor later admitted it was created to troll researchers and journalists.
“We were also surprised to see this story gaining traction,” Europol told BleepingComputer on Monday. “The announcement didn’t come from us.”
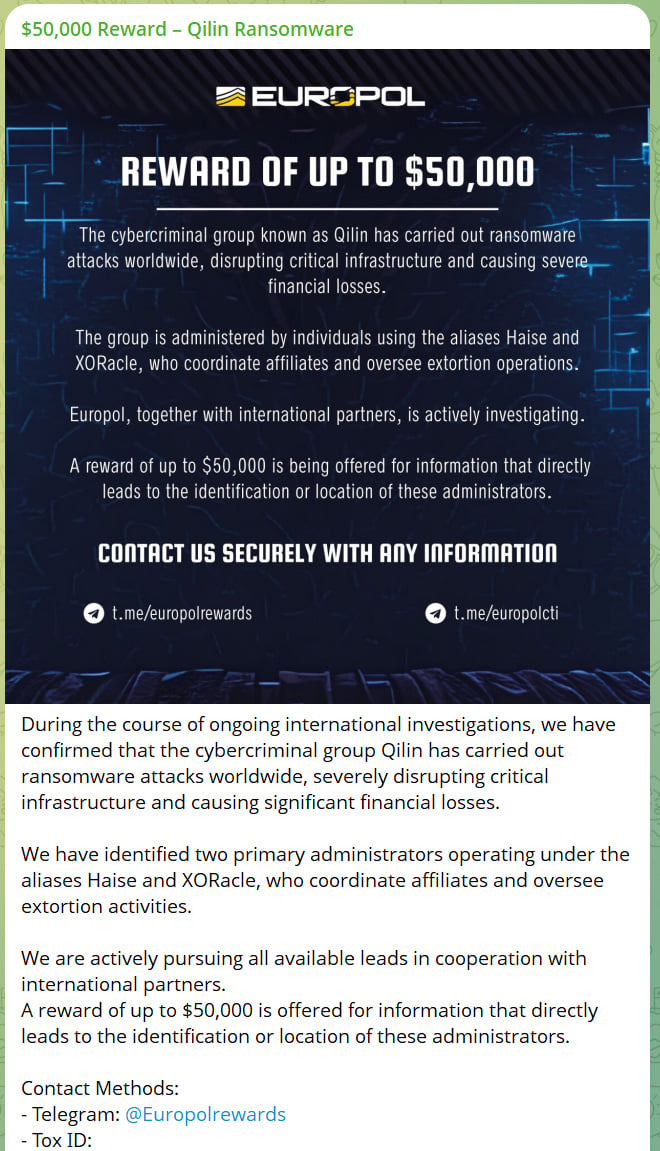
The statement comes after a new Telegram channel called @europolcti was created on August 16th, claiming to offer a $50,000 reward for information on two Qilin ransomware admins known as “Haise” and “XORacle”.
“During the course of ongoing international investigations, we have confirmed that the cybercriminal group Qilin has carried out ransomware attacks worldwide, severely disrupting critical infrastructure and causing significant financial losses,” reads the imposter’s Telegram post.
“We have identified two primary administrators operating under the aliases Haise and XORacle, who coordinate affiliates and oversee extortion activities.”
“We are actively pursuing all available leads in cooperation with international partners.”
“A reward of up to $50,000 is offered for information that directly leads to the identification or location of these administrators.”
Source: BleepingComputer
Haise is believed to be one of the operators of the Qilian ransomware gang, previously recruiting affiliates on the RAMP cybercrime forum.
The Qilin ransomware operation was initially launched as “Agenda” in August 2022. However, by September that year, it had rebranded under the name Qilin, which it continues to use to this day.
The ransomware operation is one of the most active, currently targeting companies worldwide.
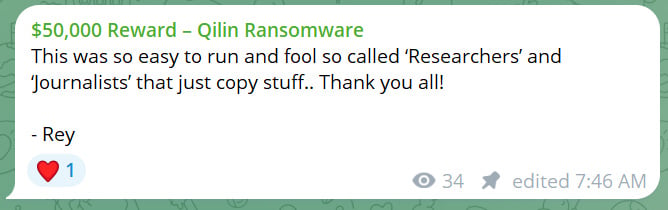
However, after Europol confirmed it was fake, a new post appeared on the imposter channel claiming it was created to troll researchers and journalists, some of whom wrote articles about the claims.
“This was so easy to run and fool so called ‘Researchers’ and ‘Journalists’ that just copy stuff.. Thank you all!,” reads the new post.
Source: BleepingComputer
The post was signed by Rey, a hacker previously linked to breaches at Telefonica and Orange Group.
However, the actually trolling started in August 15th posts on a Telegram channel impersonating threat actors from “Scattered Spider”, “ShinyHunters”, and “Lapsus,” where someone had begun calling out Haise and the ransomware operation.
This is not the first time threat actors attempted to mislead the media about cybercrime.
In 2021, a RAMP admin known as ‘Orange’ or ‘boriselcin’ and who ran the “Groove” ransomware site, called on threat actors to attack the USA. This threat actor was later sanctioned by the US for his involvement in three ransomware operations that targeted victims across the United States.
After the media covered this post, including BleepingComputer, the threat actor claimed it was fake and was created to troll and manipulate the media and security researchers.
However, security researchers from McAfee and Intel 471 believe that it was likely the threat actor trying to cover up for a failed ransomware-as-a-service.
In 2023, BleepingComputer receieved a “tip” about an alleged arrest of two Canadian teens over a crypto-theft attack.
While BleepingComputer learned that the news was fake and did not cover the story, we were told it was done to manipulate the media and “troll” the people accused of the theft.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
