An international law enforcement operation dubbed “Operation Eastwood” has targeted the infrastructure and members of the pro-Russian hacktivist group NoName057(16), responsible for distributed denial-of-service (DDoS) attacks across Europe, Israel, and Ukraine.
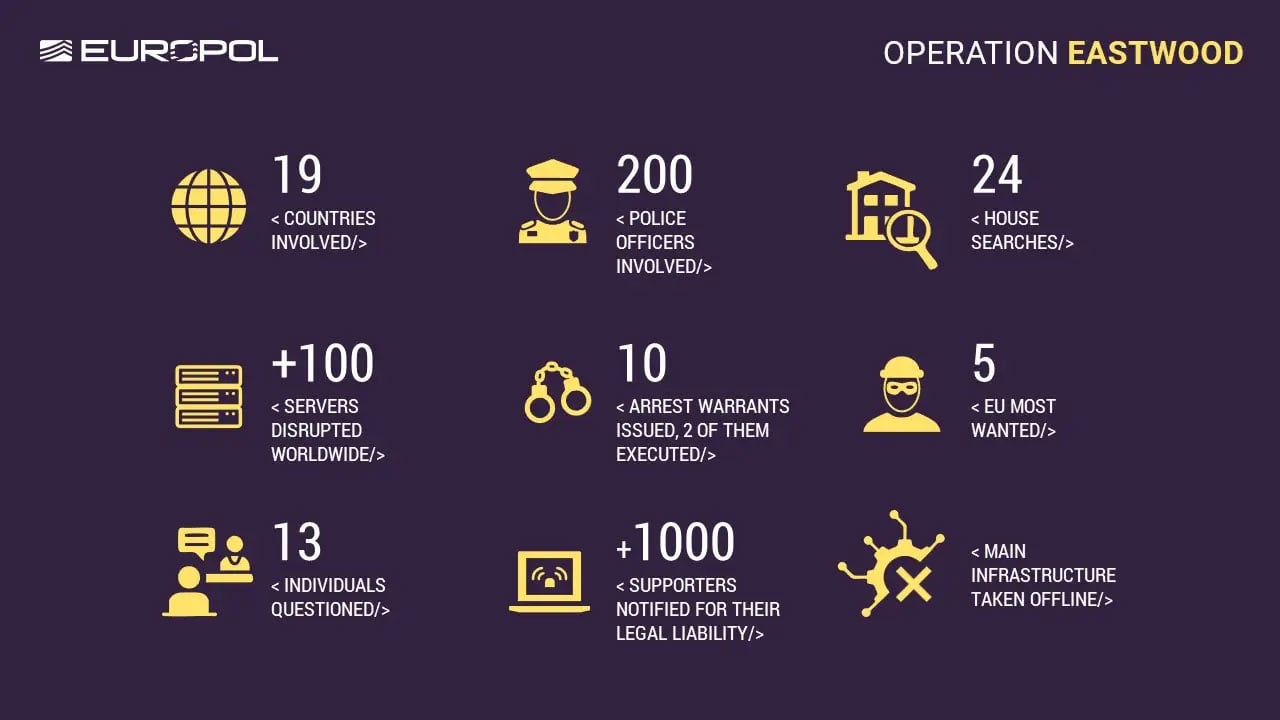
Operation Eastwood was led by Europol and Eurojust with support from 12 countries. It took place on July 15, 2025, and targeted the systems and individuals behind the group’s activities.
NoName057(16) is a pro-Russian hacking group that launched in March 2022 after the war in Ukraine began. To conduct attacks, the group uses Telegram channels and the “DDoSia” project, software that runs on volunteers’ computers to crowdsource DDoS attacks on targets selected by the threat actors.
Since then, NoName057(16) and its supporters have carried out DDoS attacks against companies and critical infrastructure in European countries that support Ukraine. These targets include NATO sites, government agencies, transportation services, banks, defense firms, media outlets, and energy suppliers.
According to Europol, the attacks disrupted critical services in Germany, Poland, Lithuania, Latvia, Estonia, Sweden, the Netherlands, and other countries.
Source: BleepingComputer
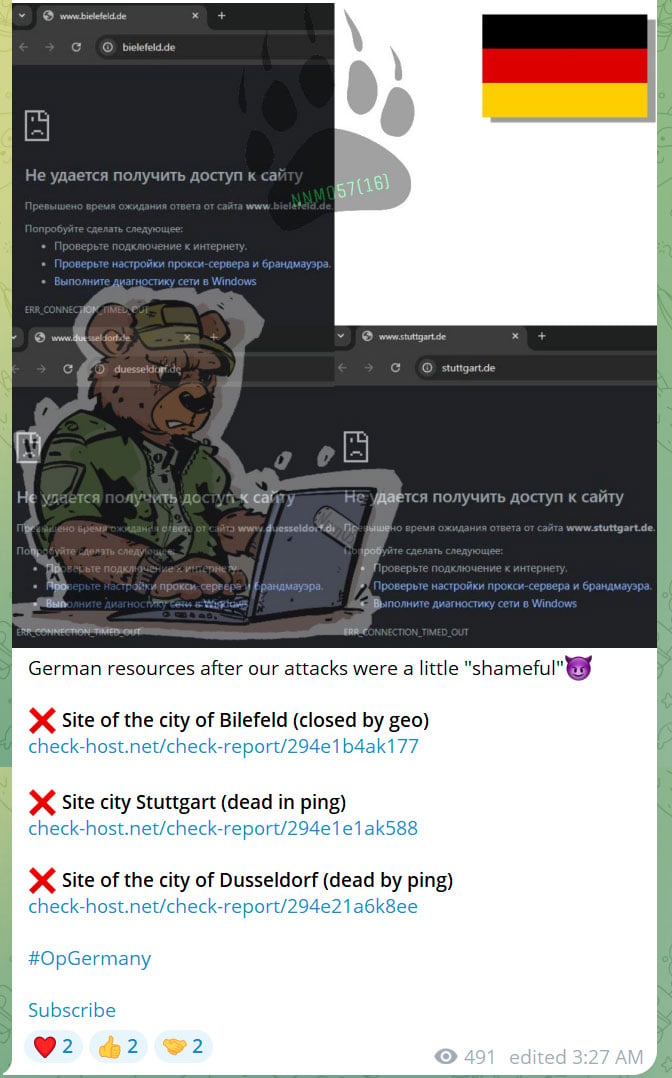
“The hacktivist group has executed 14 attacks in Germany, some of them lasting multiple days and affecting around 230 organisations including arms factories, power suppliers and government organisations,” reads a statement from Eurojust.
“Attacks were also executed across Europe during the European elections. In Sweden, authorities and bank websites were targeted, while in Switzerland multiple attacks were carried out during a video message given by the Ukrainian President to the Joint Parliament in June 2023, and during the Peace Summit for Ukraine in June 2024.”
“Most recently, the Netherlands was targeted during the NATO Summit at the end of June.”
On July 15, law enforcement agencies conducted searches in Germany, Latvia, Spain, Italy, Czechia, Poland, and France, with more than 100 servers hosting the group’s infrastructure disrupted or taken offline.
Two arrests have been made as part of this operation (1 preliminary arrest in France and 1 in Spain), and seven European arrest warrants were issued, including six by Germany and one by Spain. The authorities also sent Telegram messages to 1,100 participants and 17 administrators, warning them that they were facing criminal liability for their actions.
Six of the warrants issued by Germany are for individuals believed to be residing in Russia, with two of them suspected of being the primary operators of the group.
Source: Europol
The operation involved law enforcement from Czechia, Estonia, Finland, France, Germany, Latvia, Lithuania, the Netherlands, Poland, Spain, Sweden, Switzerland, and the United States.
Authorities claim that Operation Eastwood is a significant blow to NoName057(16). However, with the core members located in Russia, this action is likely to have only a short-lived effect, as the threat actors will likely rebuild their infrastructure.
As of today, the threat actors continue to announce new attacks and breaches of German companies.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.
