Malware peddlers are using NodeLoader, a loader written in Node.js, to foil security solutions and deliver infostealers and cryptominers to gamers.
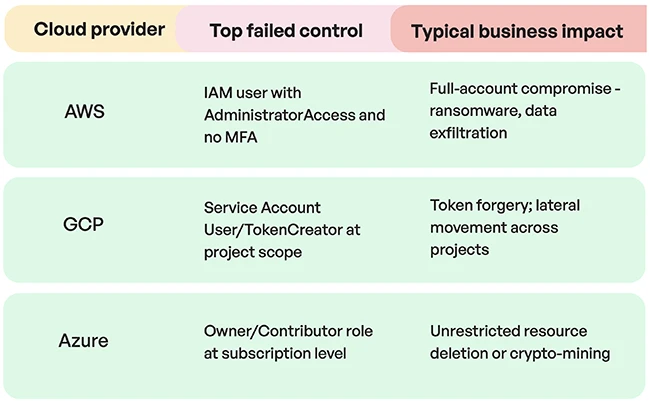
The malicious links in YouTube comments (Source: Zscaler ThreatLabz)
Attackers leveraging the Node.js loader
In this latest malware delivery campaign, the attackers are using YouTube and Discord to publish links that professedly lead to game hacks hosted on (spoofed) gaming websites.
The fake game hack / cheat comes in the form of a malicious ZIP archive that, when unzipped, shows a malicious executable compiled in Node.js.
When this file is run by the user, it first checks whether any of a number of processes (i.e., applications) are running on the user’s machine: Chrome, Opera, Frefox, Steam, Spotify, Discord, Telegram, Microsoft Gaming Install Services, Lightshot (screenshot tool), and Epic Games Launcher.
If it finds at least one, it downloads a PowerShell script, which in turn downloads and saves two additional executables and executes them: the XMRig cryptocurrency miner and the Phemedrone Stealer.
The former enganges in detection evasion, attempts to stop the Windows Event Log Service and uninstall Windows updates related to the Windows Malicious Software Removal Tool, and creates a service to establish persistence. The latter is able to steals login credentials, cookies, etc. from Google and Microsoft browsers and uploads it to Telegram.
“In addition to downloading Phemedrone, the threat actors utilized a separate malicious URL to deliver a loader for Lumma Stealer,” Zscaler researchers found.
Why are attackers using Node.js?
Threat actors have been known to write malware loaders in Node.js.
Node.js is a cross-platform JavaScript runtime environment built on Chrome’s V8 JavaScript engine.
While it’s often used for building web-based services, it can also be used to create command line tools and to build client-side apps for common desktop platforms running popular operating systems (Windows, macOS, Linux, Unix, etc.)
“NodeLoader’s code is written in Node.js using JavaScript. The Node.js code, along with all necessary dependencies, is compiled into a binary executable using the [Node Package Manager] pkg module. This step packages everything needed to run the Node.js code, including the V8 JavaScript engine library,” the researchers explained.
“When compiled using the pkg NPM module, a single line of code results in a large Windows binary exceeding 35 MB. This large file size complicates detection for some security products. In addition, there are far fewer signatures for malicious JavaScript-based code. As a result, many of the NodeLoader binaries associated with this campaign currently have zero antivirus and EDR detections.”
As of today, the NodeLoader executables detected by Zscaler still have abysmal AV detection results. The final payloads – the cryptominer and the infostealers – are detected by many solutions, though.