The dark web leak site of the Everest ransomware gang has apparently been hacked over the weekend by an unknown attacker and is now offline.
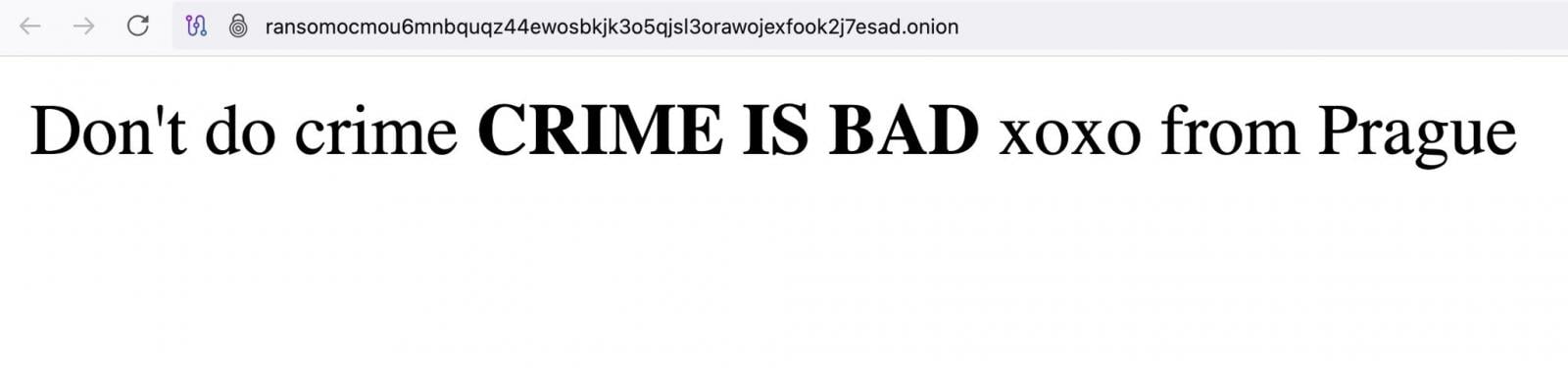
The unknown attacker replaced the website’s contents with the following sarcastic message: “Don’t do crime CRIME IS BAD xoxo from Prague.”
The Everest operation has since taken down its leak site, which no longer loads and now displays an “Onion site not found” error.
While it’s unknown how the attacker gained access to Everest’s website or if it was even hacked, some security experts, like Flare Senior Threat Intelligence Researcher Tammy Harper, point to a potential WordPress vulnerability that could’ve been exploited to deface the ransomware operation’s leak site.
“It is worth mentioning that Everest was using a WordPress template for their blog. I would not be surprised if that was how this happened,” Harper said.
Since it surfaced in 2020, the Everest ransomware operation has switched tactics from data theft-only corporate extortion to including ransomware in its attacks to encrypt victims’ compromised systems.
Everest operators are also known for acting as initial access brokers for other cybercrime gangs and threat actors, selling access to breached corporate networks.
Over the last 5 years, Everest has added over 230 victims to its dark web leak site, which is used as part of double-extortion attacks where the ransomware gang tries to force their victims’ hand into paying ransoms under the threat of releasing files containing sensitive information.
One of its most recent victims is STIIIZY, a popular California-based cannabis brand that Everest claimed in November 2024. In January, STIIIZY disclosed that unknown attackers hacked its point-of-sale (POS) vendor to steal customer information, including purchase information and government IDs.
In August 2024, the U.S. Department of Health and Human Services also warned that the Everest ransomware gang was increasingly targeting healthcare organizations across the United States.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
