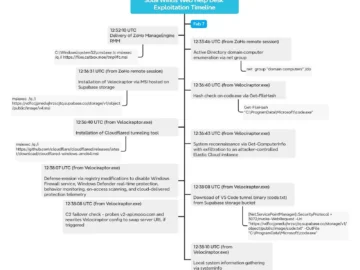
Evilginx is an open-source man-in-the-middle attack framework designed to phish login credentials and session cookies, enabling attackers to bypass 2FA safeguards.
“Back in 2017, I was experimenting with extracting cookies from one browser and importing them into another. I realized this technique could effectively take over accounts, bypassing the need for credentials or even MFA authorization. This discovery led me to consider the possibility of executing such an attack remotely by proxying HTTP traffic between the target user and the website. I built a proof-of-concept using Nginx combined with LUA scripting to test this idea. This project eventually evolved into Evilginx v1.0,” Kuba Gretzky, the creator of Evilginx, told Help Net Security.
“When Evilginx v1.0 was released, the concept of using reverse proxies wasn’t new. What set it apart, however, was that it was the first publicly available tool to expose the vulnerabilities of MFA, even on high-profile platforms like Google. Its uniqueness lay in the attention it garnered—it made a lot of noise. In truth, there was nothing cutting-edge about the tool itself; its impact came from how it highlighted a critical security gap,” Gretzky explained.
The author of Evilginx emphasizes that the project demonstrates the techniques skilled attackers may employ. The author asserts that it is the responsibility of defenders to consider such threats and develop strategies to protect users from these types of phishing attacks. Evilginx is intended solely for legitimate penetration testing assignments conducted with explicit written permission from the targeted parties.
Evilginx is available for free download on GitHub.
![]()
Must read: