KeePass is a widely used open-source password manager that enables you to manage your passwords by using a database that is maintained locally, as opposed to a database that is hosted in the cloud, like LastPass or Bitwarden. KeePass is quite popular. ! Researchers in the field of information security have uncovered a major flaw in the widely used password manager KeePass, which puts users of the software in grave danger. There is a possibility that KeePass version 2.5x is vulnerable to the security hole known as CVE-2023-24055, which might enable attackers to read passwords that have been saved in cleartext.
Given that a proof-of-concept (PoC) exploit is already available and that KeePass is one of the most widely used password managers in the world, the current security flaw is a tempting target for malicious actors. for the purpose of proactively detecting harmful behavior linked with exploitation of CVE-2023-24055.
CVE-2023-24055 The proof-of-concept exploit code might be altered by adversaries in order to evade detection and go on with the attack while remaining undetected. It allows threat actors with write access to a target’s system to edit the KeePass XML configuration file and insert a malicious trigger that would export the database, including all users and passwords in cleartext. This can only be done if the threat actor has access to the target’s system.
The export rule will be activated and the contents of the database will be stored to a file that the attackers may subsequently exfiltrate to a machine under their control once the target starts KeePass and inputs the master password to open and decrypt the database the following time.
Any malicious changes to the KeePass configuration file may be made by an adversary who has write access to the file (for example, he could inject malicious triggers). However, KeePass does not really have a problem with this particular security flaw.
The company said the following
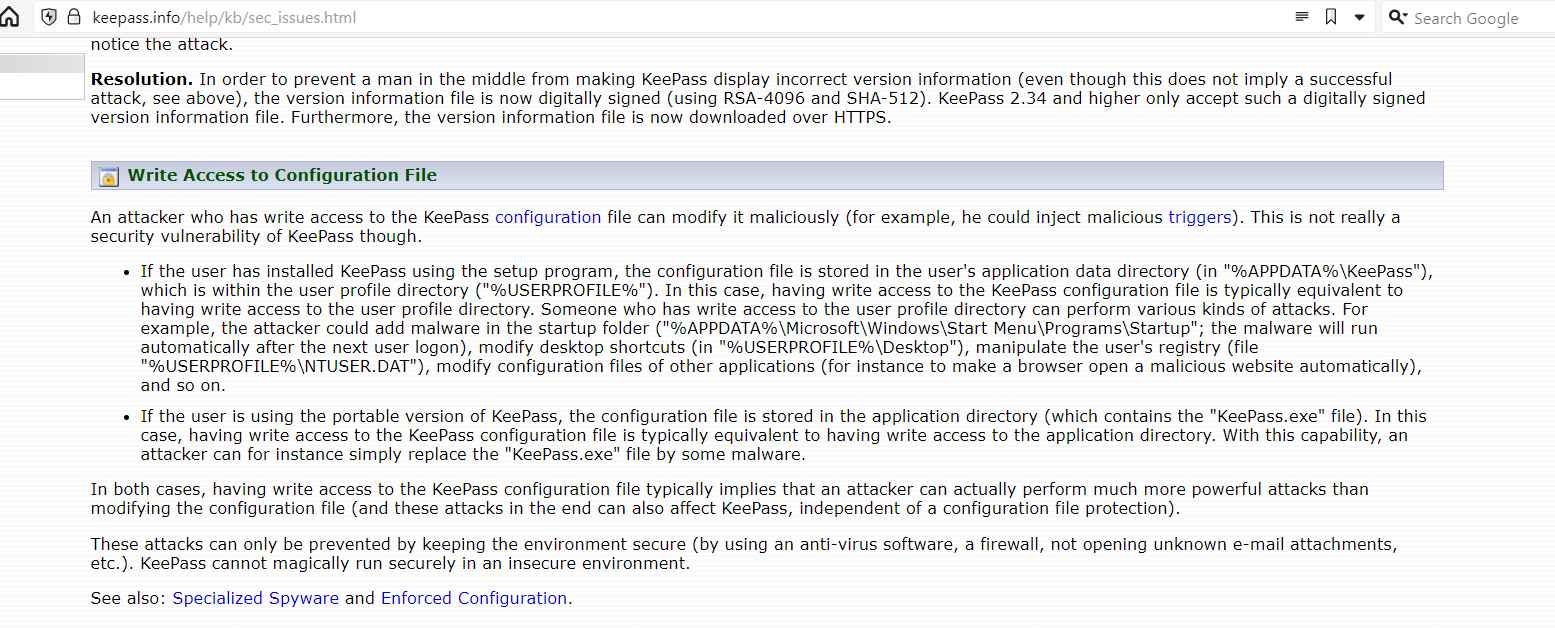
If the user installs KeePass by using the setup program, the configuration file will be located in the user’s application data directory (in “%APPDATA%KeePass”), which is contained inside the user profile directory (“%USERPROFILE%”) of the operating system. When it comes to KeePass, having write access to the configuration file is generally considered to be the same thing as having write access to the user profile directory. Any sort of attack may be carried out by a person as long as they have the ability to write to the user profile directory. For instance, the adversary could plant malware in the startup folder (“%APPDATA%MicrosoftWindowsStart MenuProgramsStartup”; the malware will run automatically after the next user logon), modify desktop shortcuts (in “%USERPROFILE%Desktop”), manipulate the user’s registry (file “%USERPROFILE%NTUSER.DAT”), modify configuration files of other applications.
In the event that the user is working with the portable version of KeePass, the configuration file is kept in the directory that the program is installed in (which contains the “KeePass.exe” file). When it comes to KeePass, having write access to the configuration file is often considered to be the same thing as having write access to the application directory. Because of this feature, a malicious actor may, for example, easily replace the “KeePass.exe” file with another piece of malicious software.
In either scenario, having write access to the KeePass configuration file often indicates that an attacker is able to carry out operations that are far more potent than just altering the configuration file (and these attacks in the end can also affect KeePass, independent of a configuration file protection).
Keeping the environment secure is the only way to stop assaults like this from happening (by using an anti-virus software, a firewall, not opening unknown e-mail attachments, etc.). It is impossible for KeePass to magically function safely in an environment that is not secure.
However, even if the KeePass developers do not provide users with a version of the app that addresses the export to cleartext via triggers issue, you can still protect your database by logging in as a system administrator and creating an enforced configuration file. This is something you can do even if they do not provide users with a version of the app that addresses the issue.
This sort of configuration file takes priority over settings stated in global and local configuration files, including new triggers provided by malicious actors, hence reducing the risk associated with the CVE-2023-24055 vulnerability.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
