Horizon3 security researchers have released proof-of-concept (PoC) exploit code for a remote code execution (RCE) bug in the MOVEit Transfer managed file transfer (MFT) solution abused by the Clop ransomware gang in data theft attacks.
This critical flaw (tracked as CVE-2023-34362) is an SQL injection vulnerability that lets unauthenticated attackers gain access to unpatched MOVEit servers and execute arbitrary code remotely.
On May 31, days after the Clop ransomware gang began exploiting it on a large scale as a zero-day, Progress released security updates to patch the bug and advised all customers to immediately apply them to block exploitation attempts.
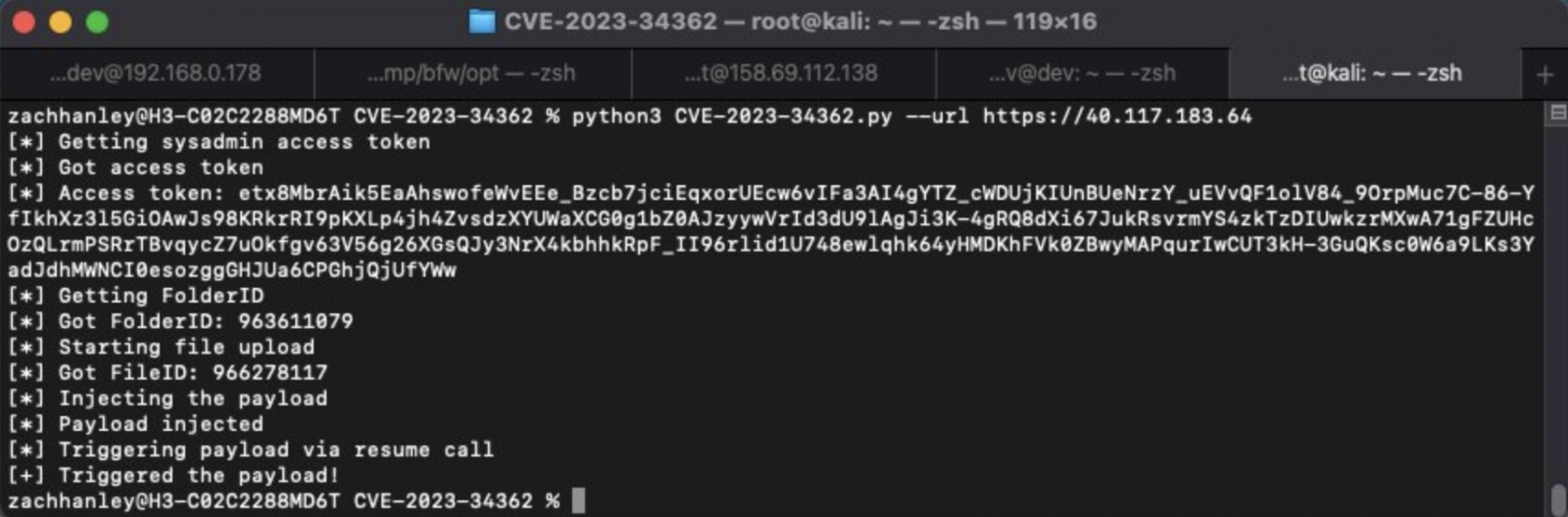
Horizon3 published a proof-of-concept (PoC) exploit and technical analysis of the vulnerability on Friday, as well as a list of indicators of compromise (IOCs) that network defenders could use to detect exploitation on vulnerable servers.
“This POC abuses an SQL injection to obtain a sysadmin API access token and then use that access to abuse a deserialization call to obtain remote code execution,” the Horizon3 researchers explain.
“This POC needs to reach out to an Identity Provider endpoint which hosts proper RS256 certificates used to forge arbitrary user tokens – by default this POC uses our IDP endpoint hosted in AWS.”
With the release of this RCE PoC exploit, more threat actors will likely move quickly to deploy it in attacks or create their own custom versions to target any unpatched servers left exposed to Internet access.
However, given the widespread media coverage of the attacks exploiting the vulnerability, it is expected that the number of unsecured MOVEit Transfer servers on the internet has sharply decreased since Clop began exploiting the bug.
Zero-day in Clop’s hands since 2021
The Clop ransomware gang has claimed responsibility for the data-theft attacks exploiting the CVE-2023-34362 MOVEit Transfer zero-day in a message sent to Bleepingomputer, attacks that allegedly impacted “hundreds of companies.”
Clop was also linked to the attacks by Microsoft, who attributed this data theft campaign to the Lace Tempest hacking group, which overlaps with FIN11 and TA505 activity.
According to a Kroll report, evidence suggests that Clop has been actively seeking opportunities to exploit the patched MOVEit zero-day vulnerability since 2021. They’ve also been searching for methods to extract data from compromised MOVEit servers since at least April 2022.
The list of organizations that have disclosed data breaches following these attacks includes, among others, the EY British multinational, the Irish Health Service Executive (HSE) public healthcare system, UK-based provider of payroll and HR solutions Zellis and some of its customers (i.e., UK’s flag carrier British Airways, Irish flag carrier Aer Lingus, and the Minnesota Department of Education).
Known for its history of orchestrating data theft campaigns, this cybercrime group has targeted vulnerabilities in multiple managed file transfer platforms during the last several years.
Notable instances include the zero-day breach of Accellion FTA servers in December 2020, the 2021 SolarWinds Serv-U Managed File Transfer attacks, and the exploitation of a GoAnywhere MFT zero-day in widespread attacks in January 2023.
On Friday, Progress patched and warned customers of newly found critical SQL injection vulnerabilities in MOVEit Transfer enabling unauthenticated attackers to steal information from customers’ databases.





