Splunk has found a vulnerability that enables unauthenticated log injection, which opens the door for hostile actors to execute dangerous code on the system. This flaw was identified by Splunk.Splunk SOAR, which stands for Security Orchestration, Automation, and Response, is a program that can be used to automate repetitive operations and react quickly to security issues. This ultimately results in improved levels of productivity. Playbooks may be used to automate answers, and the whole process can be managed via a single interface.There is a security flaw in the Splunk SOAR, which also calls for a terminal program that is able to translate ANSI escape codes. Additionally, in order to exploit this vulnerability, the terminal in question has to have the necessary permissions.
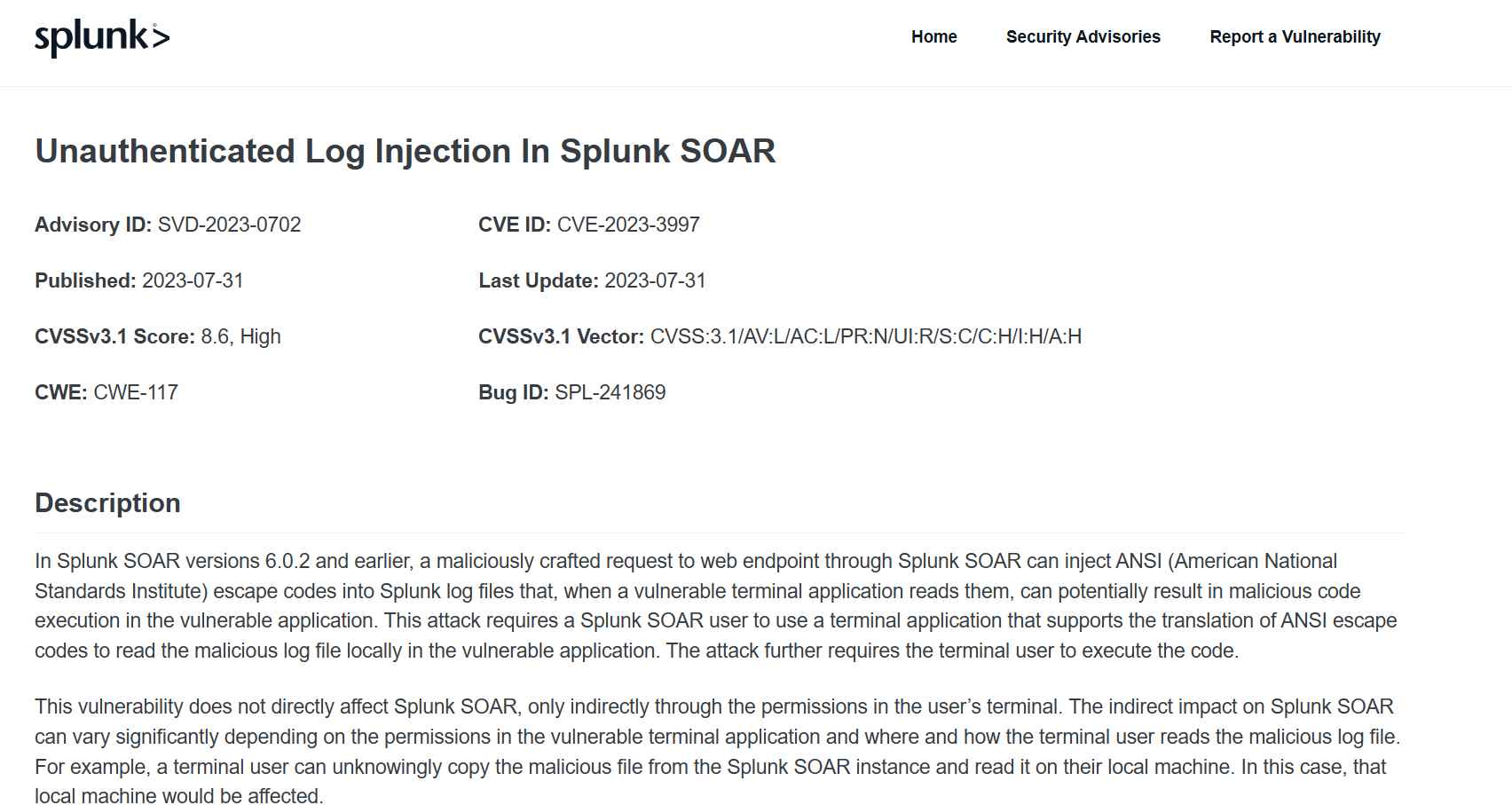
Unauthenticated Log Injection in Splunk SOAR, which is identified by the CVE ID 2023-3997
This vulnerability may be exploited by a threat actor by having them make a malicious HTTP request to an endpoint located inside the SOAR. When a terminal user makes an attempt to access the tainted logs, it causes a piece of malicious code to be executed inside the system. This vulnerability has been assigned a CVSS score of 8.6, which is considered to be “High.”
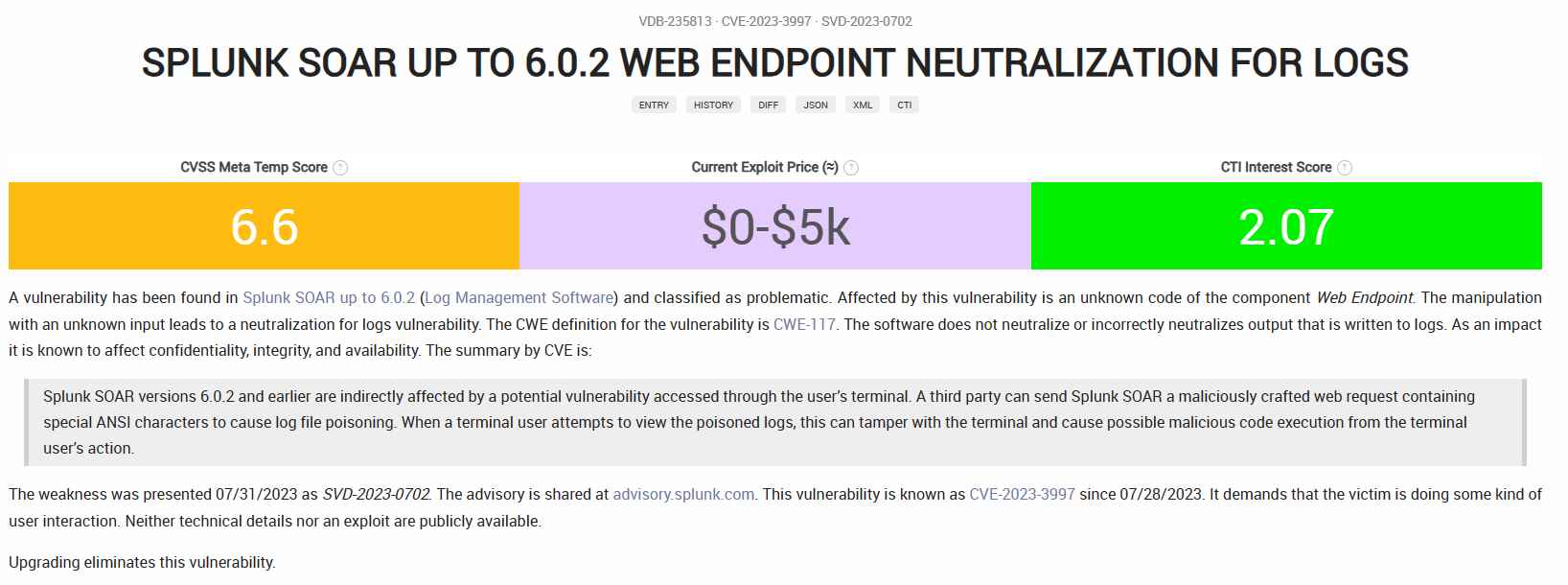
However, the severity of this vulnerability is determined on the rights granted to the terminal users that try to access the log file. If the malicious log file is copied and viewed on a local system, then that machine, rather than the instance, will be impacted by the vulnerability.
Splunk has addressed this issue by publishing a security warning on their website. The advice contains a variety of details, including the attack vector, the complexity, the privileges, the scope, and the user engagement.
Users of Splunk SOAR are encouraged to update to the most recent versions in order to protect themselves from malicious actors who may try to take advantage of this vulnerability.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
