In a major update aimed at revolutionizing the way cybersecurity professionals tackle threats, ANY.RUN has unveiled its redesigned Threat Intelligence (TI) Lookup platform.
The latest update introduces an enhanced home screen that integrates the powerful MITRE ATT&CK matrix, complete with interactive features, actionable insights, and connections to real-world malware samples and signatures.
The new features are set to help analysts, researchers, and incident responders streamline their workflows and respond to threats with greater precision and confidence.
ANY.RUN’s Black Friday offers: Get Up to 3 licenses as a gift
Redesigned Threat Intelligence Dashboard: A New Standard

The centerpiece of the redesigned TI Lookup is its fully interactive MITRE ATT&CK matrix, now displayed prominently on the home screen. This matrix doesn’t just present theoretical frameworks for tactics and techniques—it bridges the gap between these concepts and practical, real-world threat data.
Key Features of the New TI Lookup Dashboard
- Comprehensive Coverage: Unlike other platforms that display only a subset of techniques, TI Lookup includes all techniques detected on the platform.
- Interactive Insights: Clicking on any technique or tactic reveals detailed information about its use in real-world attacks, along with malware samples tied to the behavior.
- Actionable Layout: The matrix is organized for maximum clarity, showing clear connections between tactics, techniques, and actual malware.
Whether you’re a malware analyst, incident responder, or simply a researcher looking to understand attack patterns, the new dashboard is a highly functional tool designed to simplify complex threat intelligence tasks.
Collect threat intel on the latest malware and phishing attacks with TI Lookup – Get Upto 3 Free Licences
Making the MITRE ATT&CK Matrix Actionable
One of the primary goals of the redesign is to turn the MITRE ATT&CK matrix into a hands-on tool for analysts. Instead of just listing tactics and techniques, the enhanced platform connects these elements to detection data, attack patterns, and malware families.

How It Works:
- Detailed Connections: Techniques are linked to real-world examples of how attackers use them, helping analysts understand their practical implications.
- Behavioral Insights: Analysts can explore how specific techniques (e.g., spearphishing links) are implemented by attackers, gaining insights into their tactics, techniques, and procedures (TTPs).
- Better Detection: Security teams can fine-tune their detection rules by studying malware families and techniques tied to specific behaviors.
For instance, by analyzing the Phishing technique (T1566) within the Initial Access phase of the MITRE ATT&CK matrix, users can explore sub-techniques like spearphishing links, spearphishing attachments, and more. Each entry provides detailed signatures and examples pulled from real-world analysis sessions, offering invaluable insights into how attackers operate.
Filtering and Prioritization: Focus on What Matters
To help analysts prioritize critical threats, the redesigned TI Lookup introduces a color-coded filtering system for MITRE ATT&CK techniques:
- Red (Danger): High-risk techniques requiring immediate action.
- Yellow (Warning): Moderate-risk techniques that warrant ongoing analysis.
- Blue (Other): Low-risk or less urgent techniques.
Users can refine their view by toggling specific categories on or off, making it easier to focus on the most pressing threats.
For example, when analyzing spearphishing links, users can drill down into associated URLs, domains, and other Indicators of Compromise (IOCs).

Interactive Malware Analysis: Sandbox Integration
The revamped platform seamlessly integrates with ANY.RUN’s cloud-based interactive sandbox, allowing users to analyze malware samples in-depth. With one click, users can jump from the TI Lookup dashboard to a sandbox session, where they can observe malware behavior in real time and analyze its overall attack structure.
Key Benefits:
- Behavioral Analysis: Watch how malware interacts with systems, including file modifications, network connections, and registry changes.
- IOC Collection: Collect actionable Indicators of Compromise (IOCs) directly from sandbox sessions.
- Comprehensive Threat Context: Gain insights into the full lifecycle of an attack, from initial access to persistence and lateral movement.
This integration ensures analysts have all the tools they need to not only understand threats but also respond effectively.
Use Case Highlight: Spearphishing Links
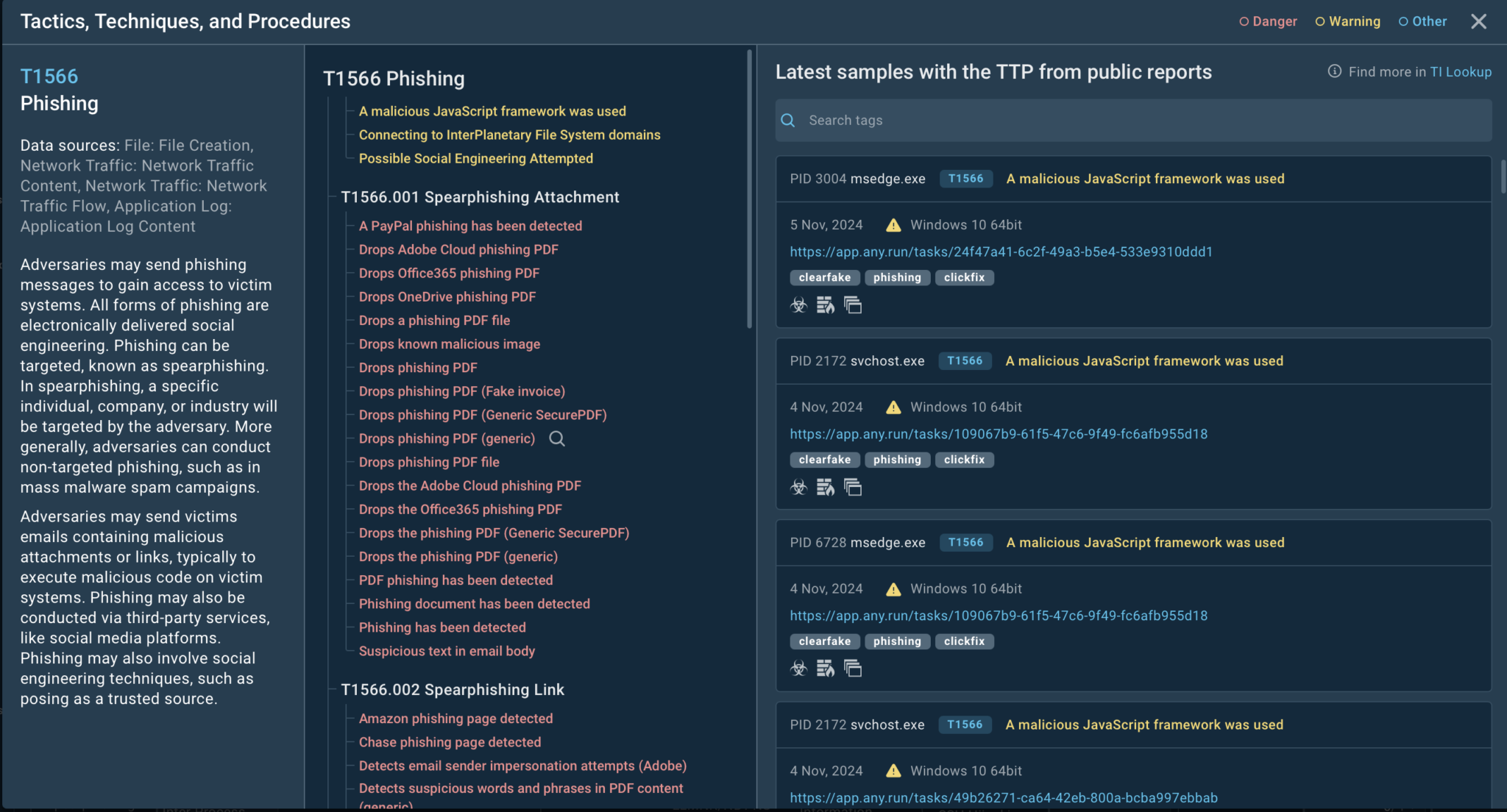
To illustrate the power of the new platform, consider the Spearphishing Links sub-technique within the MITRE ATT&CK matrix. Clicking on this entry reveals detailed information, including:
- Overview: A breakdown of spearphishing links, attachments, and similar techniques.
- Signatures: Real-world examples such as malicious QR codes or URLs identified in phishing attempts.
- Sandbox Links: Direct access to sandbox sessions showing how the technique was used in specific attacks.
According to the ANY.RUN report, By studying these insights, analysts can create tailored detection rules, enhance their defenses, and develop detailed reports for stakeholders. For example, they might uncover a phishing campaign leveraging malicious URLs embedded in emails, then use this information to prevent future attacks.
TI Lookup Search: A Treasure Trove of Threat Intel
The updated TI Lookup also features a dedicated search function for deeper exploration of threats. Users can search for specific techniques, malware families, or IOCs and access a wealth of actionable intelligence, including:
- Indicators of Compromise (IOCs): Domains, IPs, files, and URLs tied to specific threats.
- Indicators of Behavior (IOBs): Patterns of attack behavior.
- Indicators of Attack (IOAs): Evidence of how attackers execute their techniques.
For instance, searching for “Suspicious URL” might reveal phishing campaigns, malicious payloads, or other threats, providing analysts with the context needed to improve their defenses.
Why This Matters
The new features in TI Lookup are designed to address some of the most pressing challenges in cybersecurity:
- Enhanced Efficiency: By integrating actionable insights into an easy-to-use dashboard, analysts can save time and focus on high-priority threats.
- Deeper Insights: The connection between the MITRE ATT&CK matrix and real-world examples gives analysts a clearer understanding of how attackers operate.
- Improved Defense: Armed with detailed insights, security professionals can develop better detection rules and mitigation strategies.
About ANY.RUN
ANY.RUN is a leading provider of interactive cybersecurity tools, including its popular Threat Intelligence Lookup and YARA Search services. Known for their speed and precision, these tools empower analysts to stay ahead of emerging threats by providing detailed insights into malware behavior and attack patterns.
Ready to Transform Your Threat Intelligence Workflow?
Explore the redesigned Threat Intelligence Lookup today and experience firsthand how these updates can revolutionize your approach to cybersecurity.
Whether you’re defending against phishing attacks, studying persistence techniques, or analyzing lateral movement, TI Lookup provides everything you need to stay ahead.
Sign Up Intelligence Lookup for Fast Threat Investigations - Get Upto 3 Free Licences
