A few weeks ago we warned our readers of a phishing campaign targeting Instagram users that didn’t resort to the usual links to phishing websites, but used mailto: links instead. Now, it seems that these scammers have turned their attention to Facebook users.
It works like this: The target receives an email saying that your Facebook account was logged into from a new device. Even though the subject line says “We’ve Received a request to Reset your password for Facebook Account !”
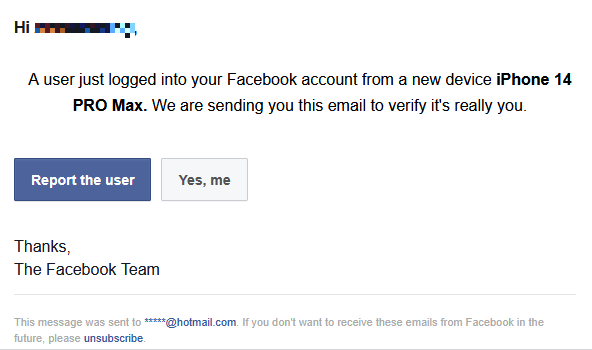
“A user just logged into your Facebook account from a new device iPhone 14 PRO Max. We are sending you this email to verify it’s really you.”
All the links you see in the email: “Report the user”, “Yes, me”, “unsubscribe”, and even the obfuscated email address at the bottom, do exactly the same thing.
They open your default email program with a pre-addressed message with a subject line that matches the button/text you clicked on.
The email addresses these messages will be sent to are the same as the ones we saw with the Instagram phish:
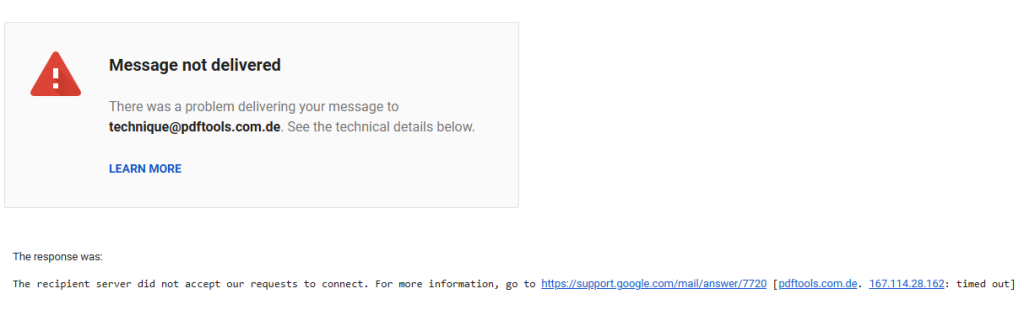
prestige@vacasa[.]uk.com(typosquat of vacasa.com vacation rentals)ministry@syntec[.]uk.com(typosquat of syntechnologies.co.uk hardware provider)technique@pdftools[.]com.de(typosquat of pdf-tools.com software provider)service@boss[.]eu.com(several possibilities)threaten@famy[.]in.net(science news site, possibly compromised)difficulty@blackdiamond[.]com.se(known malicious domain)anticipation@salomonshoes[.]us.com(typosquat of salomon.com running shoes)
This is kind of surprising since we found last time that several of the addresses were unresponsive.
The unusual Top-Level Domains (TLDs) like uk.com, com.de, eu.com, com.se, and us.com are actually second-level domain extensions operated by private entities, not official country-code top-level domains.
Though these domain extensions themselves are legitimate registration services, their openness and global accessibility mean they can be misused by phishers and other cybercriminals to make them look more legitimate or country-specific than generic .com domains. They may also be used to typosquat legitimate domains.
How to avoid Facebook phishing
Since we can expect to see more phishing campaigns that use mailto: links, here are some tips to avoid falling victim to such a scam.
- As with regular links, scrutinize the destination of an email link. Even if the domain looks legitimate, your Facebook account isn’t secured by a shoe maker or vacation provider, or someone using a gmail address. The email address should be one that belongs to Facebook or Meta.
- Remember that legitimate companies will not ask you to mail them your account details, credentials, or other sensitive information.
- If there’s an urgency to respond to an email, take a pause before you do. This is a classic scammer trick to get you to act before you can think.
- Don’t reply if the warning looks suspicious in any way. Sending an email will tell the phishers that your email address is active, and it will be targeted even more.
- Do an online search about the email you received, in case others are posting about similar scams.
- Use Malwarebytes Scam Guard to assess the message. It will tell you whether it’s a scam or give you tips how you can find out if it isn’t sure.
We don’t just report on threats – we help protect your social media
Cybersecurity risks should never spread beyond a headline. Protect your social media accounts by using Malwarebytes Identity Theft Protection.
