A malicious Android application has been uncovered, impersonating legitimate Indian banking apps to orchestrate credential theft, surveillance, and unauthorized financial transactions.
This malware employs a modular architecture featuring a dropper and a primary payload, leveraging deceptive user interfaces, silent installation techniques, and extensive abuse of Android permissions to evade detection and ensure persistence.
In-Depth Malware Analysis
Operating through Firebase for command-and-control (C2) operations, it deploys phishing pages that mimic authentic banking interfaces, tricking users into divulging sensitive data.
Static analysis of the dropper reveals permissions such as ACCESS_NETWORK_STATE for monitoring connectivity to facilitate stealthy data exfiltration, REQUEST_INSTALL_PACKAGES for prompting installations of secondary APKs without user awareness, and QUERY_ALL_PACKAGES for profiling installed apps to target banking software specifically.
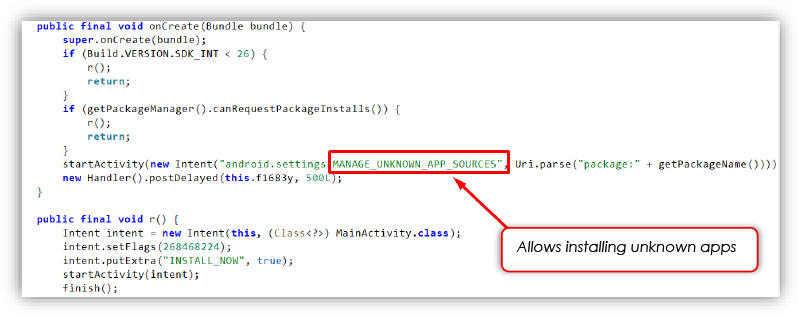
The dropper loads a hidden payload from its assets folder, writes it to external storage via FileProvider, and initiates installation using an INSTALL_NOW flag, bypassing app store scrutiny and enabling background deployment akin to tactics seen in advanced banking Trojans.
Delving deeper, the main payload requests permissions like READ_SMS, SEND_SMS, and RECEIVE_SMS to intercept and exfiltrate one-time passwords (OTPs) and two-factor authentication (2FA) codes, while REQUEST_IGNORE_BATTERY_OPTIMIZATIONS ensures uninterrupted background execution.
Additional permissions such as READ_PHONE_STATE and READ_PHONE_NUMBERS enable device fingerprinting, SIM data extraction including carrier names and phone numbers, and even call forwarding abuse via USSD codes like **21*number# to redirect calls to attacker-controlled numbers.
The payload hides from the app launcher by categorizing its activity as INFO, running silently without an icon, and utilizes modular classes like Account for credential harvesting, Debit for stealing card details (validating CVV as 3 digits, card numbers as 19 characters, and ATM PINs as 4 digits), and AutostartHelper for boot persistence via RECEIVE_BOOT_COMPLETED.
Data exfiltration occurs through Firebase Realtime Database, storing user IDs and intercepted SMS metadata such as sender, content, timestamp, and SIM slot in paths like user/
Dynamic analysis shows the dropper initiating with fake update popups to lure users into enabling ‘Install Unknown Apps,’ followed by the payload requesting SMS access and displaying phishing pages that enforce input validation (e.g., 10-digit phone numbers and 4-digit MPINs) to appear legitimate.
Firebase Cloud Messaging (FCM) facilitates remote command execution, including unauthorized calls and real-time SMS monitoring, with embedded keys for sender ID, API, and storage buckets enabling covert C2.
During the probe, the Firebase instance remained active but authentication-locked, underscoring its ongoing malicious use.
Evolving Threat Landscape
This malware, observed as early as April 3, 2025, exemplifies trends in mobile financial fraud, where cybercriminals clone app icons, names, and UIs to deceive users into granting high-risk permissions for OTP theft and 2FA bypass.
Delivery vectors include smishing via fake SMS links, email phishing with embedded APKs, WhatsApp bots, vishing calls posing as bank support, SEO-poisoned fake websites, malvertising in apps, trojanized utilities like QR scanners that drop payloads, QR/NFC attacks in public spaces, preloaded malware on counterfeit devices, and exploitation of vulnerabilities such as accessibility services or CVE-2025-27363 for silent installs and overlays.
This evasive banking Trojan highlights the need for layered defenses, including user education on permission risks, robust app vetting, and anomaly detection in financial ecosystems to combat such persistent threats.
Indicators of Compromise (IOCs)
| Indicator | Type | Remarks |
|---|---|---|
| ee8e4415eb568a88c3db36098b7ae8019f4efe565eb8abd2e7ebba1b9fb1347d | Sha256 | Base Payload or Dropper |
| 131d6ee4484ff3a38425e4bc5d6bd361dfb818fe2f460bf64c2e9ac956cfb13d | Sha256 | Main Payload |
Get Free Ultimate SOC Requirements Checklist Before you build, buy, or switch your SOC for 2025 - Download Now
