Competition between stealers for macOS is heating up, with a new malvertising campaign luring Mac users via a fraudulent advert for Microsoft Teams. This attack comes on the heels of the new Poseidon (OSX.RodStealer) project, another threat using a similar code base and delivery techniques.
Based on our tracking, Microsoft Teams is once again a popular keyword threat actors are bidding on, and it is the first time we have seen it used by Atomic Stealer. Communication tools like Zoom, Webex or Slack have been historically coveted by criminals who package them as fake installers laced with malware.
This latest malvertising campaign was running for at least a few days and used advanced filtering techniques that made it harder to detect. Once we were able to reproduce a full malware delivery chain, we immediately reported the ad to Google.
Top search result for Microsoft Teams
We were able to reliably search for and see the same malicious ad for Microsoft Teams which was likely paid for by a compromised Google ad account. For a couple of days, we could not see any malicious behavior as the ad redirected straight to Microsoft’s website. After numerous attempts and tweaks, we finally saw a full attack chain.
Despite showing the microsoft.com URL in the ad’s display URL, it has nothing to do with Microsoft at all. The advertiser is located in Hong Kong and runs close to a thousand unrelated ads.

Malicious redirect and payload
We confirmed the ad was indeed malicious by recording a network capture (see below). Each click is first profiled (smart[.]link) to ensure only real people (not bots, VPNs) proceed, followed by a cloaking domain (voipfaqs[.]com) separating the initial redirect from the malicious landing (decoy) page (teamsbusiness[.]org).
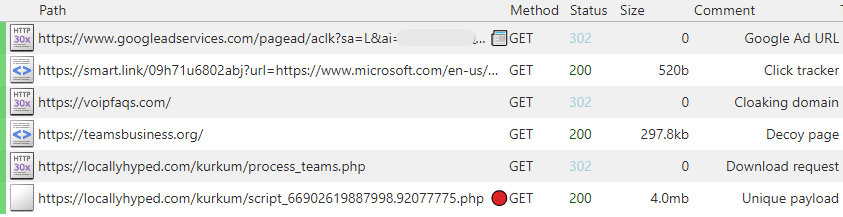
Victims land on a decoy page showing a button to download Teams. A request is made to a different domain (locallyhyped[.]com) where a unique payload (file name and size) is generated for each visitor.

Once the downloaded file MicrosoftTeams_v.(xx).dmg is mounted, users are instructed to open it via a right click in order to bypass Apple’s built-in protection mechanism for unsigned installers.
In the video below, we show the steps required to install this malicious application, noting that you are instructed to enter your password and grant access to the file system. This may not come as unusual for someone wanting to install a new program, but it is exactly what Atomic Stealer needs to grab keychain passwords and important files.
Following the data theft is the data exfiltration step, only visible via a network packet collection tool. A single POST request is made to a remote web server (147.45.43[.]136) with the data being encoded.

Mitigations
As cyber criminals ramp up their distribution campaigns, it becomes more dangerous to download applications via search engines. Users have to navigate between malvertising (sponsored results) and SEO poisoning (compromised websites).
To mitigate such risks, we recommend using browser protection tools that can block ads and malicious websites. Often times, threat actors will rely on redirects from ads or compromised networks that can be stopped before even downloading a malicious installer.

Malwarebytes for Mac detects this threat as OSX.AtomStealer:

Indicators of Compromise
Cloaking domain
voipfaqs[.]com
Decoy site
teamsbusiness[.]org
Download URL
locallyhyped[.]com/kurkum/script_66902619887998[.]92077775[.]php
Atomic Stealer payload
7120703c25575607c396391964814c0bd10811db47957750e11b97b9f3c36b5d
Atomic Stealer C2
147.45.43[.]136
