Malicious versions of at least 18 widely used npm packages were uploaded to the npm Registry on Monday, following the compromise of their maintainer’s account.
“The packages were updated to contain a piece of code that would be executed on the client of a website, which silently intercepts crypto and web3 activity in the browser, manipulates wallet interactions, and rewrites payment destinations so that funds and approvals are redirected to attacker-controlled accounts without any obvious signs to the user,” Aikido Security researcher Charlie Eriksen explained.
They started getting pushed to npm on September 8 around 13:15 UTC, and have been pulled after a couple of hours. Unfortunately, it also looks like other packages by other maintainers have also been compromised.
How this supply chain compromise unfolded
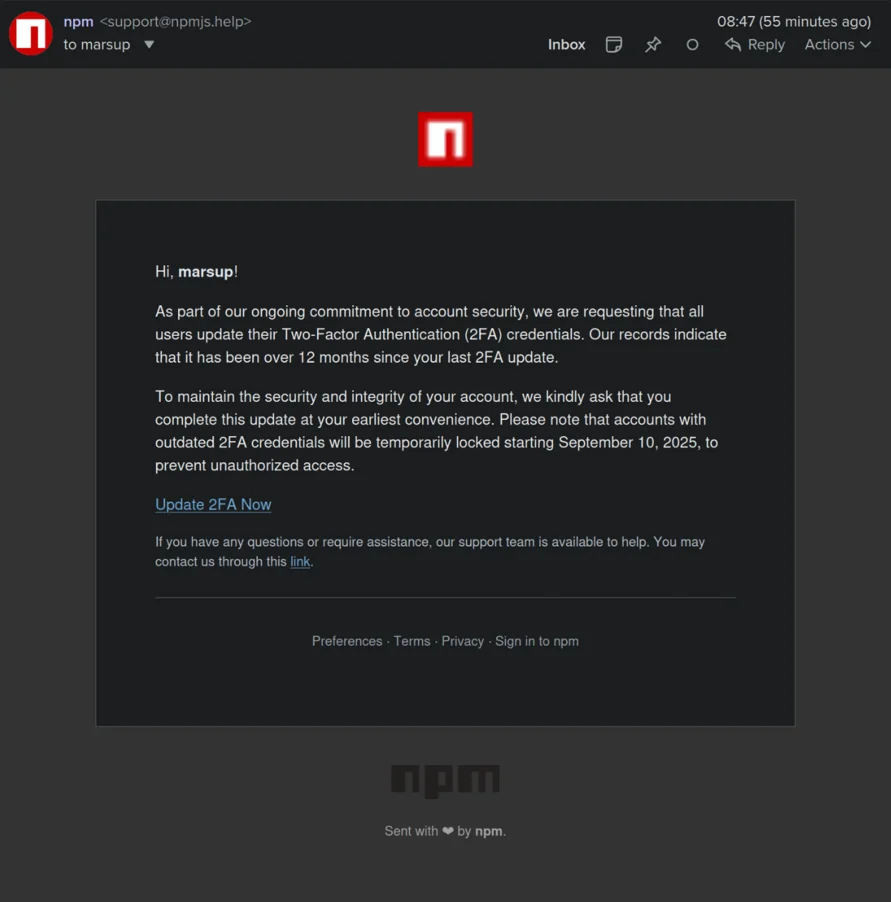
Josh Junon (handle: ~qix), the developer of the packages, admittedly fell for a phishing email impersonating the npm registry, asking him to update their two-factor authentication (2FA) credentials.
The phishing email (Source: Nicolas Morel, ~marsup)
(Other developers have been targeted with the same email, as well. According to Sonatype, four additional packages published by a separate maintainer also appear to be hijacked by the same threat actor.)
“[The] email came from support [@] npmjs [.] help. Looked legitimate at first glance,” Junon explained.
“Not making excuses, just had a long week and a panicky morning and was just trying to knock something off my list of to-dos. Made the mistake of clicking the link instead of going directly to the site like I normally would (since I was mobile).”
When he landed on the phishing site, it asked for his npm Registry login credentials and OTP (one-time password). “It even gave me a new TOTP key to add to authy, which worked. I assume this was either just keeping the facade up, or just because they had [Man-in-the-Middle]’d npm or something,” he noted.
Armed with the credentials and the one-time password, the threat actor logged into Junon’s npm account, changed the associated email (thus making it impossible for him to log in) and proceeded to pump out the malicious package versions:
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
The fallout
The malicious payload injects itself into the browser to intercept both web traffic and wallet activity; detects crypto transactions; and swaps the payment destinations to point to a wallet belonging to the threat actor.
“What makes [this malware] dangerous is that it operates at multiple layers: altering content shown on websites, tampering with API calls, and manipulating what users’ apps believe they are signing. Even if the interface looks correct, the underlying transaction can be redirected in the background,” Eriksen noted.
Software supply chain security company ReversingLabs says it has also discovered hundreds of packages on GitHub containing the malicious code associated with the attackers who targeted Junon. These are associated with many different developers.
“While the full extent of the hacks and affected packages have yet to be determined, security experts say that the vast reach of the affected packages will touch most developers,” the company added.
Collectively, Junon’s npm packages – i.e., bundles of reusable code for JavaScript or Node.js projects – have over 2 billion weekly downloads on the npm Registry, and they are implemented in a great number of apps. Which apps have ended up incorporating the compromised packages is currently unknown, though.
“What we are seeing unfold with the npm packages chalk and debug is an unfortunately common instance today in the software supply chain,” noted Ilkka Turunen, Field CTO at Sonatype.
“The malicious payload was focused on crypto theft, but this takeover follows a classic attack that is now established — by taking over popular open source packages, adversaries can steal secrets, leave behind backdoors and infiltrate organisations. Package takeovers are now a standard tactic for advanced persistent threat groups like Lazarus, because they know they can reach a large amount of the world’s developer population by infiltrating a single under-resourced project.”
Turunen has urged organizations to investigate their SBOMs for the affected package versions and to treat any machine found with them as compromised.
“Open source repository managers (such as npm, pip, docker) are relied upon for a huge range of applications, and their ubiquity makes them an appealing target. Luckily, in this instance the affected packages were fixed within hours, and the risk of pulling an impacted package was low,” commented Nathan Webb, Principal Consultant at Acumen Cyber.
“This attack represents a good example of why companies need to audit their software dependencies, and it acts as a reminder for companies to review their capabilities when it comes to detecting malicious dependencies: NPM, for example, has a built in ‘npm-audit’ command that that can be used to automatically calculate and fix at least some vulnerabilities. Companies ultimately need to be accountable for checking the security of the packages they use, and they should implement checks like these into their build pipelines.”
As security researcher Kevin Beaumont noted, this attack could have had worse consequences if the attacker had concentrated on something other than crypto theft.
“Imagine if they had done reverse shells instead, or automated lateral movement to ransomware deployment NotPetya style. The thing that saved companies here was the threat actor was incompetent crypto boy, nothing more,” he commented.
Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!