The FBI has seized the notorious RAMP cybercrime forum, a platform used to advertise a wide range of malware and hacking services, and one of the few remaining forums that openly allowed the promotion of ransomware operations.
Both the forum’s Tor site and its clearnet domain, ramp4u[.]io, now display a seizure notice stating, “The Federal Bureau of Investigation has seized RAMP.”
“This action has been taken in coordination with the United States Attorney’s Office for the Southern District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice,” the notice reads.

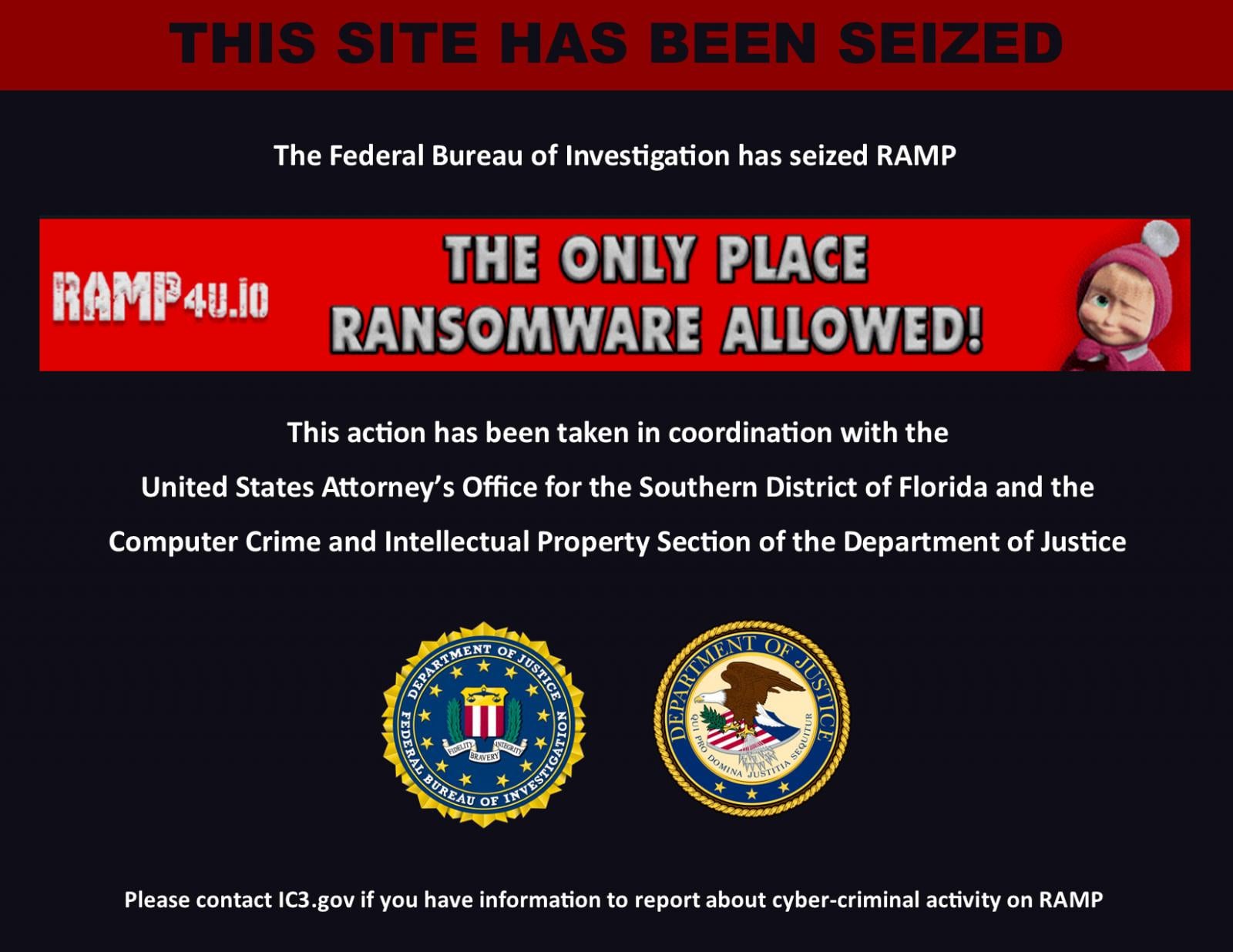
The seizure banner also appears to taunt the forum’s operators by displaying RAMP’s own slogan: “THE ONLY PLACE RANSOMWARE ALLOWED!,” followed by a winking Masha from the popular Russian “Masha and the Bear” kid’s cartoon.
While there has been no official announcement by law enforcement regarding this seizure, the domain name servers have now been switched to those used by the FBI when seizing domains:
Name Server: ns1.fbi.seized.gov
Name Server: ns2.fbi.seized.gov
If so, law enforcement now has access to a significant amount of data tied to the forum’s users, including email addresses, IP addresses, private messages, and other potentially incriminating information.
For threat actors who failed to follow proper operational security (opsec), this could lead to identification and arrests.
BleepingComputer contacted the FBI with question regarding the seizure and will update this story if we receive a response.
The RAMP cybercrime forum
The RAMP cybercrime forum launched in July 2021, following the banning of the promotion of ransomware operations by popular Russian-speaking Exploit and XSS hacking forums.
This ban was due to heightened pressure from Western law enforcement following the DarkSide ransomware attack on Colonial Pipeline.
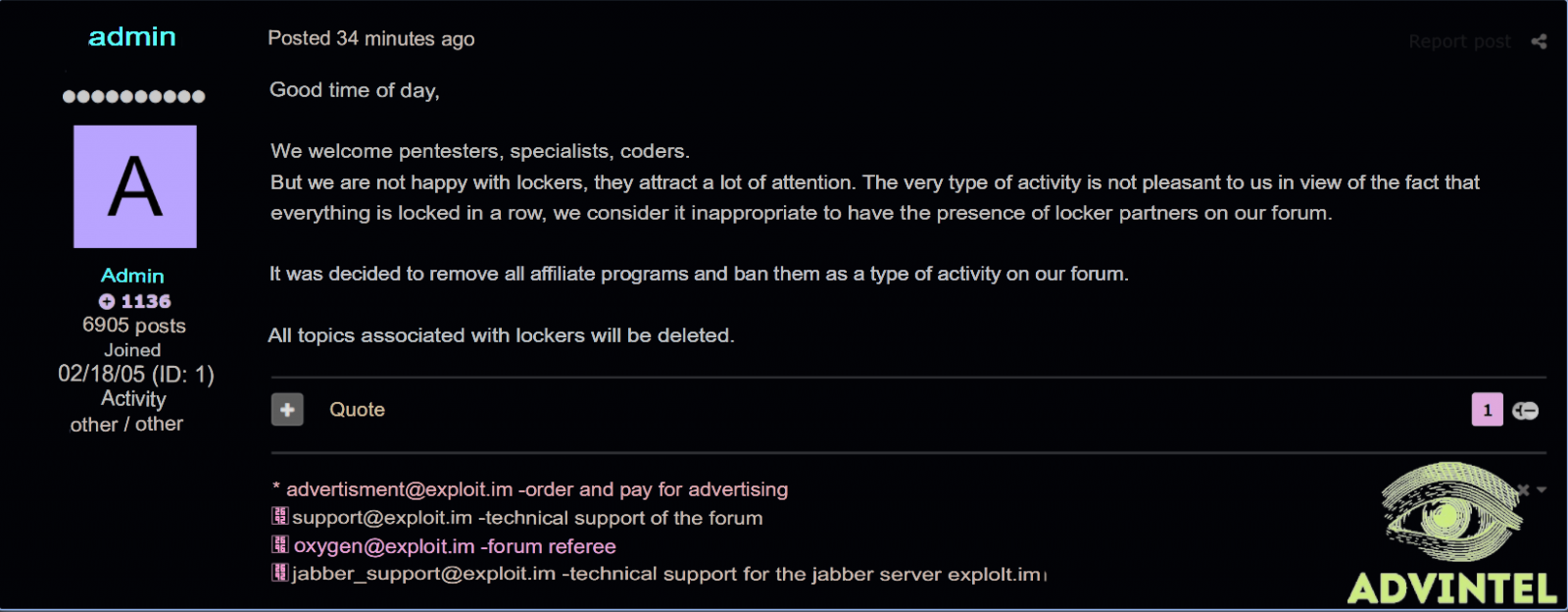
In July 2021, a new Russian-speaking forum called RAMP launched, promoting itself as one of the last remaining places where ransomware could be openly promoted. This led to multiple ransomware gangs using the forum to promote their operations, recruit affiliates, and buy and sell access to networks.
RAMP was launched by a threat actor known as Orange, who also operated under the aliases Wazawaka and BorisElcin.
Orange was previously the administrator of the Babuk ransomware operation, which shut down after its ransomware attack on the D.C. Metropolitan Police Department.
Internal disputes allegedly erupted within the group over whether stolen law enforcement data should be publicly leaked, and after the data was leaked, the group splintered.
Following the split, Orange launched the RAMP forum on a Tor onion domain that Babuk had previously used.
Soon after its launch, RAMP experienced distributed denial-of-service (DDoS) attacks that disrupted its availability. Orange publicly blamed former Babuk partners for the attacks, though the previous members denied responsibility to BleepingComputer, stating they had no interest in the forum.
The individual behind the Orange and Wazawaka aliases was later publicly identified by cybersecurity journalist Brian Krebs as Russian national Mikhail Matveev.
In an interview with Recorded Future’s Dmitry Smilyanets, Matveev confirmed that he previously operated under the alias Orange and that he created RAMP using the former Babuk onion domain.
Matveev explained that the forum was initially created to repurpose Babuk’s existing infrastructure and traffic. He claimed that RAMP ultimately generated no profit and was subjected to constant DDoS attacks, which led him to step away from managing it after it gained popularity.
In 2023, Matveev was indicted by the U.S. Department of Justice for his involvement in multiple ransomware operations, including Babuk, LockBit, and Hive, which targeted U.S. healthcare organizations, law enforcement agencies, and other critical infrastructure.
He was also sanctioned by the U.S. Treasury’s Office of Foreign Assets Control and placed on the FBI’s most-wanted list, with the U.S. State Department offering a reward of up to $10 million for information leading to his arrest or conviction.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.




