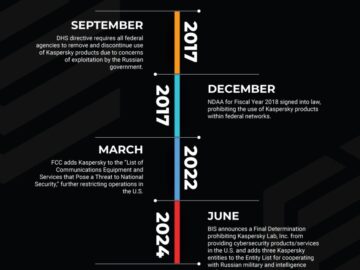
Ransomware attacks set a single-month record in February that was well above previous highs, according to a Cyble threat intelligence report.
The Cyble report measured the number of victims claimed by ransomware groups on their Tor-based data leak sites (DLS), which the groups use as part of their extortion tactics by “naming and shaming” victims and threatening to release data unless ransom demands are paid. While not all ransomware victims are included on DLS sites, Cyble said it’s a useful indicator for analyzing ransomware trends.
The record ransomware attacks seen in February 2025 were more than 50% higher than the previous record set two years ago, Cyble said.
CL0P Sends Ransomware Attacks to Record Highs
Cyble said the previous high for ransomware attacks was set in May 2023, when 544 victims were claimed by ransomware groups.
February’s numbers would have eclipsed that record even without the CL0P ransomware group’s 267 victims, but with the CL0P victims, the total number of victims claimed by ransomware groups in February hit 821, far beyond previous highs (image below).

CL0P has now claimed 386 victims from its exploitation of Cleo MFT vulnerabilities, Cyble said. The high number of victim claims made CL0P the most active ransomware group for the month, followed by RansomHub and Akira (chart below).


The U.S. far outpaced other nations in ransomware victims, with 10 times more victims than second-place Canada (chart below).


Are Record Ransomware Attacks the Start of a New Trend?
While February’s record ransomware victims were well above long-term trends, Cyble questioned whether that surge is the start of a new higher level of ransomware attacks. The threat intelligence company looked at the major ransomware players for clues.
Looking at the last four years, LockBit has been well ahead of other ransomware groups, claiming more than 2,700 victims (chart below). However, LockBit has fallen off considerably in the last year after being hit by global law enforcement actions and is in the process of attempting a comeback with LockBit 4.0.


CL0P came in a distant second with 901 claimed victims over that four-year period, with Play, RansomHub, Conti and Akira (608 victims) the next most active ransomware groups.
Six-year-old CL0P has largely focused on managed file transfer (MFT) vulnerabilities like Cleo and MOVEit, which has tended to make the group’s victims more clustered, with more than 40% of those victims (383) coming just in the last few months. With only 22 additional CL0P victims in the last year, “it would be reasonable to assume that CL0P victim totals will continue to fluctuate over time,” Cyble said.
But with RansomHub, Akira, Play and FOG also increasing ransomware activity in recent months, “it’s possible that we’ve entered a higher range of claimed victims by ransomware groups,” the report noted.
Cyble said organizations should focus on measures that improve cyber resilience and limit lateral movement, such as patching web-facing vulnerabilities, training employees to recognize phishing attempts, and implementing zero trust, network segmentation and monitoring, and ransomware-resistant backups.