Windows Active Directory (AD) service accounts are prime cyber-attack targets due to their elevated privileges and automated/continuous access to important systems. Windows Administrators should therefore implement strong security measures crucial for protecting AD environments from security compromises.
This article outlines five best practices to help secure your AD service accounts and reduce the risk of compromise by malicious actors.
What are service accounts?
AD service accounts are specialized accounts designed for running applications and services on Windows Servers. To support software-specific functions, service accounts require elevated permissions to manage the installation of applications and core services, and are often granted extensive access to the operating system infrastructure for dependent applications to function properly.
This expansive access level makes service accounts especially attractive targets for malicious actors looking to gain a foothold into critical systems.
By compromising a service account, attackers can often gain broad access across the network and visibility into other privileged systems.
Service account types
Service accounts come in three types: local user accounts, domain user accounts, managed services accounts (MSAs), and group managed service accounts (gMSAs).
Local user accounts
Local user accounts can log into a Windows system and access its resources and settings. Local user account types include:
- System accounts – have local, multi-privilege administration permissions
- Local service accounts – have credential-less access to network services
- Network service accounts – have more robust, credentialed access to network services
Domain user accounts
Services running under a domain user account have all the local and network access granted to the account (or to any groups the account is a member of), with full access to the service security features of Windows and Microsoft AD Domain Services.
Managed service accounts
Managed service accounts (MSAs) are accounts tied to specific systems that you can use to securely run services, applications, and schedule tasks in the system’s AD domain. Because they use strict permissions controls via AD like role-based access control (RBAC) and maintenance automations, MSAs are considered the most secure service account type.
Group managed service accounts
The gMSA is a domain account that provides the same functionality as an MSA, but over multiple servers or services.
gMSAs provide more security features than traditional managed service accounts such as automatic password management and simplified service principal name (SPN) management, to include management delegation to other administrators.
The importance of protecting service accounts
Windows Administrators should prioritize service account protection, as cyber attackers commonly look to service accounts as a potential point of entry into protected systems.
For example, Storm-0501 ransomware attackers exploit over-privileged accounts when moving from organizations’ on-premises environments to cloud environments.
This allows them to gain network control, create persistent backdoor access to cloud environments, and deploy ransomware to the on-premises systems.
Five best practices for securing AD service accounts
1. Follow the Principle of Least Privilege
When configuring service accounts, you should follow the principle of least privilege—that is, users and accounts should only have the minimum set of privileges required to perform their tasks. AD service accounts are designed to perform specific tasks and should therefore only possess the necessary permission to complete those tasks.
By granting excessive privileges (e.g., making a service account a domain or enterprise administrator), you introduce significant risk into your Windows environment.
2. Use multi-factor authentication (MFA) wherever possible
Implementing MFA for all user accounts significantly enhances the security of your AD environment. Although service accounts are not usually intended for interactive logins that support MFA, it is essential to incorporate MFA into the interactive login processes of any service accounts that do.
3. Remove service accounts not in use
AD service accounts should be part of an active lifecycle management program, with any unused or unnecessary service accounts promptly disabled or flagged for attention. Interested to know how many unused service accounts you have in your AD?
Scan your AD with our free, read-only auditing tool and get an exportable report regarding inactive accounts and other password-related vulnerabilities. Download Specops Password Auditor here.
4. Monitor service account activity
AD service accounts are prime targets for attackers and should be monitored closely for suspicious activity and anomalies (e.g., unauthorized RDP access or use on inappropriate servers or workstations).
For auditing, Windows administrators should use a combination of native AD tools and third party tools to track logon events and account changes.
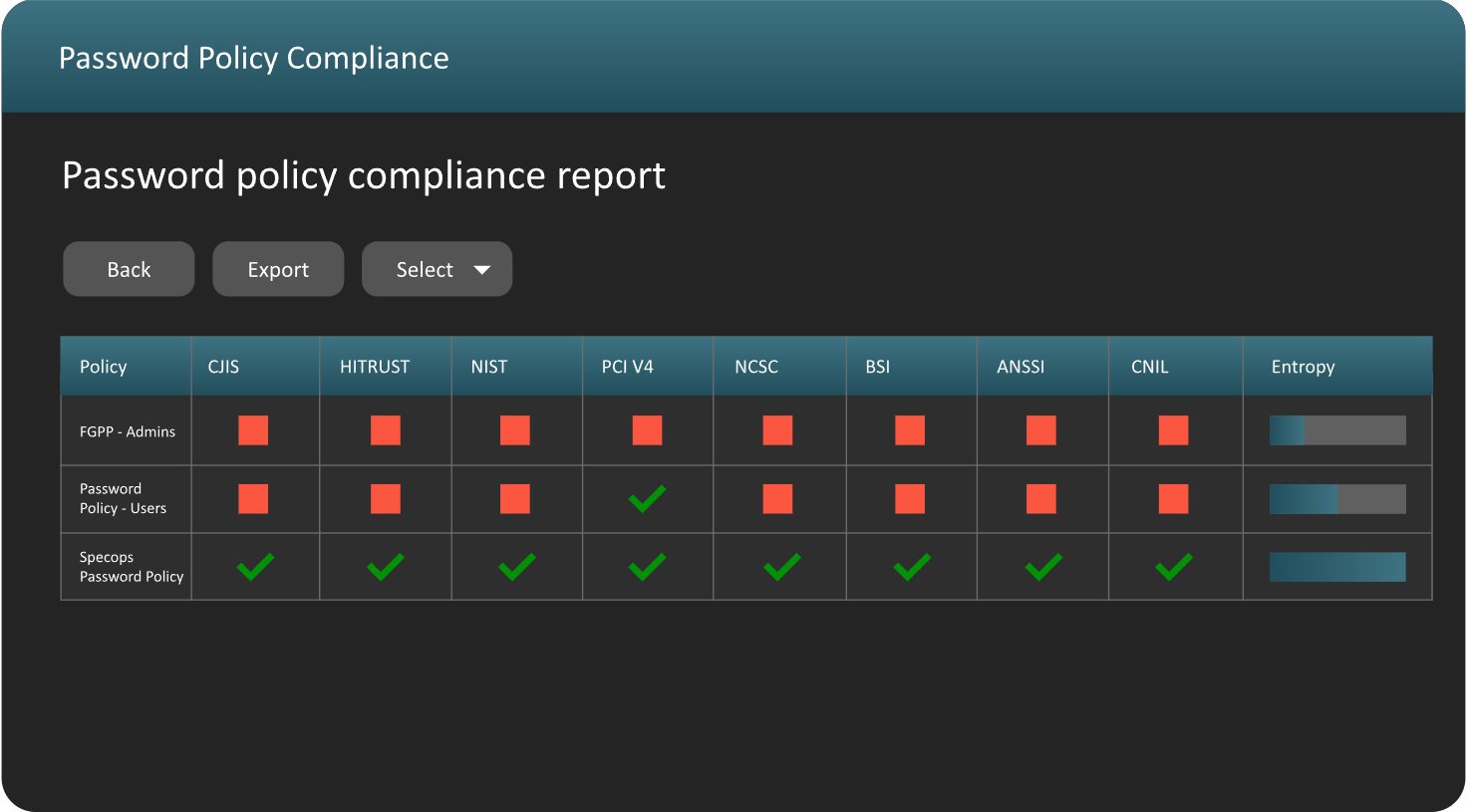
5. Enforce robust password policies across the organization
Although MSAs and gMSAs automate password management, implementing a robust password policy across all accounts, including user accounts, enhances the overall security of your AD Domain Services.
A third party tool such as Specops Password Policy can help you scale and enforce these policies across your organization, as well as continuously scanning your AD for breached passwords. Try Specops Password Policy for free.
Making service account protection a priority
AD service accounts are essential for running automated processes and services but can pose significant security risks due to their elevated privileges. If compromised, they can allow attackers to escalate control, disrupt operations, access sensitive data, and move laterally within the network.
By following these five best practices, you can mitigate these risks and better protect your IT environment against AD service account-related compromises.
Aiming to secure your Active Directory in 2025? Speak to a Specops expert.
Sponsored and written by Specops Software.
