When Atlassian Companion is installed on macOS, a vulnerability has been detected that enables remote code execution on users’ computers when they click the Edit button on a Confluence page.
With the Atlassian Companion app, users can edit Confluence files in their chosen desktop app and have the changes instantly saved back to Confluence.
.png
)
The Atlassian Companion software, which must be installed on each user’s computer, manages the download and re-upload of files.
An attacker can remotely execute malicious code on a computer via remote code execution (RCE) assaults. An RCE vulnerability can result in malware execution or an attacker acquiring complete control of a vulnerable system.
This flaw was discovered by blogger and app security expert WOJCIECH REGUA.
Remote Code Execution On MacOS Machine
The security expert says that documents saved in Confluence may be edited on macOS using the Atlassian Companion App. When the user presses the Edit button, the following happens:
- The file is downloaded locally on the computer.
- The app validates extensions
- The app opens the downloaded document
- When the document is updated, it is posted back to Confluence.
The issue here is that Atlassian was aware that some of the extensions needed to be disabled. A blocklist may be found in the app’s sources.
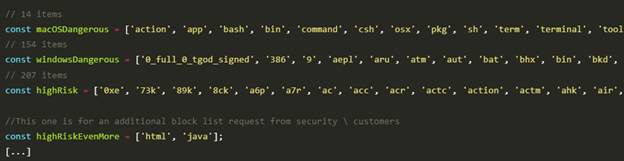
He mentions that the class extension is only on the windowsDangerous blocklist in this case; therefore, it is an allowed extension on macOS.
The researcher created a malicious Hello.java file when the researcher’s Hello.class file gets uploaded to Confluence and then clicks edit, the code is performed, and the Calculator is launched.

Finally, the mentioned. class file extension is now also blocked on macOS. Reports say Atlassian received the issue report in 2021, fixed the flaw in 90 days, and awarded a reward.
“AI-based email security measures Protect your business From Email Threats!” – Request a Free Demo.
